💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Here's what security teams need to know about the new Biden-Harris National Cybersecurity Strategy | Wiz Blog
The blog post discusses the new Biden-Harris National Cybersecurity Strategy and how security teams can benefit from it.
#cloud #security #softcorpremium
Celebrating Australia’s Privacy Awareness Week 2023
Cloudflare is proud to sponsor Australia’s Privacy Awareness Week 2023, which focuses on the theme of “Privacy 101: Back to Basics”. The blog post highlights the importance of new privacy basics, including the use of security solutions and privacy-enhancing technologies to protect sensitive personal data. Cloudflare is committed to supporting individuals and organizations in Australia and New Zealand to achieve this goal. The post also mentions the Australian Attorney General’s Privacy Act Review Report 2022, which calls for changes to Australia’s privacy regulations.
#PrivacyAwarenessWeek #PrivacyBasics #DataPrivacyProtection #softcorpremium
Using Microsoft Intune for Local Administrator Password Management - Microsoft Community Hub
This blog post discusses the use of Microsoft Intune for Local Administrator Password Management. The post explains the importance of managing local admin passwords, the limitations of traditional methods, and how Intune can help manage these passwords more effectively. It also provides step-by-step instructions on how to configure Intune for Local Administrator Password Management and some best practices for using this feature. Overall, the post aims to help organizations improve their security posture by managing local admin passwords in a more secure and efficient way.
#MicrosoftIntune #LocalAdministratorPasswordManagement #softcorpremium
Azure AD Certificate-Based Authentication (CBA) on Mobile now Generally Available! - Microsoft Community Hub
Microsoft has announced the general availability of Azure AD Certificate-Based Authentication (CBA) on mobile devices. This feature allows organizations to authenticate mobile devices using digital certificates instead of relying on usernames and passwords, providing an added layer of security.
#AzureAD #CBA #mobile #softcorpremium
Creating custom recommendations & standards for AWS/GCP workloads with Microsoft Defender for Cloud - Microsoft Community Hub
This blog post discusses how Microsoft Defender for Cloud can be used to create custom recommendations and standards for AWS/GCP workloads. The post highlights the importance of cloud security and how Microsoft Defender can help protect against threats and vulnerabilities. It also provides information on how to manage and monitor cloud workloads to ensure compliance with industry standards.
#AWS #GCP #MicrosoftDefender #cloudsecurity #softcorpremium
Email Protection Basics in Microsoft 365: Anti-malware, Safe Attachments, and Quarantine - Microsoft Community Hub
This blog post discusses the basics of email protection in Microsoft 365, covering anti-malware, safe attachments, and quarantine. The article explains how to use these features to prevent malicious emails from being delivered to your inbox and how to identify and handle them if they do get through. It also provides links to additional resources for more in-depth information on the topic.
#Microsoft365 #emailprotection #antimalware #softcorpremium
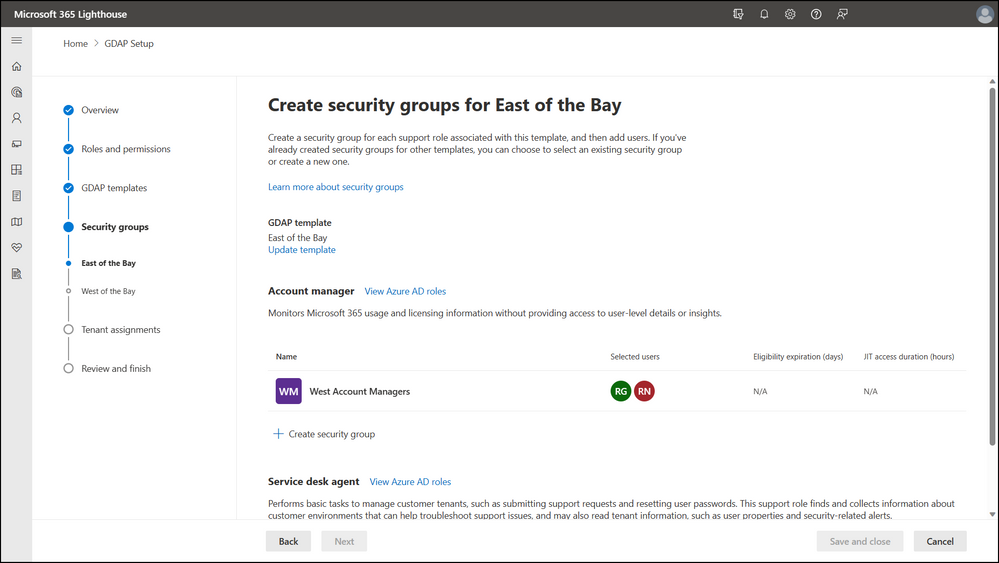
Set up GDAP
The blog post discusses the use of optional cookies on their website and how they improve the user experience through social media connections and personalized advertising based on online activity. It also provides the option for users to reject optional cookies, and only use the necessary ones for service provision. The post concludes by advising users to manage cookies and provides links to several Microsoft Tech Community Hubs and resources.
#GDAP #cookies #privacy #softcorpremium
Introducing the release of Attack Simulation Training Write API functionality (available in beta) - Microsoft Community Hub
Microsoft has announced the release of the Attack Simulation Training Write API functionality, which is available in beta. The API will allow users to create attack simulations and customize them to meet specific needs. It will also enable users to get detailed reports on the effectiveness of their security controls and how they can be improved. This development is a significant step in empowering security teams and improving their response to potential cyber threats.
#Microsoft #API #beta #softcorpremium
Get details on security finding changes with the new Finding History feature in Security Hub | AWS Security Blog
The AWS Security Blog highlights the new Finding History feature in Security Hub that provides details on security finding changes. The blog post explains how the feature works, its benefits and how it can be used for security investigations. It also includes a step-by-step guide on how to enable and use the feature on Security Hub. Overall, the post provides valuable insights for security professionals on how to better manage and track their security findings.
#SecurityHub #FindingHistory #softcorpremium
Improve Your Security Posture with Claroty xDome Integration with AWS Security Hub | AWS Partner Network (APN) Blog
The Claroty xDome integration with AWS Security Hub helps improve security posture by enabling users to detect and respond to potential threats in industrial networks. This integration allows users to view security alerts and insights from both their IT and OT environments in a single dashboard, making it easier to identify and prioritize incidents. The post also highlights the benefits of utilizing the AWS Partner Network (APN) for security solutions.
#ClarotyxDome #AWS #security #softcorpremium
How to monitor the expiration of SAML identity provider certificates in an Amazon Cognito user pool | AWS Security Blog
This blog post discusses how to monitor the expiration of SAML identity provider certificates in an Amazon Cognito user pool. It provides an overview of SAML and Cognito, explains the importance of monitoring certificate expiration, and offers step-by-step instructions on how to set up monitoring using Amazon CloudWatch, AWS Lambda, and Amazon SNS. This post is a valuable resource for anyone using Amazon Cognito user pools and looking to maintain secure and reliable access control for their applications.
#AmazonCognito #SAML #softcorpremium
ChatGPT returns to Italy after OpenAI tweaks privacy disclosures, controls | CSO Online
ChatGPT, the AI language model, is now available to users in Italy after being temporarily banned due to possible violations of the General Data Protection Regulation (GDPR). OpenAI made changes to its privacy disclosures and controls to comply with Italian regulators. ChatGPT had faced scrutiny over the collection and storage of personal data. The ban was lifted after the Italian data privacy authority found the AI model to be in compliance with GDPR regulations.
#ChatGPT #privacy #Italy #softcorpremium
Microsoft patches 3 vulnerabilities in Azure API Management | CSO Online
Microsoft has released a patch for three vulnerabilities in the Azure API Management service, which includes two Server-Side Request Forgery (SSRF) vulnerabilities and a file upload path traversal on an internal Azure workload. These vulnerabilities could allow a malicious actor to execute arbitrary code or perform unauthorized actions within a user's Azure environment. This patch is an important update for Azure users to ensure the security and integrity of their cloud infrastructure.
#Microsoft #Azure #security #softcorpremium
Re-encrypting an EC2 Instance With Your Own CMK | by Teri Radichel | Cloud Security | May, 2023 | Medium
In this post, Teri Radichel explains how to change the encryption key for an Amazon Machine Image (AMI) in order to regain control over the key policy and rotation schedule. By sharing an encrypted AMI, it's possible to end up with an AWS-managed key, which poses a security risk. The post provides a step-by-step guide for re-encrypting an EC2 instance with a custom KMS key, allowing users to control the key policy and share the AMI with multiple accounts.
#EC2 #CMK #encryption #softcorpremium
Is misinformation the newest malware? | CSO Online
The blog post discusses how misinformation and cybersecurity incidents have become the top scourges of the modern digital era. It highlights the prevalence of damaging misinformation threats, ransomware attacks, and other malicious cyber activities. The author suggests that misinformation is becoming the newest form of malware, and it is important to be aware of the risks and take necessary measures to protect oneself from such threats.
#misinformation #cybersecurity #ransomware #softcorpremium
Kaspersky probes ChatGPT’s ability to fight cyber scam - Back End News
Kaspersky recently conducted an experiment to check ChatGPT's cybersecurity knowledge and ability to detect phishing links. The study revealed that although ChatGPT knows a great deal about phishing and can guess the target of a phishing attack, it had high false positive rates of up to 64%. The experiment was based on asking ChatGPT two questions: 1. Does this link lead to a phishing website? 2. Is this link safe to visit?
#cybersecurity #AI #phishing #softcorpremium
The hidden security risks in tech layoffs and how to mitigate them | CSO Online
The blog post discusses the hidden security risks associated with tech layoffs and offers advice on how to mitigate these risks. It warns of the potential for malicious behavior from employees who have been laid off, such as locking organizations out of their own IT environment or selling data. The post emphasizes the importance of having a thorough offboarding process in place, including revoking access to systems and data, conducting exit interviews, and monitoring for unusual activity after the employee has left. Overall, the post highlights the need for companies to prioritize security in all aspects of their operations, even in the midst of personnel changes.
#security #offboarding #mitigation #softcorpremium #softcorpremium
White House unveils AI rules to address safety and privacy | Computerworld
The White House has unveiled new AI rules to address safety and privacy concerns around generative AI. The Biden administration is taking this step as generative AI has been advancing at a rapid pace, and there are risks surrounding it. The rules aim to ensure the ethical use of AI and protect privacy, civil rights, and human dignity. The move follows similar efforts by European regulators to rein in AI.
#AI #privacy #safety #softcorpremium
Cybercrime group FIN7 targets Veeam backup servers | CSO Online
Cybercrime group FIN7 is targeting Veeam Backup & Replication servers and deploying malware on them. Researchers from cybersecurity firm WithSecure investigated two such compromises so far, dating from late March.
#FIN7 #Veeam #cybersecurity #softcorpremium
Orca integrates cloud app security platform with GPT-4 | CSO Online
Orca Security, an agentless cloud security provider, has integrated Microsoft Azure OpenAI GPT-4 into its cloud-native application protection platform (CNAPP) under the ChatGPT implementation program. This integration will enable Orca Security to enhance its cloud app security platform by leveraging GPT-4's AI capabilities to identify and mitigate potential security threats.
#OrcaSecurity #ChatGPT #MicrosoftAzure #CNAPP #softcorpremium
Samsung bans staff AI use over data leak concerns | CSO Online
Samsung has banned employee use of AI tools, like generative AI ChatGPT, in an attempt to prevent sensitive internal data transmission to external servers. The electronics giant issued a memo to a key division notifying employees not to use AI tools until the data leak issue is resolved.
#Samsung #AI #dataleak #softcorpremium
White House seeks information on tools used for automated employee surveillance | Computerworld
The White House Office of Science and Technology Policy (OSTP) announced that they will soon release a public request for information (RFI) to learn more about the automated tools employers use to surveil, monitor, evaluate, and manage workers. The aim is to gather information about these tools and understand how they impact the privacy and civil liberties of employees. This move is a step towards ensuring that employee surveillance is done in a responsible and ethical way.
#employeeSurveillance #WhiteHouse #RFI #softcorpremium
11 security tools all remote employees should have | CSO Online
The blog post talks about 11 essential security tools that remote employees should have to protect their systems and data. The author highlights the importance of using VPNs, password managers, and multi-factor authentication. The post also recommends using encrypted messaging and email services and keeping software up to date. Other tools mentioned in the post include firewalls, anti-malware software, and intrusion detection systems. The author emphasizes the need for remote workers to be vigilant and proactive in protecting themselves and their companies from cyber threats.
#remotework #securitytools #softcorpremium
Apple Debuts Its Rapid Response Security Update Approach
Apple has introduced a new rapid response security update approach that allows them to distribute security updates faster and more efficiently. The new approach is designed to mitigate the risk of vulnerabilities being exploited before a patch can be released. This blog post provides insight into Apple's security strategy and highlights the importance of timely security updates for all users to ensure protection against potential threats.
#security #vulnerabilitymanagement #softcorpremium
FBI Focuses on Cybersecurity With $90M Budget Request
The FBI has requested a $90M budget increase for cybersecurity efforts. With the rise of cyberattacks in recent years, the FBI is placing a greater emphasis on protecting against them. The funds will be used to enhance the agency's cyber capabilities, including hiring more personnel and investing in new technology. This move highlights the growing importance of cybersecurity in today's digital landscape and the need for increased resources to combat evolving threats.
#cybersecurity #FBI #budgetrequest #softcorpremium