💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
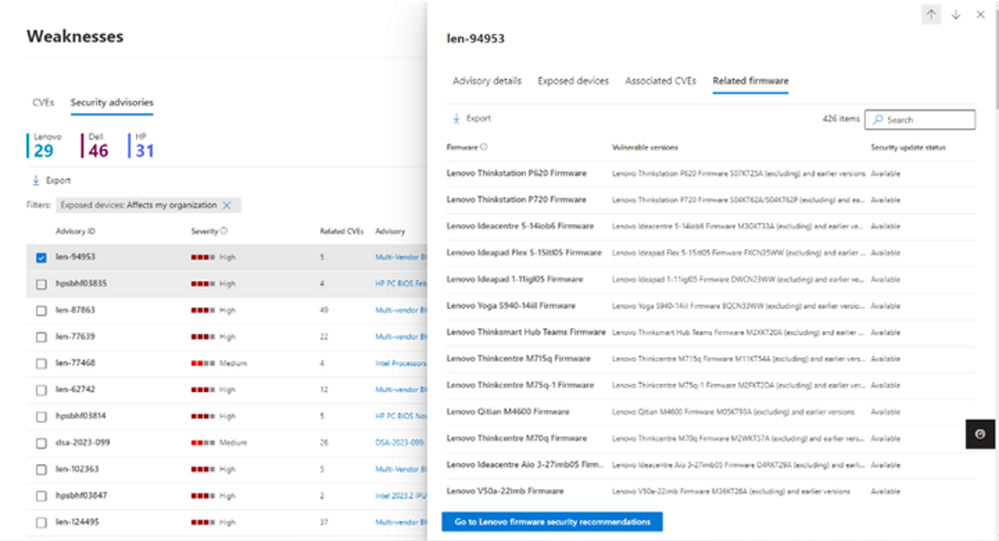
Microsoft Defender Vulnerability Management – Firmware Security Advisories - Microsoft Community Hub
Microsoft Defender Vulnerability Management has introduced a new capability called 'Firmware Security Advisories' that allows users to view, track, and monitor firmware vulnerabilities more efficiently. This is crucial in today's rapidly evolving threat landscape where firmware vulnerabilities can be exploited by attackers. The capability provides details on affected devices and software versions, instructions for updating firmware, and steps to mitigate risks. Users can also check if their organization is affected by specific security advisories. Currently, supported vendors include Lenovo, Dell, and HP. To learn more, users can take advantage of Microsoft Defender Vulnerability Management's free 90-day trial and access additional information on their website. Feedback can be shared directly with the team.
#FirmwareSecurityAdvisories #VulnerabilityManagement #MicrosoftDefender #softcorpremium
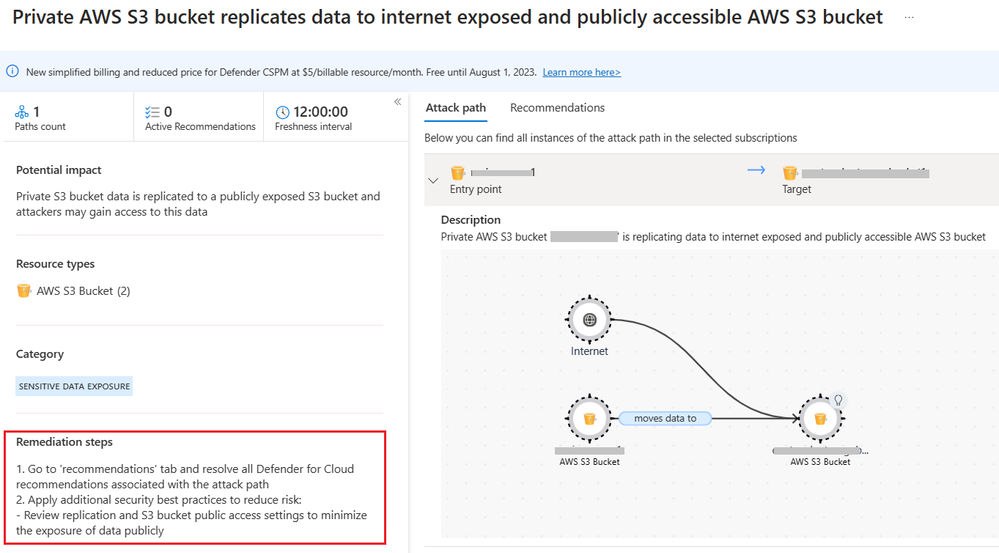
CSPM for AWS
Cloud misconfigurations are a common entry point for attackers, leaving cloud resources vulnerable to exploitation. Microsoft Defender for Cloud offers proactive security management to identify and prevent risks in AWS environments. It uses attack path analysis to detect misconfigurations and provides insights and remediation steps. Scenarios include a misconfigured S3 bucket, over-permissioning with IAM roles, and an EC2 instance with high severity vulnerabilities. By incorporating attack path analysis into security strategies, teams can stay ahead of potential misconfigurations and maintain a strong security posture.
#CloudSecurity #ProactiveProtection #AttackPathAnalysis #softcorpremium
Microsoft Purview - Paint By Numbers Series (Part 2f) – Automatic Labeling Emails and Files - Microsoft Community Hub
Microsoft has released a new tool called Purview for data management and governance. It offers features like data cataloging, automated data discovery, and data lineage tracking. Microsoft E5 Compliance provides step-by-step instructions for labeling and encrypting data. Multiple sensitivity labels can be used in Microsoft E5 Purview. Microsoft E5 Compliance offers tools for risk management and data protection. Users can now apply sensitivity labels to existing emails. Users have the option to apply or not apply recommended labels. Automatic labeling policies should be thoroughly tested before implementation. Microsoft E5 Purview allows for automatic labeling of files and emails. Users can assign permissions to individual users and groups. Users can create sensitivity labels in Word, Excel, and other applications. Users can apply automatic labeling to sensitive content. Custom policies and rules can be created for managing sensitive information. Users can create and customize rules for sensitive information types. Microsoft has introduced a feature called \"Automatic Labeling\" to automatically apply labels to files and emails. Users can simulate the policy and enable automatic labeling. Automatic labeling in Microsoft 365 may take some time to replicate. Users can pre-populate test sites with relevant data. Automatic labeling can be seen next to a padlock icon in files and emails. Sensitivity labels can be applied to Microsoft products to enhance data protection. Microsoft 365 Compliance has introduced new features for data protection and control. Sensitivity labels can be used with Microsoft Teams, SharePoint sites, and Microsoft 365 groups. Microsoft has introduced sensitivity labels in its Purview data management tool. Microsoft 365 Compliance has introduced updates to enhance data protection and control. Microsoft 365 has introduced a sensitivity label feature for content. Users should use the content provided in the document with caution and at their own risk.
#MicrosoftPurview #DataManagement #DataProtection #softcorpremium
Implementing Microsoft Sentinel and Two simulated threats from scratch! Then see Sentinel in action! - Microsoft Community Hub
Microsoft has released a comprehensive guide on how to protect your organization from cyber threats using Azure and M365 Defender. The guide covers setting up Azure resources, using security tools, and conducting threat simulations. Microsoft is also offering free trial licenses for Azure, Sentinel, and Microsoft Defender for Endpoint, along with virtual machines and security solutions. Azure Sentinel, a cloud-based security tool, integrates log analytics and incident response automation. Microsoft has also introduced new features such as Endpoint Detection and Response (EDR) utilizing virtual machines, and the ability to collect security event logs from Windows systems. Additionally, Microsoft offers resources on simulated attacks, setting up virtual machines, and enhancing cloud security with Zero Trust principles. #Microsoft #Azure #Cybersecurity
#ProtectYourOrganization #CybersecuritySolutions #AzureDefender #softcorpremium
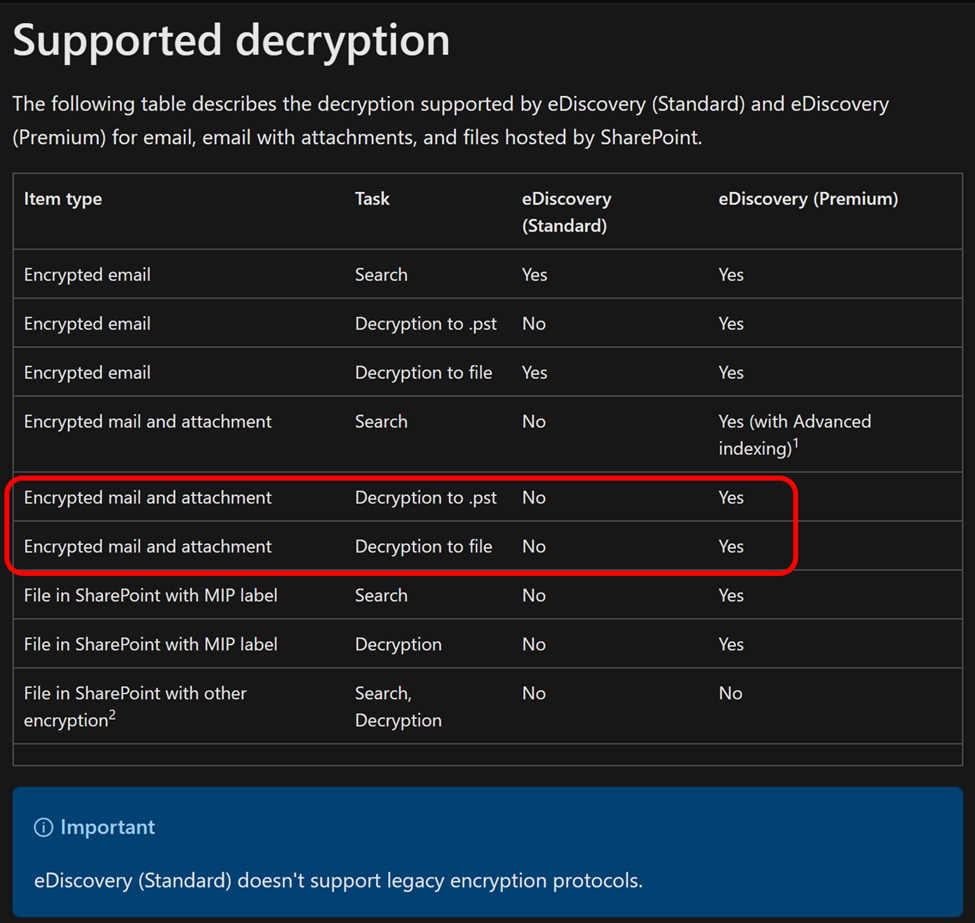
Microsoft Purview in the Real World (August 11, 2023) - Encrypted Emails and Purview eDiscovery - Microsoft Community Hub
Microsoft has released a document providing insights into various user cases, announcements, and customer-driven questions related to Microsoft Purview. The document emphasizes that it should not replace official documentation and advises users to defer to official sources for accurate information. The topics covered in this document include Purview-related eDiscovery and Office Message Encrypted (OME) emails. It provides guidance on conducting legal or HR reviews of OME emails within Purview eDiscovery, as well as accessing encrypted emails that have been exported to a PST and/or Exchange mailbox. The document also mentions the need for Roles Based Access Control (RBAC) for accessing and viewing emails/files in Purview, and provides links to relevant Microsoft documentation for further information. It concludes by reminding users to contact their Microsoft Account Team for specific use cases or needs, and provides additional links for configuring super users for Azure Rights Management and understanding email encryption in Microsoft 365.
#MicrosoftPurview #eDiscovery #RBAC #softcorpremium
Microsoft Entra Private Access: An Identity-Centric Zero Trust Network Access Solution - Microsoft Community Hub
Microsoft has introduced its identity-centric security service edge (SSE) solution and two new services, Microsoft Entra Private Access and Microsoft Entra Internet Access. The focus of this blog is on Microsoft Entra Private Access, which is an identity-centric Zero Trust Network Access (ZTNA) solution. It aims to modernize access to private applications and resources, allowing users to connect from any device and any network. The Private Access solution is built on Zero Trust principles, verifying every user and enforcing least privilege access. It offers enhanced security controls for all private applications, automatic private application discovery and onboarding, and granular segmented application access. Users can also benefit from intelligent local access, maintaining a consistent security posture whether accessing private applications remotely or on-premises. The solution can be easily migrated from legacy VPNs using Quick Access, and it works across various protocols and offers single sign-on capabilities. Microsoft Entra Private Access is delivered through Microsoft's global network, ensuring secure and fast access to private resources. The solution can be managed through the Global Secure Access (preview) in the Microsoft Entra admin center. Remote workers can connect to resources without using a VPN by installing the Global Secure Access Client. QuickAccess simplifies the configuration process, allowing users to specify IP addresses or FQDNs and port numbers to enable quick access. For more information and resources, users can refer to Microsoft's documentation and technical sessions.
#MicrosoftEntraPrivateAccess #ZeroTrustNetworkAccess #SecureAccessSolution #softcorpremium
Microsoft Purview Data Loss Prevention: Announcing general availability of several capabilities - Microsoft Community Hub
Microsoft has announced several new capabilities for its Purview Data Loss Prevention (DLP) solution. The DLP system helps organizations protect sensitive data across applications, services, and devices without the need for costly infrastructure or agents. The new capabilities include increased depth of protection through optical character recognition (OCR) in Exchange Online and Teams, extended support for document fingerprinting, enhanced label detection for non-Office and PDF files, and the ability to prevent users from copying and pasting sensitive information from internal databases to personal accounts and social media sites. Other enhancements include protection for virtualized environments, extended DLP protection for network file shares, and the ability to customize notifications and policy tips. Admins also gain improved device onboarding and investigation capabilities, as well as the ability to define user scopes based on attributes like geography. Microsoft Purview DLP is built into Windows 10 and 11 and offers a free trial for users to get started. Additional resources and a customer connection program are available for those interested in learning more about the solution.
#DataProtection #SecuritySolutions #MicrosoftDLP #softcorpremium
Honeywell to Acquire SCADAfence, Strengthening Its Cybersecurity Software Portfolio
Multinational conglomerate Honeywell has announced its acquisition of cybersecurity software company SCADAfence. This move aims to strengthen Honeywell's portfolio in the field of cybersecurity and enhance its capabilities in protecting critical infrastructure and industrial control systems from cyber threats. Honeywell's focus on cybersecurity aligns with the growing concerns surrounding the security of connected devices and the increasing number of cyber attacks targeting industrial systems. This acquisition highlights the increasing importance of cybersecurity in safeguarding critical infrastructure against potential threats.
#HoneywellAcquisition #CybersecurityInnovation #ProtectingCriticalInfrastructure #softcorpremium
BreachLock Intelligence Report Reveals Critical Insights From Thousands of Penetration Tests
BreachLock, a global leader in Penetration Testing Services, has released its 2023 Penetration Testing Intelligence Report. The report provides critical security insights from thousands of penetration tests conducted over a 12-month period, covering applications, APIs, networks, cloud, DevOps, and IoT. It also analyzes the most exploited OWASP Top 10 categories by industry and asset-specific vulnerabilities. The report highlights the growing importance of security control testing, the need for penetration testing tools and services, and the challenges faced by regulated industries in implementing effective security measures. BreachLock offers automated, AI-driven, and human-delivered Pentesting as a Service (PTaaS) solutions.
#PenetrationTesting #Cybersecurity #SecurityInsights #softcorpremium
Malware Unleashed: Public Sector Hit in Sudden Surge, Reveals New Research
New research has revealed a surge in malware attacks targeting the public sector, impacting various sectors including technology, cloud, remote workforce, and database security. The report emphasizes the importance of security monitoring, authentication, and privacy measures, as well as enhanced identity and access management and physical security. Black Hat Middle East and Africa events are upcoming, offering insights into cybersecurity. Webinars on topics such as automation and implementing zero-trust with a remote workforce are available. Reports highlight concerns about cyberattacks on government and public service organizations, as well as healthcare and financial services. The financial sector faces challenges such as the availability of commodity malware for ransomware attacks. BlackBerry has released a report on country-specific cyberattacks, providing countermeasures and Sigma rules. Tech news covers topics on cybersecurity, including threat intelligence, zero-trust protocols for remote workforces, and concerns about third-party risks and AI-enabled malware. Sense, a cybersecurity company, offers webinars and reports on implementing a zero-trust approach and using threat intelligence to mitigate risks. Websites are introducing Cookie Preference Centers to give users more control over their browsing experience and personalized ads. Allowing cookies is important for a personalized online experience.
#cybersecurity #publicsector #malwareattacks #softcorpremium
Cybercriminals Harness Leaked LockBit Builder in Wave of New Attacks
Cybercriminals are utilizing a leaked version of the LockBit ransomware builder to carry out new attacks. LockBit is a prominent ransomware-as-a-service (RaaS) operation, and after the code for LockBit v3 was leaked last year, unaffiliated hackers have begun using it for their own purposes. These cybercriminals are customizing the code to target local disks or network shares and demanding ransom payments in Bitcoin or Monero. While LockBit attacks are typically carried out by the official LockBit group or its affiliates, the leaked builder has allowed other hackers to exploit the ransomware for their own gain.
#Cybersecurity #RansomwareAttacks #LockBitLeak #softcorpremium
London Police Warned to Stay Vigilant Amid Major Data Breach
London Police have been warned to remain vigilant following a major data breach that exposed the personal information of 47,000 officers and staff. Hackers gained access to the IT systems of a contractor responsible for printing warrant cards and staff passes, stealing names, ranks, ID numbers, vetting levels, and photos. The breach has prompted the involvement of the National Crime Agency (NCA) to investigate the situation, and undercover officers have been pulled from the field. This breach comes shortly after a data leak earlier this month that put police officers at risk.
#datasecurity #cybersecurity #policeprotection #softcorpremium
Authentication Outage Underscores Why 'Fail Safe' Is Key
An authentication outage has emphasized the need for robust security measures and fail-safe systems at the edge of networks. Black Hat Middle East and Africa and Black Hat Japan Trainings are upcoming events that focus on cybersecurity threats and solutions. Duo, a popular authentication service, experienced a service outage, highlighting the importance of building resiliency and business continuity into authentication schemes. A recent research study emphasizes the need for alternative or backup login methods for two-factor authentication. Several universities experienced authentication system outages, emphasizing the importance of having no single points of failure in authentication infrastructures. Time-based one-time password (TOTP) authentication is recommended as a reliable failover mechanism. Organizations are advised to allow alternative forms of access or have a \"fail safe\" option to bypass two-factor authentication during disruptions. Automation and zero-trust approaches are increasingly important in enterprise cybersecurity. Additionally, events and resources are available to learn about IT security, remote work, cloud defense, and securing enterprise data. The use of cookies on websites can enhance user experience and provide personalized features, but users have the option to customize their settings for privacy preferences.
#Cybersecurity #Authentication #EnterpriseSecurity #softcorpremium
Financial Firms Breached in MOVEit Cyberattacks Now Face Lawsuits
Financial firms that were breached in cyberattacks targeting the MOVEit File Transfer Software are now facing class action lawsuits. TD Ameritrade and Charles Schwab have been named in lawsuits filed in the US District Court in Nebraska, accusing them of failing to secure customer data and other offenses. This comes after Prudential was hit with a similar lawsuit in New Jersey. Progress Software, the company behind MOVEit, is also facing a lawsuit for negligence and breach of contract. The Cl0p ransomware group claimed responsibility for the attacks, which compromised organizations such as Disney, Chase, and British Airways.
#cybersecuritybreach #classactionlawsuits #datasecurity #softcorpremium
Microsoft Defender for Cloud - strategy and plan towards Log Analytics Agent (MMA) deprecation - Microsoft Community Hub
Microsoft has announced that the Log Analytics agent, also known as MMA, will be retired in August 2024. The agent is currently used in Microsoft Defender for Cloud plans, specifically for Defender for Servers Plan 2 and Defender for SQL server on machines. As part of an updated strategy, the Azure Monitoring Agent (AMA) will no longer be required for Defender for Servers, but will still be required for Defender for SQL server on machines. Microsoft will be adjusting the features and capabilities of Defender for Servers to align with this change. The deprecated features and product capabilities that rely on the Log Analytics agent and Azure Monitoring agent will be replaced with a new alternative infrastructure before the deprecation date. Microsoft has provided a list of the affected features and their replacement timelines in the blogpost. Customers are advised to enable Defender for Endpoint integration and agentless disk scanning to ensure their servers are fully protected. Migrating from MMA to AMA is possible, but some Defender for Servers features will not be available on AMA. It is also clarified that running both the Log Analytics and Azure Monitor Agents on the same machine is possible, but duplicate data collection should be avoided. The timeline for the availability of the alternative infrastructure for each feature will be shared soon. The blogpost also addresses the impact on current customers using the MMA/AMA auto-provisioning process and provides guidance on how to ensure down-level machines remain fully protected. The unified agent integration for Windows Server 2012 R2 and Windows Server 2016 is recommended for improved capabilities. However, AMA may still be required for certain scenarios, such as deep analysis and investigation in Microsoft Sentinel.
#MicrosoftDefender #AgentRetirement #ServerSecurity #softcorpremium
Coming Soon: Enabling Extended Protection on Exchange Server by Default - Microsoft Community Hub
Microsoft has announced that Extended Protection (EP), a feature that protects servers from man-in-the-middle attacks, will be enabled by default on Exchange Server 2019 starting with the 2023 H2 Cumulative Update (CU14). This will make it more difficult for bad actors to carry out NTLM Relay and Ticket Replay scenarios. Admins will have the option to opt out of enabling EP, but Microsoft recommends that all customers enable it for enhanced security. Servers running older versions should be updated immediately to avoid vulnerabilities. Microsoft provides a script to enable EP on all Exchange servers in an organization.
#ExchangeServerSecurity #EnhancedProtection #MicrosoftUpdates #softcorpremium
Better SaaS Security Goes Beyond Procurement
Tech news reporter: \"SaaS security is crucial for businesses, with risks including attacks, breaches, and data privacy concerns. Comprehensive security measures beyond the initial procurement stage are necessary, including threat intelligence, endpoint authentication, and vulnerability management. Identity and access management is also important for safeguarding SaaS applications. Stay informed with upcoming events like Black Hat Japan Trainings and webinars on enterprise cybersecurity. Remember to prioritize SaaS security to protect your business from potential threats.\"
#SaaSsecurity #cybersecurity #technews #softcorpremium
Motherboard Mishaps Undermine Trust, Security
Recent motherboard mishaps have raised concerns about trust and security in the tech industry. These incidents have highlighted potential vulnerabilities that can be exploited by attackers. It is crucial to address these security issues to protect sensitive data, especially as technology becomes more prevalent in various sectors. Implementing strong authentication and mobile security measures is essential, as well as prioritizing physical security and IoT protection. Staying updated on the latest security threats and advancements is necessary to effectively mitigate risks. Furthermore, there have been reports of a bug affecting some MSI motherboards when running Microsoft's latest Windows Preview update. Both MSI and Microsoft are investigating the issue and advising users to refrain from installing the update. The US Cybersecurity and Infrastructure Security Agency has also issued a warning about vulnerabilities in the UEFI, which acts as a bridge between the operating system and the motherboard. Attackers have been exploiting these vulnerabilities to bypass Secure Boot. MSI has acknowledged the concerns and plans to release new BIOS files with enhanced security settings. It is important for organizations to stay updated on cybersecurity threats and vulnerabilities and to implement robust security measures to protect their systems.
#TechSecurity #CyberThreats #DataProtection #softcorpremium
5 Ways to Prepare for Google's 90-Day TLS Certificate Expiration
Google has announced that it will be expiring TLS certificates after 90 days, and businesses need to prepare for this change. Five ways to get ready for the expiration include monitoring certificate lifecycles, automating renewal processes, adopting certificate management tools, updating TLS protocols, and considering alternative certificate authorities. This change aims to enhance security and prevent potential vulnerabilities. In other news, upcoming events such as Black Hat Middle East and Africa and Black Hat Japan Trainings offer opportunities to learn about automation in enterprise cybersecurity and implementing zero-trust with a remote workforce. Dark Reading provides a wealth of resources on various aspects of cybersecurity, including perimeter analytics, threat intelligence, and compliance. Stay informed with the latest tech news and insights on The Edge and other featured sections.
#cybersecurity #TLScertificates #technews #softcorpremium
Legal Liability for Insecure Software Might Work, but It's Dangerous
Legal liability for insecure software is a double-edged sword, according to experts. While it may incentivize companies to prioritize security, it could also lead to unintended consequences and hinder innovation. The potential risks include stifling small businesses, increasing costs for consumers, and creating a culture of fear among developers. It is crucial to strike a balance between holding companies accountable and promoting a collaborative approach to cybersecurity.
Black Hat, a leading cybersecurity event, is set to take place in the Middle East and Africa from November 14-16. The event will feature discussions on advanced threats, insider threats, vulnerability management, identity and access management, and more. In addition, Omdia Research will present their latest findings. For those unable to attend, webinars are available on topics such as enterprise cybersecurity and implementing zero-trust with a remote workforce. Stay updated with the latest cybersecurity news and resources through Dark Reading's library of reports, webinars, white papers, and newsletters.
A new approach to promote secure software development suggests encouraging transparency rather than imposing strict regulations. By requiring companies to disclose their security practices, consumers and businesses can make informed decisions based on their risk preferences. This approach allows the market to drive demand for secure software and promotes competition among companies with robust security measures. This strategy aims to avoid burdening smaller companies disproportionately and stifling diversity and innovation in the software industry.
Software bills of materials (SBOMs) are being proposed as a way to achieve software security transparency without excessive regulation. Companies creating critical software are not currently incentivized to prioritize security, and a liability regime could have unintended negative consequences. Mandatory transparency, on the other hand, empowers consumers and encourages market-driven mechanisms to find the right level of security while fostering innovation. By implementing SBOMs, the software ecosystem can become more secure without burdening development organizations.
In recent tech news, a Defender-Pretender attack has exposed a major flaw in Microsoft's flagship EDR system. Additionally, a bug in billions of Intel CPUs has been discovered, revealing a significant design flaw. Cybersecurity experts are now calling for the industry to address the impact of climate change on security measures. Furthermore, a lead at OWASP has highlighted a critical vulnerability in software supply chain security. Various webinars are being conducted on topics such as automation in cybersecurity, implementing zero-trust with remote workforces, securing enterprise data, and mastering cloud defense strategies. Reports have also highlighted the importance of threat intelligence in mitigating third-party risks and concerns over ransomware, zero-day bugs, and AI-enabled malware. Lastly, managing identity in modern cloud and hybrid environments is a crucial aspect of security.
Tech news reporter: \"A website's privacy policy may impact your online experience. By visiting a website, it may collect data from you through cookies. While this data is used to personalize your web experience, you have the right to manage your preferences and block certain types of cookies. However, blocking cookies may affect the site's functionality. For more information, check the website's privacy policy.\"
Tech companies use cookies to track your browsing behavior and show you personalized ads. These cookies don't store personal information but identify your browser and device. If you don't allow these cookies, you'll see less targeted advertising.\"
#SoftwareSecurity #CybersecurityTransparency #TechNews #softcorpremium
Step-by-Step: Deploy Microsoft Defender For Identity – Comprehensive Guide - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity
Tech expert Charbel Nemnom has published a comprehensive guide on deploying Microsoft Defender for Identity, a cybersecurity tool that helps users stay protected against online threats. Microsoft has also made updates to its data processing policies, allowing companies to process personal data based on legitimate interest. Microsoft has introduced a range of new tools to enhance digital security, including Microsoft Defender for Identity. The industry is gradually shifting towards cloud-based solutions. Microsoft is replacing its Advanced Threat Analytics service with Microsoft Defender for Identity and has announced new updates to its Defender for Identity software. It has also launched Microsoft Domain Integrity (MDI) and introduced group Managed Service Accounts (gMSAs) for improved security. Microsoft 365 Defender now includes an Attack Disruption feature. Microsoft has released a guide on how to install MDI sensors on domain controllers and has introduced the MDI sensor feature in the Microsoft 365 Defender portal. Microsoft has also released a new PowerShell command for simplified installation of the MDI sensor on Windows Server Core. It has introduced the Azure Advanced Threat Protection sensor for enhanced server security. Microsoft Defender for Identity is a powerful cybersecurity tool for protecting sensitive data. A Microsoft MVP and MCT has shared a detailed guide on installing Windows services.
#MicrosoftDefenderForIdentity #Cybersecurity #DigitalSecurity #softcorpremium
Mastering Cybersecurity: Insights On Certification – Comprehensive Guide - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity
Tech expert Charbel Nemnom has published a comprehensive guide on cybersecurity certifications, covering different certifications like CCSP and CISM. The guide emphasizes the significance of privacy and transparency in the tech industry, as well as the use of cookies for personalized ads and content. Readers are given the option to give consent for data processing or make granular choices to maintain control over their personal data. The guide also provides step-by-step instructions on updating privacy settings on websites. Additionally, it mentions a course designed to help individuals pass the Official CCSP certification exam. The guide aims to enhance knowledge in cybersecurity and promote career growth in the field.
#cybersecuritycertifications #privacyandtransparency #careerdevelopment #softcorpremium
Centralized cloud security is now a must-have | InfoWorld
A recent survey of cybersecurity professionals found that 90% of respondents believe a single cloud security platform would be helpful for managing security consistently across multiple cloud deployments. Security silos, which occur when companies only use native security tools for specific cloud brands, are a major problem in cloud computing. These silos create complexity, inefficiency, and increased security risks. Centralized cloud security solutions offer advantages such as simplified management, reduced complexity, better visibility into security risks, and faster response to threats. However, transitioning to centralized security can be expensive, risky, and time-consuming. Despite the challenges, most enterprises will likely need to adopt centralized security solutions to effectively manage the risks and costs associated with cloud security.
#CloudSecurity #CentralizedSecurity #Cybersecurity #softcorpremium
AWS Firewall Manager is now available in Israel (Tel Aviv) region
AWS Firewall Manager is now available in the Tel Aviv region, making it available in a total of 30 commercial regions and 2 GovCloud regions. This security management service allows customers to centrally configure and manage firewall rules across their accounts and resources, including AWS WAF rules, AWS Shield Advanced protections, AWS Network Firewall, R53 resolver DNS Firewall, and VPC security groups. AWS Firewall Manager helps ensure consistent enforcement and compliance of firewall rules, even as new accounts and resources are created. For more information and to see the list of available regions, visit the AWS Firewall Manager website.
#AWSFirewallManager #SecurityManagement #CloudSecurity #softcorpremium