💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Use sensitivity labels on all e-mail messages, use encryption and protection where warranted - Microsoft Community Hub
The post recommends the use of sensitivity labels, encryption, and protection for all email messages where warranted to enhance security. The post is part of Microsoft's security and compliance best practices for its products. The post does not fall under the categories of cloud, observability, or open source.
#Microsoft #encryption #protection #softcorpremium
New timelines: Important actions to secure the partner ecosystem - Microsoft Community Hub
Microsoft has released a set of timelines for partners to ensure they are taking the necessary actions to secure the partner ecosystem. These timelines include actions such as completing security assessments, implementing multi-factor authentication, and complying with Microsoft's security requirements. The goal of these timelines is to improve the overall security posture of the partner ecosystem and protect customers' data from potential threats.
#MicrosoftPartner #security #softcorpremium
Introducing Azure AI Content Safety: Helping Organizations to Maintain Safe Online Spaces
Microsoft introduces Azure AI Content Safety, a tool designed to help organizations maintain safe online spaces. The tool uses AI and machine learning to identify harmful content in text, images, and videos, and provides a score indicating the likelihood of the content being harmful. Organizations can then decide whether to remove the content or take other actions to mitigate the risk.
#Azure #AI #ContentSafety #softcorpremium
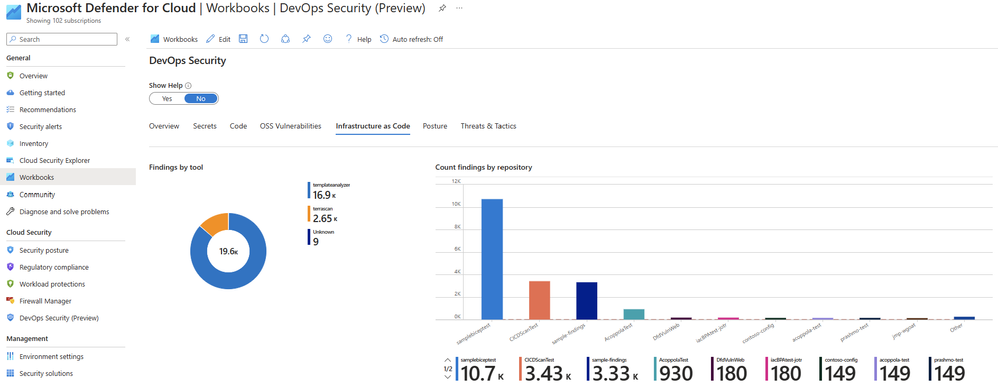
Microsoft Defender for DevOps Azure DevOps Connector - Microsoft Defender for Cloud PoC Series - Microsoft Community Hub
Microsoft has launched the Defender for DevOps Azure DevOps Connector, which is part of the Microsoft Defender for Cloud PoC series. The new connector allows developers to access Azure DevOps data from Microsoft Defender for Endpoint and Microsoft Defender for Identity to provide a comprehensive view of security across the software development lifecycle. The connector also enables the automation of security tasks and the implementation of security policies.
#MicrosoftDefender #AzureDevOps #MicrosoftCommunity #softcorpremium
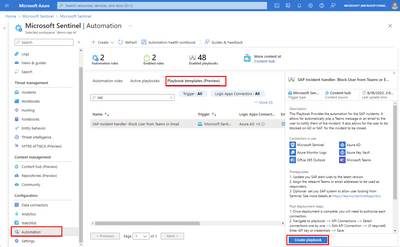
Revolutionize your SAP Security with Microsoft Sentinel's SOAR Capabilities
Revolutionize your SAP Security with Microsoft Sentinel's SOAR Capabilities
#MicrosoftSentinel #SOAR #softcorpremium
Enrich your advanced hunting experience using network layer signals from Zeek
The post discusses how to enrich advanced hunting experience using network layer signals from Zeek.
#Zeek #advancedhunting #softcorpremium
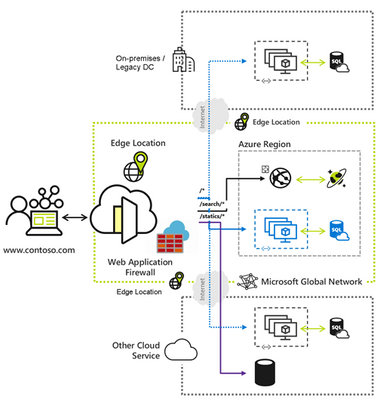
Enhance Web App Security with Azure Front Door's Web Application Firewall (WAF) | Learn How
The post talks about how Azure Front Door's Web Application Firewall can enhance web application security. It highlights the features of WAF and the benefits it provides to web applications. The post also provides information on how to configure and customize the WAF policies. Overall, it is a useful resource for developers and organizations looking to improve the security of their web applications.
#AzureFrontDoor #WebApplicationFirewall #WAF #softcorpremium
Transform the way you investigate by using Behaviors & new detections in XDR, starting w/SaaS apps - Microsoft Community Hub
Microsoft Community Hub introduces the use of Behaviors and new detections in XDR starting with SaaS apps. This will transform the way investigations are conducted by giving users the ability to see behavior indicators in real-time, enabling them to isolate and remediate threats quickly. The new detection capabilities in XDR will provide more visibility and control over SaaS apps, allowing users to detect and prevent threats in real-time. By combining these new features, XDR can help organizations improve their security posture and detect advanced threats more quickly.
#Behaviors #detections #XDR #softcorpremium
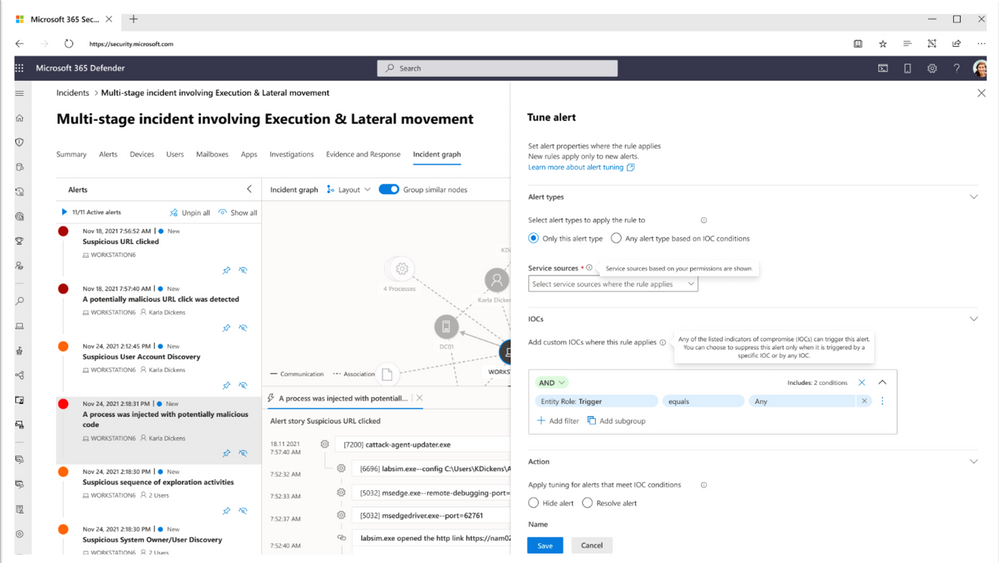
Boost your detection and response workflows with alert tuning
The post discusses the importance of alert tuning to improve detection and response workflows. It emphasizes the need to prioritize alerts and customize them to meet specific needs, reducing alert fatigue and optimizing security operations. The post highlights some key considerations, such as the use of automation and machine learning, to enhance alert tuning capabilities and streamline security operations.
#alerttuning #detection #response #softcorpremium
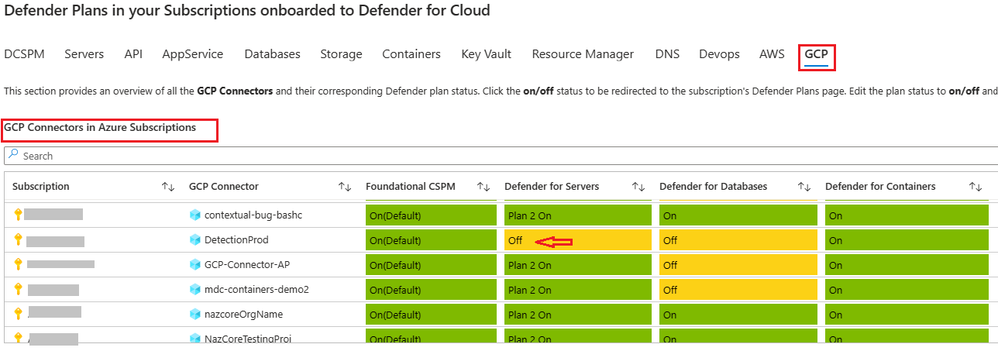
Defender for Cloud
Microsoft has launched a new cloud-native security solution called Microsoft Defender for Cloud. The solution is designed to simplify cloud security management by providing a unified view of security across different cloud workloads and services. It uses AI and automation to detect and respond to threats in real-time, and provides insights and recommendations to help organizations improve their security posture. Microsoft Defender for Cloud supports multiple cloud platforms, including Microsoft Azure, Amazon Web Services, and Google Cloud Platform.
#MicrosoftDefender #CloudSecurity #softcorpremium
Azure Firewall NAT Behaviors - Microsoft Community Hub
The post on Microsoft Community Hub discusses the NAT behaviors of Azure Firewall. The article explains how the Azure Firewall NAT works and how to configure it. The post also covers the differences between the Azure Firewall and other NAT solutions, as well as common scenarios where Azure Firewall NAT can be used. Overall, the article provides insights into the functionality of Azure Firewall and how it can be utilized to improve security in the cloud.
#Azure #firewall #softcorpremium
Microsoft Entra (Azure AD) Blog - Microsoft Community Hub
Microsoft Entra (Azure AD) Blog discusses the latest features and updates to the Azure Active Directory. The post is geared towards IT professionals and highlights new capabilities like the ability to enforce multifactor authentication for admins, self-service password reset for cloud users, and user risk policies. The post also provides guidance on how to configure and deploy these features to ensure secure access to company resources.
#Microsoft #Azure #AzureAD #softcorpremium
Advanced hunting for Microsoft Purview Data Loss Prevention (DLP) incidents - Microsoft Community Hub
Jon Nordström shared a post on the Microsoft Community Hub discussing advanced hunting for Microsoft Purview Data Loss Prevention (DLP) incidents. The post highlights how to create a custom query to find sensitive data and how to use the query to trigger an alert. The author also provides a sample query to help users get started with their DLP monitoring. Overall, the post serves as a helpful resource for those utilizing Microsoft Purview for data protection.
#MicrosoftPurview #DataLossPrevention #DLP #softcorpremium
Automatically disrupt adversary-in-the-middle attacks with XDR
The post talks about how XDR can automatically disrupt adversary-in-the-middle attacks.
#XDR #security #softcorpremium
Partnering with Health-ISAC to strengthen the European healthcare system | Google Cloud Blog
Google Cloud has expanded its partnership with Health Information Sharing and Analysis Center (Health-ISAC) to include CISOs and security leaders in Europe, the Middle East, and Africa (EMEA). The partnership will bring cybersecurity experts together with practitioners from the Health-ISAC, law enforcement, and regulatory bodies on a 17-city tour across the region, starting in Zurich, Switzerland, to discuss unique threat landscapes, better sharing of threat intelligence, emerging European laws and regulations, and initiatives to protect Europe’s healthcare system from ransomware and digital extortion.
#HealthISAC #cybersecurity #EMEA #softcorpremium
General Availability: Multi-Region Replication for Azure Key Vault Managed HSM - Microsoft Community Hub
Microsoft has announced the general availability of multi-region replication for Azure Key Vault Managed HSM. This new capability replicates customer-managed keys across Azure regions, providing enhanced disaster recovery and high availability. The feature is now available in all Azure regions where Azure Key Vault Managed HSM is available. The functionality is designed to help customers meet local data residency requirements, improve performance, and strengthen compliance and security postures.
#Azure #KeyVault #HSM #softcorpremium
Stronger together: Highlights from RSA Conference 2023 | AWS Security Blog
The AWS Security Blog has shared highlights from the RSA Conference 2023, where AWS discussed the latest trends in cybersecurity and showcased its products and services. The conference focused on the need for collaboration and innovation to address the evolving threats facing businesses. AWS highlighted its security capabilities, including threat detection and response, compliance, and identity and access management. The company also announced new features and partnerships to bolster its security offerings.
#RSAConference #cybersecurity #AWS #softcorpremium
Microsoft reports jump in business email compromise activity | CSO Online
Microsoft reports a significant increase in business email compromise (BEC) activity between April 2022 and April 2023. The company detected over 150,000 daily attempts on average, with BEC groups using Google Translate to target high-value victims. The spike in activity highlights the evolving nature of cyberattacks and the need for continued vigilance in protecting against BEC scams.
#BEC #cybersecurity #softcorpremium
Log forensics with Dynatrace Grail: Finding malicious activity
Dynatrace Grail helps in log forensics, especially in investigating security incidents based on log data with modern observability technologies. These cloud-native technologies help organizations stay competitive, agile, and grow; however, it has become more challenging to investigate security incidents as data and complexity have proliferated. Dynatrace Grail provides deep visibility into and understanding of applications and infrastructure, which is necessary to maintain control and gain visibility into all applications, microservices, and data dependencies generated in cloud environments.
#logforensics #security #observability #softcorpremium
What cybersecurity professionals can learn from the humble ant | CSO Online
The article talks about what cybersecurity professionals can learn from ants. Just like ants use pheromones to warn of impending danger and protect their colony, cybersecurity professionals can use threat intelligence sharing to protect their organization and the industry as a whole. The article emphasizes the importance of collaboration and information sharing in the cybersecurity community.
#cybersecurity #ants #softcorpremium
Container security fundamentals part 4: Cgroups | Datadog Security Labs
This post by Datadog Security Labs explores how Linux control groups (cgroups) can be used to manage each process's access to resources, such as CPU and memory, to avoid overconsumption by a single misbehaving program. Docker and other containerization tools use cgroups to restrict the resources that containers can use, which can help avoid noisy neighbor issues. The post covers several security aspects of cgroups, including how you can use them to reduce the risk of denial-of-service attacks and manage containers' access to specific devices on a host.
#cgroups #containerization #Linux #security #softcorpremium
Former Uber CSO Joe Sullivan and lessons learned from the infamous 2016 Uber breach | CSO Online
Former Uber CSO Joe Sullivan discusses lessons learned from the infamous 2016 Uber breach and the increased liability risk CISOs face. Sullivan's role as CSO of Uber was a shift from his previous job as an assistant US attorney prosecuting cybercriminals. The guilty verdict in the Uber breach case makes personal liability real for CISOs. This is a 'watershed moment' for CISOs' liability risk.
#Uber #CSO #cybersecurity #softcorpremium
New hyperactive phishing campaign uses SuperMailer templates: Report | CSO Online
Threat actors are conducting a high-volume credential harvesting campaign using SuperMailer, a legitimate email newsletter program, according to network security firm Cofense.
#phishing #SuperMailer #softcorpremium
Think security first when switching from traditional Active Directory to Azure AD | CSO Online
The article discusses the importance of prioritizing security when transitioning from traditional Active Directory to Azure AD. It highlights the significance of managing security in the cloud through Microsoft Intune and defending against attacks on Azure AD. The post also raises questions about the future of security boundaries and the role of Active Directory in network foundations.
#AzureAD #security #softcorpremium
Legitimate looking npm packages found hosting TurkoRat infostealer | CSO Online
Legitimate looking npm packages are found hosting TurkoRat infostealer despite efforts taken in recent years to proactively monitor public software repositories for malicious code.
#npm #TurkoRat #softcorpremium