💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Wiz Receives 2023 Global Cloud Security Entrepreneurial Company of the Year Award | Wiz Blog
Wiz has received the 2023 Global Cloud Security Entrepreneurial Company of the Year Award. The post contains customer reviews and testimonials about the Wiz tool which is described as a game changer and a must-have tool in any CISO stack. It is user-friendly and provides improved visibility into cloud security posture. Wiz is a one-stop-shop cloud security tool with many integrations and alerts updated constantly.
#cloud #security #softcorpremium
The Power of Integrating Secureworks and Netskope
The post discusses the acquisition of Secureworks by Dell in 2011 and their reputation as a leader in managed security services. It also highlights the benefits of integrating Secureworks and Netskope.
#Secureworks #Dell #Netskope
What's New: APIs in Microsoft Graph
Microsoft has announced that unified APIs are now available in public preview, allowing organizations to query Defender TI data to operationalize intelligence gleaned from threat actors, tools, and vulnerabilities. The new Defender TI API release has many use cases, including incident enrichment, advanced hunting with Azure notebook, SIEM integration, and reporting.
#Microsoft #DefenderTI
BrandPost: Leveling Up Cloud Native Security with Integrated DLP and Threat Intel
Securing public cloud environments with tools like Cloud Native Application Protection Platforms (CNAPP) has become a top priority for InfoSec leaders. Cloud security spending has increased with the market growing at a rate of 25.1% year over year, but unfortunately, so has the number of data breaches.
#CloudSecurity #CNAPP
Let’s pump the brakes on the rush to incorporate AI into cybersecurity
The article discusses the growing trend of integrating artificial intelligence into security offerings, highlighting both its potential benefits and threats. It also mentions a recent April fools prank pulled by the Twitter account for the MITRE ATT&CK platform involving an AI response generator.
#ArtificialIntelligence #SecurityOfferings
Securing Terraform State in Azure
This article emphasizes the significance of protecting Terraform state in Azure and offers best practices to ensure its security, including utilizing Azure Blob Storage for remote state storage with encryption and access control, creating a dedicated container within an Azure storage account to store Terraform state files, and enabling Azure Storage Service Encryption (SSE) to secure Terraform state files at rest using Azure-managed keys or customer-managed keys.
#Azure #Terraform
What's new with Microsoft Sentinel at Secure
Microsoft Sentinel is a cloud-native SIEM solution that helps defenders proactively protect their digital estate with the power of AI, automation and deep understanding of the threat landscape. Recently, they have expanded their SAP app coverage and certification, added new incident management, investigation and response features, connections to Microsoft Defender Threat Intelligence, increased multi-cloud protection, and expanded support for business applications within Microsoft Sentinel.
#Microsoft #Sentinel #SIEM
Developers Rejoice! Azure Cache for Redis Enterprise Features to Make Your Job Easier (Preview)
Azure Cache for Redis Enterprise has released preview features that improve developer efficiency and enhance security. Connection audit logging and a flush command for active-active caches with active geo-replication are now available, allowing for better logging capability, tracking of unsuccessful authentication attempts, safer and more consistent cache flushing, and limit access control roles to specific users.
#Azure #RedisEnterprise #security
The Shared Responsibility Model for Security in The Cloud (IaaS, PaaS & SaaS)
The article discusses the shared responsibility model for cloud security, where customers and vendors share responsibilities. It also explores the arguments for and against cloud security, with proponents stating that multi-billion cloud vendors are better equipped to handle sensitive business information.
#cloudsecurity #sharedresponsibilitymodel
US Space Force Requests $700M for Cybersecurity Blast Off
The US Space Force has asked for $700M to be allocated for cybersecurity measures as they prepare for their upcoming launch.
#US #SpaceForce
Securing cloud native environments: CNCF Cloud Native Security Whitepaper version 2 audio is now available
The CNCF Security Technical Advisory Group has released an audio version of their Cloud Native Security Whitepaper v2, which provides practical recommendations on securing cloud infrastructure. The audio version includes updates such as Secure Defaults Cloud Native 8 and guidance for sharing feedback.
#CloudNative #Security
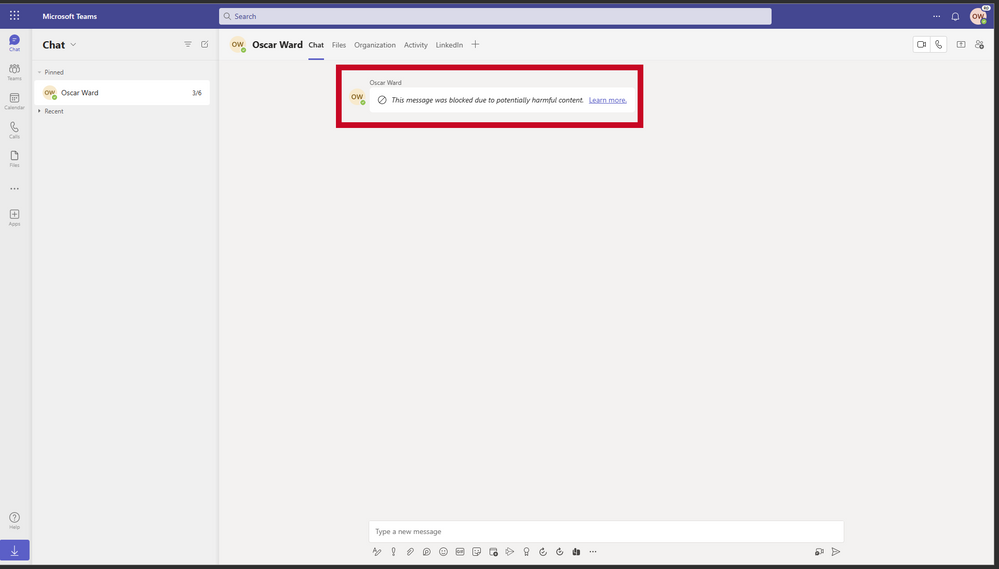
Announcing Collaboration Security for Microsoft Teams
Microsoft Teams has become indispensable for effective collaboration, with 270 million users worldwide. However, the growing number of users has also made it a new target for cyber attacks like phishing and ransomware. To address this, Microsoft has announced the public preview of Collaboration Security for Microsoft Teams, which will provide end-to-end protection and help build cybersecurity awareness and resilience for end users.
#MicrosoftTeams #CollaborationSecurity
Protect production branches from having secrets through an Azure DevOps branch policy
The post shares a strategy for protecting production branches from code secrets, with requirements of simplicity, comprehensive monitoring, developer alerts, false positive suppression, automatic onboarding, and free implementation. The solution involves using Azure DevOps features including build validation policy, Microsoft Security DevOps extension, and SARIF SAST Scans Tab.
#AzureDevOps #MicrosoftSecurityDevOps
Australia Is Scouring the Earth for Cybercriminals — the US Should Too
Australia is actively searching for cybercriminals worldwide and the US should follow suit in order to combat cybercrime.
#Australia #cybercriminals #US
Obsidian launches new SaaS security and compliance tools
Obsidian has launched its SaaS security posture management solution with new security and compliance tools, featuring three primary modules including Obsidian Compliance Posture Management, Obsidian Integration Risk Management, and Obsidian Extend. It provides posture hardening, third-party SaaS integration risk management, and threat mitigation for SaaS as the only company in the SaaS security industry to deliver a unified solution that covers all aspects of SaaS security comprehensively.
#Obsidian #SaaSsecurity
Uncover the latest cloud data security capabilities from Microsoft Defender for Cloud
Organizations are rapidly moving their data to the cloud, leading to complex and dynamic cloud data estates that create security blind spots for security teams. Microsoft has announced new enhancements for its cloud-native application platform, offering a comprehensive multicloud data security solution to help organizations strengthen their security posture and maintain continuous threat protection against active data breaches.
#cloud #security #multicloud
Hey, Siri: Hackers Can Control Smart Devices Using Inaudible Sounds
The post discusses how hackers can use inaudible sounds to take control of smart devices, and the potential implications for privacy and security.
#privacy #security
Connect your software with the right people: Ownership drives effective collaboration
The post discusses the importance of ownership in effective collaboration and problem resolution when dealing with critical security vulnerabilities affecting multiple parts of an environment.
#ownership #collaboration
5 ways to tell you are not CISO material
The post discusses the qualities and skills required for cybersecurity practitioners to be successful as a CISO, including technical expertise, experience in managing people, making crucial decisions, and driving change.
#cybersecurity #CISO
Organizations Reassess Cyber Insurance as Self-Insurance Strategies Emerge
Organizations are reconsidering their reliance on cyber insurance as self-insurance strategies become more popular.
#cyberinsurance #selfinsurance
The Pope's Security Gets a Boost With Vatican's MDM Move
The Vatican has implemented a Mobile Device Management (MDM) system to enhance security measures for the Pope's mobile devices.
#Vatican #MobileDeviceManagement #MDM
Best Practices for SOC Tooling Acquisition
The post discusses the challenges faced by Security Operations Centers in keeping corporate data safe and the importance of having the right tooling. It also highlights the complexity of deciding when and how to invest in SOC tooling amidst vendor spin.
#SecurityOperationsCenters #SOCtooling
Microsoft Entra Change Announcements – March 2023 Train
Microsoft has announced its March 2023 change announcements which includes security improvements such as number matching for Microsoft Authenticator push notifications. Organizations can continue to use the existing rollout controls until May 8, 2023, to deploy number matching in their organizations.
#Microsoft #security #Authenticator
Post-Quantum Satellite Protection Rockets Towards Reality
The article discusses the development of post-quantum cryptography for satellite protection and its progress towards implementation in reality through the use of quantum-resistant algorithms.
#postquantum #cryptography
Spera exits stealth to reveal identity-based threat hunting capabilities
Israeli cybersecurity provider Spera has launched its identity security posture management offering, which aims to address the lack of tools for managing identity attack surface and risk across enterprise environments. The platform provides visibility into enterprise identities and actions to help improve security posture.
#identitysecurity #securityposturemanagement