💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
North Dakota turns to AI to boost effectiveness and efficiency of its cybersecurity
The State of North Dakota is using AI to improve its cybersecurity operations in a more efficient and cost-effective manner, while also relieving cybersecurity personnel of tedious tasks.
#cybersecurity #AI
Google Cloud Security Best Practices — Identity and Access Management(IAM) | by Vishal Bulbule | Google Cloud - Community | Apr, 2023 | Medium
This blog post discusses Google Cloud's shared responsibility model for security, which defines the security responsibilities between Google Cloud and its customers. The post then delves into best practices for Identity and Access Management (IAM), focusing on the principle of least privilege - granting users and service accounts only the minimum permissions they need to perform their job. The post emphasizes the importance of IAM in cloud security and provides practical tips for securing access control and user management.
#GoogleCloud #IAM #security #softcorpremium
How secure is your public cloud? Quick wins & best practices | Wiz Blog
The blog post talks about the importance of securing public cloud and introduces Wiz, a cloud security tool that provides vulnerability assessment, integrations, and alerts. It highlights the benefits of using Wiz such as enhanced cloud visibility, ease of implementation, and excellent customer service. The post includes quotes from satisfied customers who consider Wiz a game-changer and a must-have tool for any CISO stack.
#cloudsecurity #CSPM #softcorpremium
CISA updates zero trust maturity model to provide an easier launch
The United States Cybersecurity and Infrastructure Security Agency (CISA) has published an updated Zero Trust Maturity Model (ZTMM) version 2, which includes feedback received from public comments on the first version.
#ZeroTrust #CISA
Introducing Data collaboration in Microsoft Purview data catalog with Ratings feature
Ratings and reviews can help provide trust and confidence to users discovering data assets in Microsoft Purview data catalog for usage either in an analytical pipeline, reporting dashboard, etc. Users can now provide a rating of 1-5 and leave comments on the data asset which can be used by analysts to understand and use the most trusted and used data.
#MicrosoftPurview #datacatalog
Darwinium upgrades its payment fraud protection platform
Security vendor Darwinium has updated its platform to provide shared intelligence on anonymized data sets, offering customers control of user data while preventing cybercrime targeting.
#Security #cybercrime
Splunk Gets the Hat Trick!
Splunk Security has been named a Leader in SIEM and security analytics by three analyst firms - Forrester, IDC, and a third analyst firm. Splunk Enterprise Security received the highest possible scores in product vision, enhancements, market approach, and partner ecosystem criteria in The Forrester Wave: Security Analytics Platforms, Q4 2022 report.
#Splunk #Security #SIEM
What's New: Hash and URL Search Intelligence
Microsoft Defender Threat Intelligence (Defender TI) now includes File Hash and URL Search capabilities, empowering security professionals to search for high-quality threat intelligence, including verdicts and associated metadata, through static and dynamic analysis of files and URLs within and outside its ecosystem.
#MicrosoftDefender #DefenderTI
Deloitte and Wiz Announce a Strategic Alliance to Help their Mutual Clients Accelerate Digital Transformation with a Modern Cloud Security Strategy | Wiz Blog
Deloitte and Wiz have formed a strategic alliance to help their mutual clients accelerate digital transformation with a modern cloud security strategy. Wiz is a cloud security posture monitoring tool that has received high praise from users for its features, ease of use, and effectiveness. The partnership between Deloitte and Wiz aims to provide clients with a comprehensive cloud security solution that addresses the challenges of cloud governance and risk management.
#cloudsecurity #CSPM #digitaltransformation #softcorpremium
The Cado Platform Full Export for Forensic Data Lakes
Cado Security has expanded their platform's feature set to allow the export of all system data, following the previous release of a SIEM export feature.
#CadoSecurity #SIEM
Financial services IT leaders can boost customer lifetime value with DevSecOps-driven innovation
Financial services IT leaders can boost customer lifetime value with DevSecOps-driven innovation
#Financial #DevSecOps #innovation
The CSO guide to top security conferences
CSO editors have compiled a list of top security conferences for 2023 that are essential for professionals looking to stay updated on security trends and threats, and benefit from face-to-face networking and knowledge gathering opportunities.
#security #conferences #professionals
BrandPost: The status quo for DNS security isn’t working
DNS-over-HTTPS (DoH) is growing in popularity as an enterprise privacy and security function, but it also poses challenges for organizations trying to monitor their DNS traffic.
#DoH #privacy #security
Cybersecurity startups to watch for in 2023
Cybersecurity startups often solve problems ahead of the mainstream and can innovate faster than established companies, but lack resources and maturity. Committing to a startup product or platform requires a different kind of customer/vendor relationship and can bring huge rewards if it provides a competitive advantage or reduces stress on security resources.
#Cybersecurity #startups
Announcing Windows LAPS management through Microsoft Intune
Intune now supports managing and supporting Windows Local Admin Password Solution (LAPS), bringing Microsoft's admin password management solution to the cloud. Windows LAPS has been revamped to integrate into the Windows platform to securely rotate and backup passwords using Microsoft Entra, Azure Active Directory (Azure AD), and IT admins can use first-class management experiences built into Intune to configure Windows LAPS.
#Intune #WindowsLAPS
QBot Expands Initial Access Malware Strategy With PDF-WSF Combo
QBot now uses a PDF-WSF combo as part of its initial access malware strategy.
#PDF #WSF
Russian Fancy Bear APT Exploited Unpatched Cisco Routers to Hack US, EU Gov't Agencies
Russian Fancy Bear APT used unpatched Cisco routers to hack US and EU government agencies.
#Russian #FancyBear
'GhostToken' Opens Google Accounts to Permanent Infection
A new vulnerability dubbed 'GhostToken' has been discovered that allows hackers to take over Google accounts and gain permanent access.
#GhostToken #Google
Splunk at Carrefour – Enterprise Resilience in Action
Splunk is supporting Carrefour's global Security Operations Center (SOC) in protecting their business and improving customer experience day in and day out, resulting in the team being able to respond to security threats 3x faster.
#Splunk #Carrefour #SecurityOperationsCenter
Protect your Amazon Cognito user pool with AWS WAF
Amazon Cognito provides advanced security features for authentication and user management in web and mobile applications.
#Amazon #Cognito #security
Datadog Expands Application Security Capabilities to Automatically Uncover Vulnerabilities in Production Code
Datadog announces general availability of Application Vulnerability Management, automatically uncovering and prioritizing important vulnerabilities in open-source libraries for improved application security.
#ApplicationVulnerabilityManagement #open-source #libraries
7 cybersecurity mindsets that undermine practitioners and how to avoid them
Cybersecurity jobs are high-pressure due to the industry's mindset, which affects security professionals' mental state.
#Cybersecurity #jobs
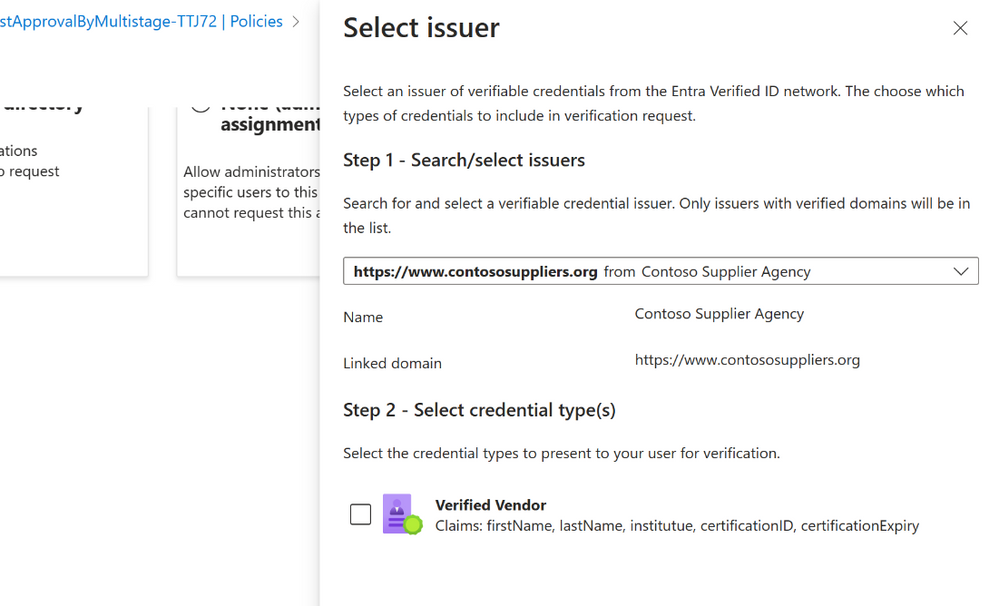
Entra Identity Governance with Entra Verified ID – Higher Fidelity Access Rights + Faster Onboarding
Entra Identity Governance Entitlement Management has integrated Microsoft Entra Verified ID technology to simplify the onboarding process for new users, including employees, contractors, partners, or other business guests, by verifying their identity information and credentials. This integration allows access packages to be automatically configured with Verified ID requirements in just 3 steps.
#IdentityGovernance #EntitlementManagement #VerifiedID
Is Your Business Secure Enough to Work at the Edge?
The article discusses the importance of securing edge computing as more businesses move towards it to operate their manufacturing environments and conduct daily operations.
#edgecomputing #manufacturing
Businesses detect cyberattacks faster despite increasingly sophisticated adversaries
Global organizations are improving their attack detection capabilities, as the global median dwell time has dropped to 16 days in 2022, according to Mandiant's M-Trends 2023 report. However, adversaries are becoming increasingly sophisticated, persistent, and confident.
#Mandiant #MTrends2023