💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Google Cloud Platform Security Checklist : Part 3/7 — Network Security | by Hassene BELGACEM | Google Cloud - Community | May, 2023 | Medium
This blog post is the third part of the Google Cloud Platform (GCP) security checklist series. It highlights the importance of network security and offers recommendations to secure the GCP infrastructure. The article suggests adopting a hub and spoke design for the network, organizing resources into shared VPCs based on environment and security levels, and deleting default networks. By implementing these best practices, organizations can effectively manage firewall rules, routing policies, and access controls to protect their network from potential threats and vulnerabilities.
#networksecurity #GCPsecurity #softcorpremium
Support tip: Removing and preventing the use of applications on iOS/iPadOS and Android devices - Microsoft Community Hub
The blog post discusses how to remove and prevent the use of applications on iOS/iPadOS and Android devices. It provides step-by-step instructions on how to remove apps from devices and how to prevent users from installing unauthorized apps. The post also highlights the importance of controlling app usage to protect against security threats and data breaches. It is a useful resource for IT professionals and anyone concerned about device security.
#iOS #iPadOS #Android #softcorpremium
Microsoft Purview: Comprehensive solutions for data governance, protection, compliance & management. - Microsoft Community Hub
Microsoft Purview is a comprehensive solution that provides data governance, protection, compliance, and management. The platform enables organizations to access, analyze, and collaborate on data in a secure and compliant manner. Microsoft Purview is designed to integrate seamlessly with Azure services and other Microsoft products, making it easy for users to manage their data from a single platform. With Microsoft Purview, organizations can better understand their data assets, manage data access and permissions, and ensure compliance with industry regulations.
#data #governance #compliance #management #softcorpremium
Become a Microsoft Defender Threat Intelligence Ninja: The complete level 400 training
This post on Microsoft Tech Community announces the availability of a complete level 400 training for becoming a Microsoft Defender Threat Intelligence Ninja. The training covers topics such as threat intelligence fundamentals, data analysis, and automation. The post is focused on providing relevant training to individuals interested in enhancing their knowledge and skills in threat intelligence using Microsoft Defender.
#MicrosoftDefender #ThreatIntelligence #training #softcorpremium
What's New: Defender TI Intel Reporting Dashboard and Workbook - Microsoft Community Hub
Microsoft has recently announced the release of its Defender TI Intel Reporting Dashboard and Workbook. This feature will enable security teams to access information about threats and vulnerabilities in order to make informed decisions. The dashboard is designed to be user-friendly and includes features such as automatic updating and customizable widgets. The Workbook provides additional insights and analytics. This is a major step forward for Microsoft in the security space, as it further enhances its Defender suite of products and services.
#MicrosoftDefender #security #softcorpremium
Creating custom recommendations & standards for AWS/GCP workloads with Microsoft Defender for Cloud - Microsoft Community Hub
This blog post discusses how to create custom recommendations and standards for AWS/GCP workloads with Microsoft Defender for Cloud. The post highlights the importance of understanding and managing cloud security risks and how Microsoft Defender for Cloud can help organizations detect and respond to threats in their cloud environments. The post also emphasizes the need for a comprehensive security strategy that includes proactive monitoring, threat detection, and incident response.
#AWS #GCP #MicrosoftDefenderforCloud #softcorpremium
Throttling and Blocking Email from Persistently Vulnerable Exchange Servers to Exchange Online - Microsoft Community Hub
Microsoft has announced the throttling and blocking of email from persistently vulnerable Exchange servers to Exchange Online in order to prevent continued exploitation by cyber attackers. This is part of Microsoft's ongoing efforts to protect its customers from threats and keep Exchange Online secure, as well as to encourage organizations to keep their on-premises Exchange servers up to date with the latest security patches and updates. Customers who are affected by this measure will be contacted by Microsoft's support team to help them address any issues and ensure their email is protected.
#ExchangeOnline #MicrosoftCommunityHub #softcorpremium
Wiz is on the FedRAMP Marketplace
Wiz, a cloud security company, is now listed on the FedRAMP Marketplace which will allow U.S. government agencies to easily access and deploy their services.
#Wiz #FedRAMP #cloudsecurity
Close the Permissions Gap With Identity And Access Management For Multicloud Workforces
The post discusses the importance of Identity and Access Management in bridging the permissions gap for employees working across multiple cloud environments.
#IdentityAndAccessManagement #permissionsGap
A sneak peek at the identity and access management sessions for AWS re:Inforce 2023 | AWS Security Blog
The AWS Security Blog has given a sneak peek into the Identity and Access Management (IAM) sessions that will be featured at AWS re:Inforce 2023. The post highlights the importance of IAM in securing cloud environments and mentions the different sessions that will cover various IAM topics, such as permission boundaries, multi-account management, and identity federation. The blog post also provides a link to register for the event and encourages attendees to take advantage of the valuable IAM sessions.
#AWSreInforce #IAM #security #softcorpremium
Cybersecurity stress returns after a brief calm: ProofPoint report | CSO Online
According to a ProofPoint survey, global cybersecurity concerns are back to pandemic levels as 68% of CISOs from 16 countries fear a cyberattack in the next year. The report shows that cybercriminals are using new attack tactics, including voice phishing, and are targeting remote workers. Companies need to invest in a strong cybersecurity strategy to protect their data and systems from these evolving threats.
#cybersecurity #cyberattacks #CISOs #softcorpremium
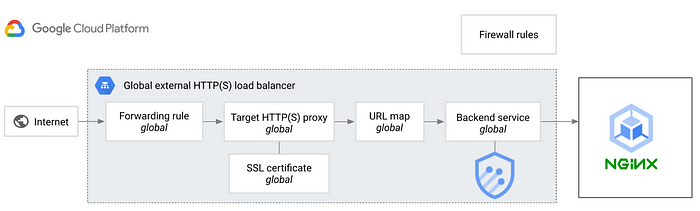
Secure your Nginx Ingress controller behind Cloud Armor | by Mathieu Benoit | Google Cloud - Community | May, 2023 | Medium
The post discusses the process of securing Nginx Ingress Controller behind Cloud Armor. The author highlights that the process is not supported like it is with the GCE ingress controller, but it can be done manually. The post provides pointers to set it up and talks about the benefits of using external L7 load balancing over mesh-based ingress.
#CloudArmor #HTTPS #NginxIngressController #softcorpremium
Manage IAM permissions with the Google Cloud mobile app | Google Cloud Blog
Google Cloud has announced an enhancement to its mobile app that allows administrators to manage their organisation’s cloud identities and access from the mobile platform of their choice. The new capability enables users to easily view, assign and search for all the roles in their organisation as well as assign multiple roles at the same time and view a list of users.
#GoogleCloud #IAM #permissionsmanagement #softcorpremium
Solving the SBOM crisis with WebAssembly components | InfoWorld
Recent reports have highlighted the problem of inherited software vulnerabilities. Many businesses are at risk and this post explains how WebAssembly's component model will offer a progressive path forward. Despite industry-wide efforts to develop policies, practices, tooling, and education around open source security, more than 70% of companies remain vulnerable to Log4shell.
#SBOM #WebAssembly #softcorpremium
Majority of US, UK CISOs unable to protect company 'secrets': Report | CSO Online
52% of CISOs in the US and UK are unable to fully secure their company secrets according to a report by a code security platform. This highlights the need for increased data security measures and protection against cyber threats.
#CISO #companysecrets #datasecurity #softcorpremium
Nebulon's TripLine offers ransomware encryption protection for on-prem systems | CSO Online
Nebulon has launched an early warning system called TripLine which helps on-premises systems to identify the precise time and location of a cryptographically based attack. The system is designed to offer ransomware encryption protection and quickly act upon the potential danger of an attack. Nebulon’s smart infrastructure hack provides rapid recovery of data and better observability of attacks in on-premises systems.
#Nebulon #TripLine #ransomware #softcorpremium
Small- and medium-sized businesses: don’t give up on cybersecurity | CSO Online
Small and medium-sized businesses often overlook cybersecurity due to either high costs or complexity. However, in today's hostile environment, every enterprise should be concerned about protection from hackers, phishers, and other bad actors. Leaving cybersecurity as an afterthought can leave SMBs vulnerable to damaging attacks.
#cybersecurity #SMBs #protection #softcorpremium
Why visibility is key to overcoming your security challenges | CSO Online
In an increasingly cloud-based and hybrid work environment, the potential attack surface continues to grow, making it necessary for CISOs to prioritize visibility as a key factor in overcoming security challenges. According to AV-Test, more than 350,000 new malware samples are launched every day. With the sad truth that it is no longer a matter of if but when an organization will be breached, visibility into an organization's security posture is vital for identifying and responding to threats.
#visibility #security #hybridwork #softcorpremium
New ransomware group CACTUS abuses remote management tools for persistence | CSO Online
A new ransomware group called CACTUS has been using remote management tools to gain persistence in enterprise networks over the past two months. The group has been deploying a new ransomware program that has caught the attention of researchers. The attacks involve the abuse of legitimate remote monitoring and management tools, allowing for lateral movement within networks. The CACTUS ransomware group is the latest addition to the growing list of cybercriminal organizations using ransomware to target businesses worldwide.
#ransomware #security #softcorpremium
Facilitating seamless frontline worker collaboration with identity management | CSO Online
Microsoft Security discusses the importance of seamless identity management to facilitate collaboration among frontline workers who play a crucial role in providing essential services to the public. The post highlights the challenges faced by organizations in ensuring secure and efficient collaboration among frontline workers and suggests solutions through identity management systems.
#identitymanagement #collaboration #frontlineworkers #softcorpremium
International security agencies warn of Russian “Snake” malware threat | CSO Online
International security agencies have issued a joint advisory warning about the Snake malware, a sophisticated espionage tool used by Russian cyber actors against their targets. The malware and its variants have been active since at least 2012 and can be used for espionage, data theft, and to disrupt networks. The advisory includes technical details on how the malware works and how to detect it. Security experts advise organizations to update their antivirus software and to be vigilant against suspicious activity on their networks.
#Russian #malware #cybersecurity #softcorpremium
Review your on-prem ADCS infrastructure before attackers do it for you | CSO Online
This blog post emphasizes the importance of reviewing on-premises ADCS infrastructure to identify and address any vulnerabilities before attackers exploit them. It highlights a recent incident of a cyber attack through a weak spot in the SolarWinds Orion software. The article recommends implementing security best practices such as regular patching, conducting vulnerability scans, and enhancing monitoring capabilities to detect any unusual activities. Overall, the post raises awareness about the criticality of maintaining a secure on-premises infrastructure to prevent potential cyber threats.
#ADCS #security #onpremises #softcorpremium
DigiCert’s DigiCert ONE platform now available on Oracle Cloud Infrastructure | CSO Online
Digital trust firm DigiCert has partnered with Oracle to make its cloud-native SaaS platform, DigiCert ONE, available on Oracle Cloud Infrastructure (OCI). DigiCert ONE secures and centrally manages users, devices, servers, documents, and software. The partnership allows for easy deployment and scalability within customers’ single or multi-cloud environments. Companies can use OCI for secure infrastructure, application, and workload management.
#DigiCertONE #OracleCloudInfrastructure #softcorpremium
New Bazel Ruleset Helps Developers Build Secure Container Images
A new Bazel ruleset has been released which will assist developers in creating secure container images. The ruleset helps developers to identify and eliminate vulnerabilities during the build process, ensuring that the final image is secure and free from any known security issues. This is a valuable tool for companies looking to adopt containerization as it helps to mitigate the risks associated with using containers, and ensures that their applications are secure from the outset.
#container #security #BazelRuleset #softcorpremium
7 VPN alternatives for securing remote network access | CSO Online
This blog post provides 7 VPN alternatives for securing remote network access. With the increased need for remote work due to the pandemic, Virtual Private Networks (VPNs) have become a popular choice for organizations to secure their network. However, VPNs may not be suitable for all remote workers due to their bandwidth requirements and potential security risks. The post explores alternative solutions such as cloud-based access, zero-trust network access, and remote desktop access.
#VPN #security #remotenetworkaccess #softcorpremium