Cloud Security & Compliance News for March 28th, 2023
A Weekly post with news from the Security & Compliance community. #cloudsecurity #compliance #news #softcorpremium


Cyberattackers Continue Assault Against Fortinet Devices
The article discusses the ongoing cyberattacks against Fortinet devices and the measures being taken to prevent them.
#cyberattacks #Fortinet #prevention
| View » | Share on Linkedin » | Tweet » | Toot » |

Analyze any URL safely using the Cloudflare Radar URL Scanner
The post describes how to safely analyze any URL using the Cloudflare Radar URL Scanner.
#Cloudflare #Radar
| View » | Share on Linkedin » | Tweet » | Toot » |

How Patch Tuesday Keeps the Beat After 20 Years
The post discusses the history and significance of Patch Tuesday, a monthly release of security updates by Microsoft, which has been ongoing for 20 years.
#PatchTuesday #MicrosoftSecurityUpdates
| View » | Share on Linkedin » | Tweet » | Toot » |

Trustwave teams up with Trellix for better managed security
Managed cybersecurity vendor Trustwave has partnered with Trellix to offer a combined XDR/MDR offering, which allows end user companies to offload key parts of their security setups. The integration of XDR technology can help companies to correlate security events and separate false alarms from actual threats.
#cybersecurity #XDR #MDR
| View » | Share on Linkedin » | Tweet » | Toot » |

Gain flexibility and scale with a cloud-native DLP solution
The post discusses the three stages of migrating to cloud-based data loss prevention (DLP) and provides insights on overcoming challenges to create a scalable, holistic DLP solution. It also highlights the benefits of using a cloud-native DLP solution for increased flexibility and scalability.
#cloud-based #DLP #scalability
| View » | Share on Linkedin » | Tweet » | Toot » |

Cybercriminals target SVB customers with BEC and cryptocurrency scams
Cybercriminals are taking advantage of Silicon Valley Bank's downfall to carry out scams that can steal money or infect customers systems with malware. SVB customers are expected to transfer their financial operations to other banks in the coming weeks, which hackers are using as an opportunity for phishing and business email compromise campaigns.
#Cybercriminals #SiliconValleyBank
| View » | Share on Linkedin » | Tweet » | Toot » |
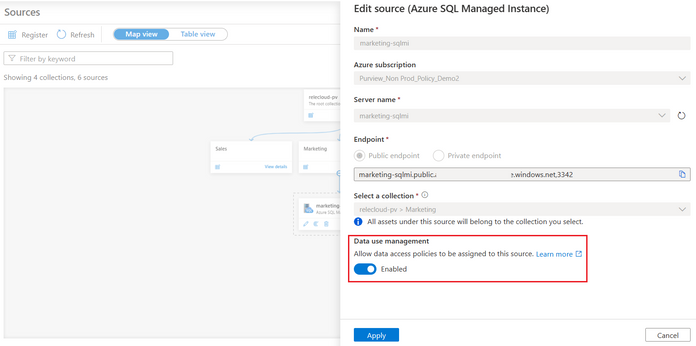
Enable IT personnel to monitor SQL health and performance while reducing the insider risk
The article discusses the risks associated with IT personnel having high privileges such as SQL sysadmin while monitoring database systems and how Microsoft Purview DevOps policies support the Principle of Least Privilege (PoLP) to minimize these risks. It also highlights the experience for Azure SQL Managed Instance, the newest source supported for DevOps policies (now in private preview), and provides configuration steps.
#ITpersonnel #MicrosoftPurview #DevOps
| View » | Share on Linkedin » | Tweet » | Toot » |

Telerik Bug Exploited to Steal Federal Agency Data, CISA Warns
CISA warns that a Telerik bug has been exploited to steal data from federal agencies.
#CISA #Telerik
| View » | Share on Linkedin » | Tweet » | Toot » |

How sophisticated scammers and phishers are preying on customers of Silicon Valley Bank
Threat actors use current events as bait to deceive victims, with Silicon Valley Bank being the latest target. It is important to be aware of phishing campaigns using SVB as a lure and remain vigilant.
#phishing #SVB
| View » | Share on Linkedin » | Tweet » | Toot » |

Be threat ready for 2023: Join us for Google Cloud Security Talks in March
Google Cloud is hosting a quarterly digital discussion event, Google Cloud Security Talks, where experts from the industry come together to share insights and best practices on cloud-scale security. The first installment on March 22 will focus on transforming security with frontline intelligence and the latest security products from Google Cloud.
#GoogleCloud #CloudSecurityTalks
| View » | Share on Linkedin » | Tweet » | Toot » |

Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principles
Beyond Identity has launched Zero Trust Authentication, a sub-category of zero trust security that aligns verification with zero-trust principles and includes passwordless capability and phishing resistance to verify identities with zero-trust-level certainty.
#ZeroTrustAuthentication #passwordless
| View » | Share on Linkedin » | Tweet » | Toot » |

SMBs Orgs Want Help, but Cybersecurity Expertise Is Scarce
The post discusses the challenges faced by small and medium-sized businesses in finding cybersecurity experts to help them protect their organizations.
#cybersecurity #SMBs
| View » | Share on Linkedin » | Tweet » | Toot » |

Palo Alto announces new SD-WAN features for IoT security, compliance support
Palo Alto has added SD-WAN features to its Prisma SASE solution for IoT device security and announced advanced URL filtering to prevent unknown and evasive MitM and SaaS platform phishing attacks.
#IoT #MitM
| View » | Share on Linkedin » | Tweet » | Toot » |

Announcing Cloudflare Fraud Detection
Cloudflare has released a new feature for detecting fraud on their platform.
#Cloudflare #fraud
| View » | Share on Linkedin » | Tweet » | Toot » |

DirectDefense Reports the Top Threats From 2022 and What's Trending for 2023
DirectDefense presents its report on the top threats observed in 2022 and provides insights into what to expect in terms of security trends for 2023.
#DirectDefense #securitytrends
| View » | Share on Linkedin » | Tweet » | Toot » |
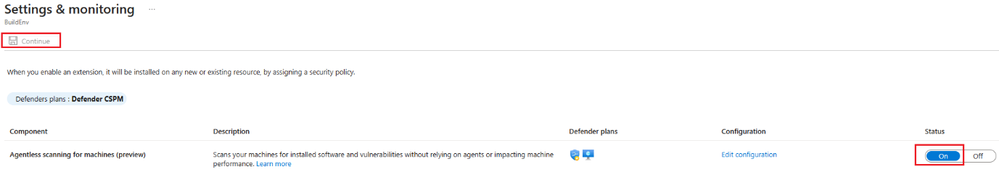
Microsoft Defender PoC Series – Defender CSPM
This post provides guidelines on how to perform a proof of concept for Microsoft Defender for Cloud Plans, specifically focusing on Cloud Security Posture Management. It also highlights the two plans offered by Defender CSPM and suggests various use case scenarios that can be validated during the PoC.
#MicrosoftDefender #CloudSecurityPostureManagement
| View » | Share on Linkedin » | Tweet » | Toot » |

Are we Doing Enough to Protect Our Unstructured Data?
The post discusses the importance of protecting unstructured data and questions whether enough is being done to ensure its security.
#unstructureddata #security
| View » | Share on Linkedin » | Tweet » | Toot » |
Detecting API abuse automatically using sequence analysis
The post discusses the automatic detection of API abuse through sequence analysis.
#APIabuse #sequenceanalysis
| View » | Share on Linkedin » | Tweet » | Toot » |
New Azure Marketplace offer from MISA member DeepSurface
The Microsoft Intelligent Security Association is a group of software vendors and security providers that have integrated their solutions to better defend against threats. MISA partner DeepSurface offers an automated vulnerability insights platform, DeepSurface Risk Analyzer, in the Azure Marketplace.
#MicrosoftIntelligentSecurityAssociation #DeepSurfaceRiskAnalyzer
| View » | Share on Linkedin » | Tweet » | Toot » |
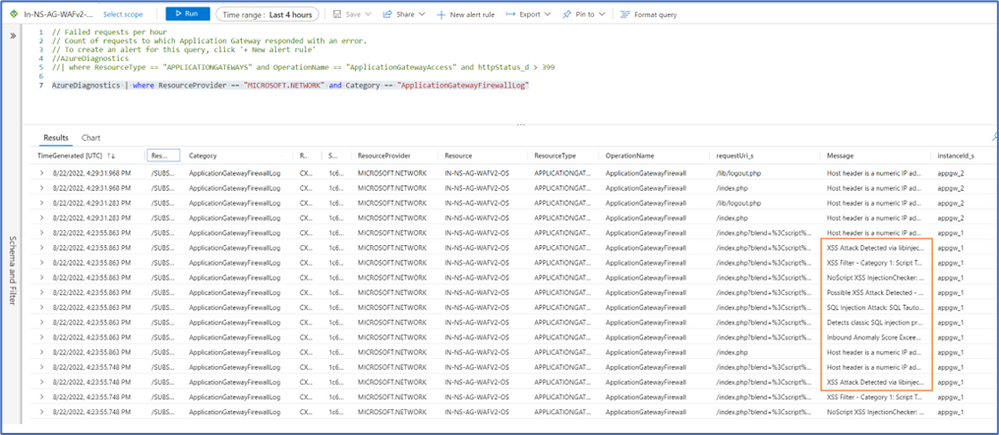
Protect Applications in Google Cloud Platform (GCP) using Azure WAF
This blog provides the steps to deploy a sample coffeeshop application in GCP and implement Azure Web Application Firewall (WAF) for centralized protection against common exploits and vulnerabilities. The post includes instructions on how to restrict access to the application and test for SQL injection and XSS attacks.
#GCP #Azure
| View » | Share on Linkedin » | Tweet » | Toot » |

Catch Defender Experts for Hunting on the Ninja Show
Microsoft Defender Experts for Hunting is a managed service that provides access to highly skilled security experts and industry-leading threat intelligence. The service offers proactive threat hunting across Microsoft 365 Defender data to identify emerging attack patterns and prioritize significant threats.
#MicrosoftDefender #ThreatHunting
| View » | Share on Linkedin » | Tweet » | Toot » |

Why Security Practitioners Should Understand Their Business
The post discusses the importance of security practitioners having a deep understanding of their organization's business operations.
#security #businessoperations
| View » | Share on Linkedin » | Tweet » | Toot » |
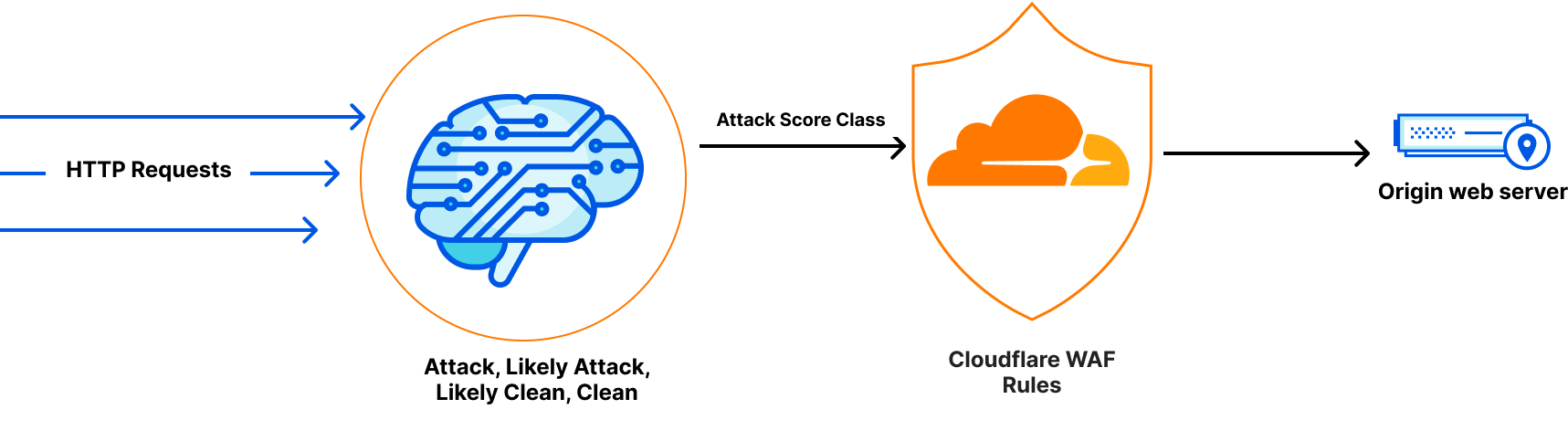
Announcing WAF Attack Score Lite and Security Analytics for business customers
The post announces the release of WAF Attack Score Lite and Security Analytics for business customers.
#WAF #SecurityAnalytics
| View » | Share on Linkedin » | Tweet » | Toot » |

Meet Data Privacy Mandates With Cybersecurity Frameworks
The post discusses the use of cybersecurity frameworks as a way to comply with data privacy mandates.
#cybersecurity #frameworks
| View » | Share on Linkedin » | Tweet » | Toot » |

Dell beefs up security portfolio with new threat detection and recovery tools
Dell Technologies has expanded its security portfolio in areas such as threat security, management, and incident response through in-house and partnered capabilities, including an upgrade to its MDR platform and a partnered threat management solution with CrowdStrike.
#security #MDR #threatmanagement