Cloud Security & Compliance News for March 13th, 2023
A Weekly post with news from the Security & Compliance community. #cloudsecurity #compliance #news #softcorpremium


The Role of Verifiable Credentials In Preventing Account Compromise
Verifiable Credentials are increasingly being used as a way to protect user accounts from malicious actors. This technology provides an additional layer of security that helps to prevent account compromise.
#VerifiableCredentials #CyberSecurity #AccountProtection
| View » | Share on Linkedin » | Tweet » | Toot » |

How CISOs can do more with less in turbulent economic times
Nicole Darden Ford, the CISO at Rockwell Automation, has experience dealing with limited resources having once successfully managed a transition to remote working in her previous company during a period of economic uncertainty. She is now prepared to help her current clients navigate the global pandemic.
#RemoteWorking #CISO #GlobalPandemics
| View » | Share on Linkedin » | Tweet » | Toot » |

International Women’s Day: The power of diversity to build stronger cybersecurity teams
The Microsoft Security Blog highlights the celebration of International Women's Day and emphasizes their commitment to promoting women in cybersecurity. The post stresses the importance of diversity in building stronger cybersecurity teams.
#MicrosoftSecurityBlog #WomenInCybersecurity #DiversityInCybersecurityTeams
| View » | Share on Linkedin » | Tweet » | Toot » |

Announcing new security and observability features in Azure Database for PostgreSQL
Azure Database for PostgreSQL Flexible Server has recently released features that provide better security, credential management and control over databases. These include the general availability of Azure Active Directory authentication and customer managed keys encryption.
#AzureDBforPostgreSQL #AzureActiveDirectory #CustomerManagedKeys
| View » | Share on Linkedin » | Tweet » | Toot » |

PayPal sued for negligence in data breach that affected 35,000 users
A class action lawsuit has been filed against PayPal for failing to protect its users' personal information from a data breach that affected nearly 35,000 people late last year. The cyberattack reportedly happened between December 6 and 8 of 2022.
#DataBreach #Paypal #ClassActionLawsuit
| View » | Share on Linkedin » | Tweet » | Toot » |
![]()
New CISO appointments, February 2023
With the ever-changing threat landscape, companies are hiring chief security and information security officers for the first time. This article provides insight into the new appointments to senior-level security roles and is a source for keeping up with hiring trends.
#CyberSecurity #Infosec #HiringTrends
| View » | Share on Linkedin » | Tweet » | Toot » |

Rising Public Cloud Adoption Is Accelerating Shadow Data Risks
The rapid adoption of public cloud services is creating an increased risk of shadow data, which can lead to security and compliance issues. Organizations need to be aware of these risks and take steps to mitigate them in order to protect their data.
#CloudSecurity #DataManagement #Compliance
| View » | Share on Linkedin » | Tweet » | Toot » |
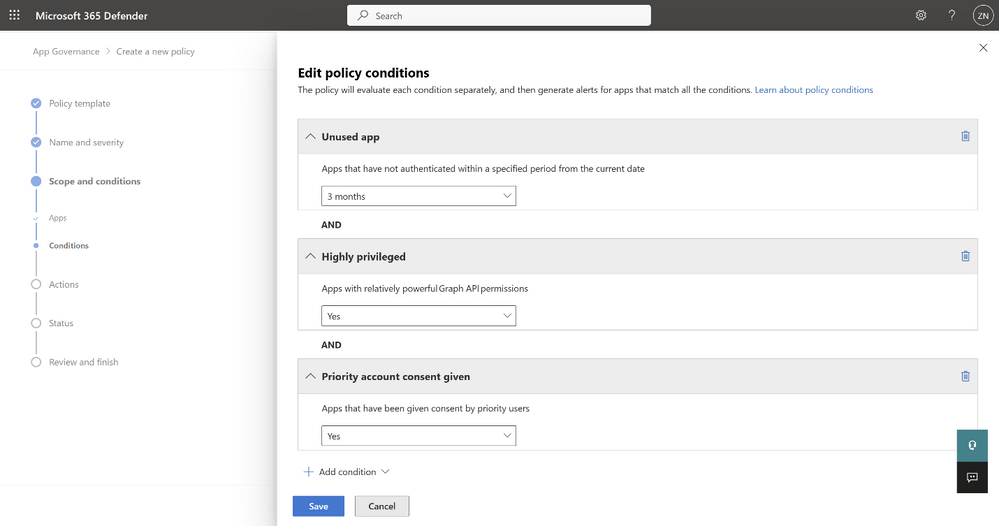
Improve your app posture and hygiene using Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps has shifted to a comprehensive SaaS Security solution to help organizations manage the growing number of apps and ensure they are configured securely. The expanded SSPM capabilities in Defender for Cloud Apps are now in public preview, including App Hygiene features which provide deeper visibility and automatically identify misconfigurations.
#MicrosoftDefender #CloudApps #SaaSSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |
ManageEngine Launches Security and Risk Posture Management in its SIEM Solution
ManageEngine has released a new feature in its SIEM solution, Security and Risk Posture Management, to help organizations strengthen their security posture. The feature provides enhanced visibility and control over their IT infrastructure to protect against threats.
#ManageEngine #SIEM #SecurityPosture
| View » | Share on Linkedin » | Tweet » | Toot » |
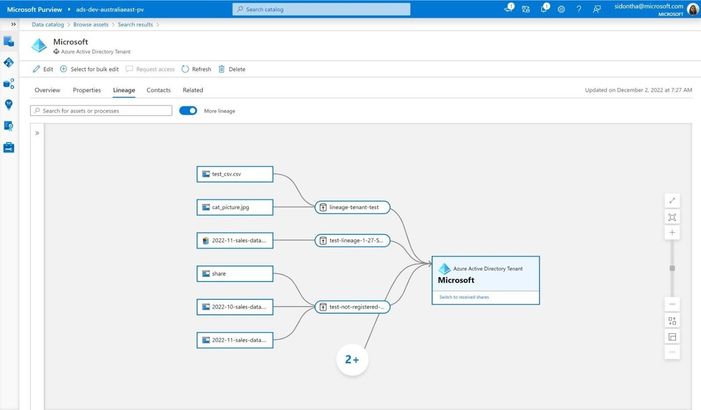
Data Sharing Lineage and search for Azure Storage in-place sharing in Microsoft Purview
Microsoft Purview has added new capabilities such as Data Sharing Lineage and Catalog integration to its public preview of in-place sharing for Azure Blob and Data Lake Storage (ADLS Gen2) data. Users can now search for and manage shares from data share assets and AAD tenant assets in the Microsoft Purview Catalog, view the Data Sharing Lineage within and across organizations/AAD tenants, and navigate to different entities on the lineage canvas.
#MicrosoftPurview #DataSharingLineage #AzureBlobandDataLakeStorage
| View » | Share on Linkedin » | Tweet » | Toot » |

Protecting Android clipboard content from unintended exposure
Microsoft recently found that the Android application 'SHEIN' was accessing and sending data from the Android device clipboard to a remote server. Microsoft Security Blog has released a post about how to protect Android clipboard content from being exposed unintentionally.
#MicrosoftSecurity #AndroidClipboard #SHEIN
| View » | Share on Linkedin » | Tweet » | Toot » |
Azure Synapse Data Explorer enterprise readiness - Part 1: Keeping your data safe
This post is part one of an Enterprise readiness series for Azure Synapse Data Explorer. It focuses on the built-in mechanisms to safeguard data and the importance of operational security in protecting the data. The post also recommends regular auditing of security principals and setting expiration dates on privileged accounts.
#Azure #Synapse
| View » | Share on Linkedin » | Tweet » | Toot » |

Empower growth with full-stack data security
In late 2016, global internet traffic finally reached the Zettabyte threshold that analysts had been projecting for a decade, indicating the importance of data. The Economist reported on the need for full-stack data security to enable growth.
#data #security
| View » | Share on Linkedin » | Tweet » | Toot » |
2022 H2 IRAP report is now available on AWS Artifact for Australian customers
Amazon Web Services has released a new Information Security Registered Assessors Program report, which was completed by an independent Australian Signals Directorate certified assessor in December 2022. This report includes six additional AWS services that were not previously assessed.
#AmazonWebServices #InformationSecurity #RegisteredAssessorsProgram
| View » | Share on Linkedin » | Tweet » | Toot » |

GitHub begins 2FA rollout for code contributors
GitHub is rolling out two-factor authentication for developers who contribute code to enhance account and software supply chain security. Users can choose their preferred 2FA method, and the rollout follows the White House National Cybersecurity Strategy that puts responsibility on software vendors to secure the software ecosystem.
#GitHub #2FA
| View » | Share on Linkedin » | Tweet » | Toot » |

NIST's Quantum-Proof Algorithm Has a Bug, Analysts Say
Analysts have reported a bug in NIST's quantum-proof algorithm, which could potentially affect its security. Researchers are now working to fix the issue before it can be exploited by malicious actors.
#QuantumSecurity #NIST #BugFixing
| View » | Share on Linkedin » | Tweet » | Toot » |

Inside Threat: Developers Leaked 10M Credentials, Passwords in 2022
The post discusses how 10 million credentials and passwords were leaked by developers as an inside threat in the year 2022.
#insideThreat #passwordLeak
| View » | Share on Linkedin » | Tweet » | Toot » |
How to Set up Identity Platform multi-tenancy?
The post describes the advantages of Identity Platform multi-tenancy, which allows multiple organizations to share resources while maintaining their own unique requirements and data privacy. Multi-tenancy provides cost savings, scalability, security, and customization, and allows each organization to establish a data isolation boundary with its own unique identifier, users, identity providers, auditing, and IAM configuration.
#IdentityPlatform #multitenancy #IAMconfiguration
| View » | Share on Linkedin » | Tweet » | Toot » |
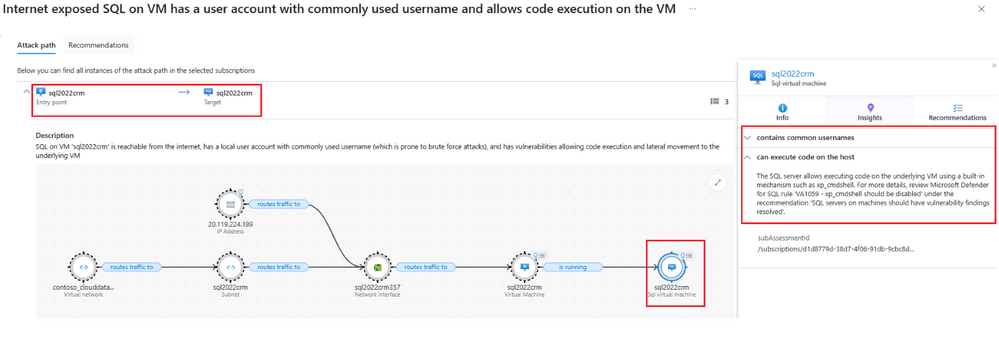
Prioritize Risk remediation with Microsoft Defender for Cloud Attack Path Analysis
Security teams can use Microsoft Defender for Cloud Attack Path Analysis to prioritize risk remediation efforts and improve their overall security posture. Attack path analysis can be used for risk remediation by identifying the attack paths, analyzing the risks and mapping out the various components of the system.
#MicrosoftDefender #CloudSecurity #AttackPathAnalysis
| View » | Share on Linkedin » | Tweet » | Toot » |
![]()
Tracking device technology: A double-edged sword for CISOs
The transportation industry has increased its use of fleet tracking recently, resulting in both positive and negative implications. Google is now entering the market with their own device codenamed Grogu, showing potential to pose a serious challenge to cybersecurity leaders.
#FleetTracking #CyberSecurity #GooglesGrogu
| View » | Share on Linkedin » | Tweet » | Toot » |

Municipal CISOs grapple with challenges as cyber threats soar
The City of Oakland, California declared a state of emergency after being hit by a ransomware attack on February 10. As of February 24, many city services were still down, including the 311 system, just as a severe winter storm bore down on the area.
#Oakland #RansomwareAttack #WinterStorm
| View » | Share on Linkedin » | Tweet » | Toot » |

3 Ways Security Teams Can Use IP Data Context
Security teams can use IP data context to gain greater visibility into their networks and identify potential threats. Additionally, it can help them better understand user behavior and network activity for improved security monitoring.
#NetworkSecurity #NetworkActivity #ThreatMonitoring
| View » | Share on Linkedin » | Tweet » | Toot » |
Okta SAML Integration with AWS IAM Step 2: AWS IAM Identity Provider
This post looks at how to configure an Identity Provider (IdP) in AWS for Okta using CloudFormation. It's part of a series on automating cybersecurity metrics and also contains information about cloud security training and penetration testing.
#CloudSecurity #AWS #Okta
| View » | Share on Linkedin » | Tweet » | Toot » |
Cloud Threats Memo: Multiple Different Cloud Apps Abused in a Single Cyber Espionage Campaign
Researchers at Sentinel One and QGroup have recently discovered a cyber espionage campaign, conducted by a threat cluster called WIP26, which targets telecommunication providers in the Middle East. This campaign stands out for its abuse of multiple cloud services.
#CyberEspionage #WIP26 #CloudServices
| View » | Share on Linkedin » | Tweet » | Toot » |

Hard-coded secrets up 67% as secrets sprawl threatens software supply chain
According to GitGuardian's State of Secrets Sprawl 2023 report, the number of detected hard-coded secrets increased by 67% last year with 10 million new secrets discovered in public GitHub commits. Hard-coded secrets pose significant security risks as they are often stored in plain text.
#GitGuardian #SecretsSprawl2023 #SecurityRisks
| View » | Share on Linkedin » | Tweet » | Toot » |
Automate your alert response actions in Microsoft 365 Defender
Microsoft 365 Defender's XDR solution helps security teams prioritize response activities and provides a unified experience for more effective investigation. Automation is also growing in importance to close the gap between attack speed and response time, allowing for automatic response actions to be set up for built-in alerts in Microsoft 365 Defender.
#Microsoft365Defender #XDR #Automation
| View » | Share on Linkedin » | Tweet » | Toot » |

Akamai releases new threat hunting tool backed by Guardicore capabilities
Akamai has launched Akamai Hunt, a visibility tool that combines their historic data with Guardicore's network segmentation and visualization capabilities to provide customers with the ability to identify and remediate threats and risks in their cloud environments. Akamai acquired Guardicore for approximately $600 million back in October 2022.
#Akamai #Guardicore #CloudSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

What is zero trust? A model for more effective security
Security leaders are increasingly embracing zero trust, with the percentage of organizations with a zero-trust initiative in place more than tripling since 2018. The latest State of Zero-Trust Security report found that 55% of those surveyed had already implemented a zero-trust strategy or planned to do so within 18 months.
#ZeroTrust #SecurityLeaders #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |
Palo Alto Survey Reveals 90% of Organizations Cannot Resolve Cyberthreats Within an Hour
A survey conducted in Palo Alto has revealed that 90% of organizations are unable to address cyberthreats within an hour. This indicates a lack of preparedness against potential security threats.
#cybersecurity #cyberthreats #preparedness
| View » | Share on Linkedin » | Tweet » | Toot » |

BrandPost: Is Your XDR Strategy Incomplete?
XDR is a strategy, rather than a product, that combines security-related telemetries with high-fidelity detections in order to deliver faster and more effective incident response. There are two main approaches to XDR: proprietary and open strategies, both of which involve multiple types of products and vendors.
#XDR #IncidentResponse #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Targeted Threat Intelligence for Security Operations
Organizations are recognizing that more sophisticated online security measures are necessary to protect against the ever-evolving threat posed by malicious actors. Threat intelligence is becoming an essential component in any comprehensive digital defense strategy.
#ThreatIntelligence #CyberSecurity #DigitalDefense
| View » | Share on Linkedin » | Tweet » | Toot » |

How to improve your Kubernetes security posture with GKE Dataplane V2 network policies
Organizations are increasingly adopting a defense-in-depth strategy to protect their applications and data from threats, taking advantage of GKE Dataplane V2 which integrates eBPF to provide consistent network policy enforcement, logging and monitoring.
#GKEDataplaneV2 #eBPF #DefenseInDepth
| View » | Share on Linkedin » | Tweet » | Toot » |
Securing a successful merger: Insights from MGM Studios
MGM Studios has recently provided insights into the process of securing a successful merger. This information is invaluable to those looking to navigate the complexities of merging two companies.
#Merger #BusinessStrategy #MGMStudios
| View » | Share on Linkedin » | Tweet » | Toot » |

Critical RCE Bug Opens Fortinet's Secure Web Gateway to Takeover
The post discusses a critical Remote Code Execution (RCE) vulnerability in Fortinet's Secure Web Gateway that allows an attacker to take over the system.
#RemoteCodeExecution #FortinetSecureWebGateway
| View » | Share on Linkedin » | Tweet » | Toot » |

White House releases an ambitious National Cybersecurity Strategy
The White House released its National Cybersecurity Strategy, a document that outlines changes in how the US handles cybersecurity. It was crafted with input from more than 20 government agencies and private sector organizations and covers a wide range of topics related to cybersecurity.
#NationalCybersecurityStrategy #Cybersecurity #USSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |
Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender
Microsoft 365 Defender has announced the expansion of automatic attack disruption public preview to cover business email compromise (BEC) campaigns, in addition to human-operated ransomware (HumOR), to help Security Operations (SOC) teams address the ever-growing volume of advanced cybersecurity attacks. This game-changing capability leverages high-confidence Extended Detection and Response (XDR) signals to contain active cybersecurity attacks quickly and effectively, stopping progression and limiting the impact to organizations.
#Microsoft365Defender #BEC #HumOR #XDR
| View » | Share on Linkedin » | Tweet » | Toot » |
Securely save files from Microsoft Edge to OneDrive on mobile devices
Microsoft Edge mobile app now allows users to securely download and save files from the app to OneDrive, offering a simple solution for users to save, access, and share files while respecting enterprise security parameters. Users need to log on to the Edge mobile app with their Azure AD accounts and Intune admins need to assign Intune App Protection Policy (APP) to users in order to use this feature.
#MicrosoftEdge #OneDrive #EnterpriseSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Hacker Cracks Toyota Customer Search Tool
The hacker was able to gain access to Toyota's customer search tool, successfully cracking the system. This gave them access to confidential customer information stored within the database.
#CyberSecurity #DataSecurity #Toyota
| View » | Share on Linkedin » | Tweet » | Toot » |

Medusa Gang Video Shows Minneapolis School District's Ransomed Data
A video released by the Medusa Gang showcases how they were able to ransom the Minneapolis School District's data.
#MedusaGang #MinneapolisSchoolDistrict
| View » | Share on Linkedin » | Tweet » | Toot » |
Forrester Study Reveals Businesses Are Insufficiently Prepared to Manage Enterprise Risks
The post discusses the findings of a Forrester study that highlights the lack of preparedness among businesses to manage enterprise risks.
#Forrester #enterpriserisks
| View » | Share on Linkedin » | Tweet » | Toot » |

GitHub 2FA campaign begins
GitHub will begin phasing in two-factor authentication (2FA) requirements for developers contributing code to the site, affecting millions of developers. All developers will be required to comply by the end of the year, with smaller groups being enrolled first and given 45 days to configure 2FA on their accounts.
#GitHub #2FA
| View » | Share on Linkedin » | Tweet » | Toot » |

How LTIMindtree Solves for Cross-Account Sensitive Data Sharing Using AWS Services
The article discusses the need for organizations to implement data governance in order to protect personally identifiable information. It also highlights a modern process introduced by LTIMindtree that uses AWS Step Functions to transfer and share transformed data securely across different regions.
#DataGovernance #AWSStepFunctions #SecureDataTransfer
| View » | Share on Linkedin » | Tweet » | Toot » |
GCP Workload Identity Federation with Azure
Users must have sufficient permissions to register an application with their Azure AD tenant and assign a role in their Azure subscription in order to implement workload identity federation, allowing Azure workloads to authenticate with Google Cloud Platform without the need for a service account key. Managed identities can also be used to get an Azure Active Directory token for applications.
#AzureAD #WorkloadIdentityFederation #ManagedIdentities
| View » | Share on Linkedin » | Tweet » | Toot » |
Surge in Cloud Adoption Means a Greater Data Attack Surface for Healthcare and Financial Services
The healthcare and financial services industries have seen a dramatic increase in cloud adoption, resulting in a larger attack surface for potential data breaches. This has caused organizations to take extra precautions to protect their sensitive information.
#CloudAdoption #DataBreaches #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Public Preview: Data sharing lineage and search for Azure Storage in Microsoft Purview
Microsoft Edge is the recommended browser to take advantage of the latest features, security updates and technical support. Data Sharing Lineage is now available in Microsoft Purview in public preview for Azure Data Lake Storage (ADLS) Gen2 and Azure Blob (Blob) Storage.
#MicrosoftEdge #DataSharingLineage #Purview
| View » | Share on Linkedin » | Tweet » | Toot » |

Lazarus group infiltrated South Korean finance firm twice last year
The Lazarus group exploited a zero-day vulnerability in an unnamed software twice last year to infiltrate a South Korean finance firm, according to research by AhnLab Security Emergency Response Center. ASEC reported the vulnerability to the Korean Internet and Security Agency, but the affected software has not been named.
#Lazarus #cybersecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

BrandPost: Protecting yourself from DDoS attacks
Microsoft Security has identified Distributed Denial-of-Service (DDoS) attacks as a major threat to enterprise businesses. Malware infected devices or networks of devices can generate large volumes of traffic to overwhelm websites or services, resulting in long-term disruption.
#MicrosoftSecurity #DDoS #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

CISA, MITRE Look to Take ATT&CK Framework Out of the Weeds
The Cybersecurity and Infrastructure Security Agency (CISA) and The MITRE Corporation are working together to make the ATT&CK framework more accessible and easier to use. This collaboration is aimed at taking the ATT&CK Framework out of the weeds, making it more widely applicable.
#Cybersecurity #CISA #MITRE #ATTACKFramework
| View » | Share on Linkedin » | Tweet » | Toot » |

Celebrating Women in Cybersecurity | International Women’s Day 2023
This event is celebrating the accomplishments of women in the field of cybersecurity, and is being held on International Women's Day 2023. It aims to recognize the contributions of women to the industry and encourage more diversity in the workforce.
#IWD2023 #Cybersecurity #WomenInTech
| View » | Share on Linkedin » | Tweet » | Toot » |
99% of Cybersecurity Leaders Are Stressed About Email Security
Cybersecurity leaders are feeling an immense amount of stress related to the security of their email systems. Almost all of them have expressed concern about potential threats posed by email vulnerabilities.
#Cybersecurity #EmailSecurity #Threats
| View » | Share on Linkedin » | Tweet » | Toot » |

Emotet Resurfaces Yet Again After 3-Month Hiatus
The Emotet malware has returned after a 3-month break, with new tactics and evasion techniques.
#Emotet #malware
| View » | Share on Linkedin » | Tweet » | Toot » |
The White House’s National Cybersecurity Strategy asks the private sector to step up to fight cyber attacks. Cloudflare is ready.
The White House has issued a National Cybersecurity Strategy, calling on the private sector to join the fight against cyber attacks. Cloudflare is among the companies that have responded positively to the call for action.
#Cybersecurity #NationalCybersecurityStrategy #Cloudflare
| View » | Share on Linkedin » | Tweet » | Toot » |

HPE to acquire Axis Security to deliver a unified SASE offering
HPE has acquired Axis Security to incorporate its SSE platform into its edge-to-cloud security capabilities, aiming to offer integrated networking and security solutions as-a-service following the hybrid work environment that has become the new normal. Phil Mottram of HPE Aruba Networking stated that a new approach is needed for network edge security to protect critical SaaS applications.
#HPE #ArubaNetworking #EdgeToCloudSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Biden's Cybersecurity Strategy Calls for Software Liability, Tighter Critical Infrastructure Security
Joe Biden has proposed a cybersecurity strategy that calls for software liability and increased security measures for critical infrastructure. The strategy seeks to ensure the safety of digital systems from malicious actors.
#CybersecurityStrategy #SoftwareLiability #CriticalInfrastructure
| View » | Share on Linkedin » | Tweet » | Toot » |

Acer Confirms Data Offered Up for Sale Was Stolen
Acer has confirmed that the data offered up for sale was stolen from their systems, and is currently investigating the incident. They are taking steps to mitigate any potential damage resulting from the breach.
#Acer #DataBreach #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Get integrated Microsoft Purview Information Protection in Adobe Acrobat—now available
Adobe and Microsoft have announced a collaboration to provide customers with modern work experiences. Organizations using Microsoft Purview Information Protection now have the ability to apply and edit sensitivity labels and policies to PDFs.
#Adobe #Microsoft #PurviewInformationProtection
| View » | Share on Linkedin » | Tweet » | Toot » |

The benefits of a customer-centric cloud security mindset
A customer-centric cloud security mindset can provide many advantages, such as increased efficiency and improved customer experience. It is an approach that focuses on the needs of customers when developing cloud security strategies.
#CloudSecurity #CustomerExperience #CustomerCentricity
| View » | Share on Linkedin » | Tweet » | Toot » |

Attack campaign uses PHP-based infostealer to target Facebook business accounts
Morphisec researchers have reported a campaign in which attackers target Facebook business account owners by spreading malware through malicious Google ads or fake Facebook profiles. The malware is designed to steal sensitive information, including login data, cookies, and Facebook ad and business account information.
#CyberSecurity #FacebookSecurity #Malware
| View » | Share on Linkedin » | Tweet » | Toot » |
Information Barriers v2 is now generally available for all new onboarding customers
Microsoft has released Microsoft Purview Information Barriers v2 (IB v2) which includes enhanced architecture and new features such as large-scale segment support, multi-segment support, and flexible user discoverability. IB v2 allows organizations to meet compliance requirements while enabling communication and collaboration across internal regulated users.
#MicrosoftPurview #InformationBarriers #ComplianceRequirements
| View » | Share on Linkedin » | Tweet » | Toot » |

Machine Learning Improves Prediction of Exploited Vulnerabilities
Use of Machine learning to enhance the prediction of exploited vulnerabilities in cybersecurity can help identify and prioritize vulnerabilities that are more likely to be exploited, allowing organizations to focus on securing their most critical assets.
#MachineLearning #PredictiveAnalysis #VulnerabilityPrediction
| View » | Share on Linkedin » | Tweet » | Toot » |
[Coming soon] Microsoft Sentinel out-of-the-box content centralization!
Microsoft Sentinel is centralizing its out-of-the-box (OOTB) content and solutions in the content hub to allow customers to easily manage packaged solutions for SOC use cases. Changes are coming soon in Q2 FY23 to complete OOTB content centralization, retiring legacy gallery content templates and providing a central tool to reinstate IN USE retired templates from corresponding content hub solutions.
#MicrosoftSentinel #OOTB #SOCusecases
| View » | Share on Linkedin » | Tweet » | Toot » |

BlackLotus Bookit Found Targeting Windows 11
BlackLotus Bookit is a malicious software targeting Windows 11 operating systems. It has the potential to cause significant damage to vulnerable systems.
#BlackLotus #Bookit #Windows11
| View » | Share on Linkedin » | Tweet » | Toot » |

Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Employees are using ChatGPT to share sensitive business data, which is raising concerns about security risks. Companies are now faced with the challenge of ensuring that data remains secure while employees are using the platform.
#ChatGPT #DataSecurity #BusinessData
| View » | Share on Linkedin » | Tweet » | Toot » |

New Chinese regulatory body expected to streamline data governance rules
China is creating a new data regulation body to clarify and establish data sovereignty rules for multinational companies. The body will streamline data governance policies in the country.
#China #dataregulation
| View » | Share on Linkedin » | Tweet » | Toot » |

XPeng In-car App Requires User Facial Recognition Using Outside Camera
XPeng has developed an in-car app that requires users to use facial recognition technology with an outside camera. This technology is designed to provide a more secure and efficient experience for XPeng drivers.
#FacialRecognition #XPeng #SecureDriving
| View » | Share on Linkedin » | Tweet » | Toot » |
Monthly news - March 2023
Microsoft Defender for Cloud released various new assets, including product videos, webcasts, and improved version of the cloud security explorer in February 2023. It also added a new community workbook "Active Recommendations" to its library, as well as a guide on how to use Security Explorer for blob-hunting.
#MicrosoftDefender #CloudSecurity #BlobHunting
| View » | Share on Linkedin » | Tweet » | Toot » |
Avast Introduces Avast One Platinum
Avast One Platinum is a new product offering from Avast that provides comprehensive protection and privacy for all devices.
#AvastOnePlatinum #protection
| View » | Share on Linkedin » | Tweet » | Toot » |

Ransomware's Favorite Target: Critical Infrastructure and Its Industrial Control Systems
Ransomware is a malicious software that has been increasingly targeting critical infrastructure and its industrial control systems. These systems are considered to be particularly vulnerable to ransomware attacks due to their lack of security protocols.
#Ransomware #CriticalInfrastructure #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

US Lawmakers Face Cyberattacks, Potential Physical Harm After DC Health Link Breach
US lawmakers are at risk of cyberattacks and physical harm following a data breach at DC Health Link.
#cyberattacks #physicalharm #dchealthlink
| View » | Share on Linkedin » | Tweet » | Toot » |

Congressional health insurance service hit by data breach
A data breach was discovered in a health insurance marketplace that provides coverage for members of the US Congress and congressional staffers. Personal information for some DC Health Link customers was exposed on a public forum, and credit monitoring services will be provided for all customers.
#dchealthlink #databreach
| View » | Share on Linkedin » | Tweet » | Toot » |
Skill up at Tech Accelerator: Microsoft Intune Suite!
Microsoft Intune Suite is now available, offering advanced endpoint and security management solutions. Microsoft is hosting a two-day virtual skilling event, Tech Accelerator: Microsoft Intune Suite, to provide technical details and features of the suite.
#MicrosoftIntune #TechAccelerator #EndpointSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Key Proposals in Biden's Cybersecurity Strategy Face Congressional Challenges
Key Proposals in Biden's Cybersecurity Strategy Face Congressional Challenges
#Cybersecurity #BidenAdministration #CongressionalChallenges
| View » | Share on Linkedin » | Tweet » | Toot » |
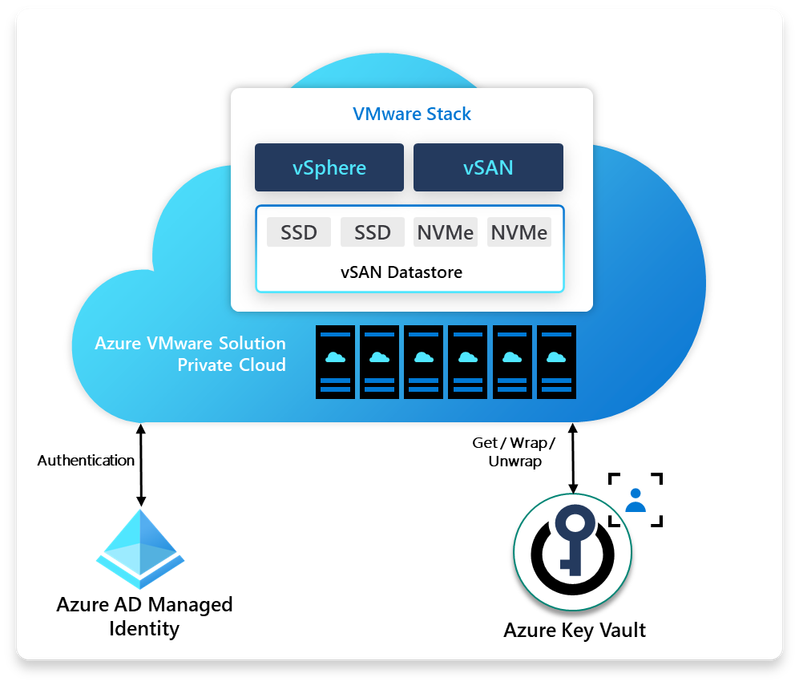
Customer Managed Keys for Azure VMware Solution
Azure VMware Solution now offers customer-managed keys, which enables customers to have maximum control over their encrypted vSAN data. Customers can use Azure Key Vault to generate customer-managed keys and centralize the key management process.
#Azure #VMwareSolution #KeyManagement
| View » | Share on Linkedin » | Tweet » | Toot » |
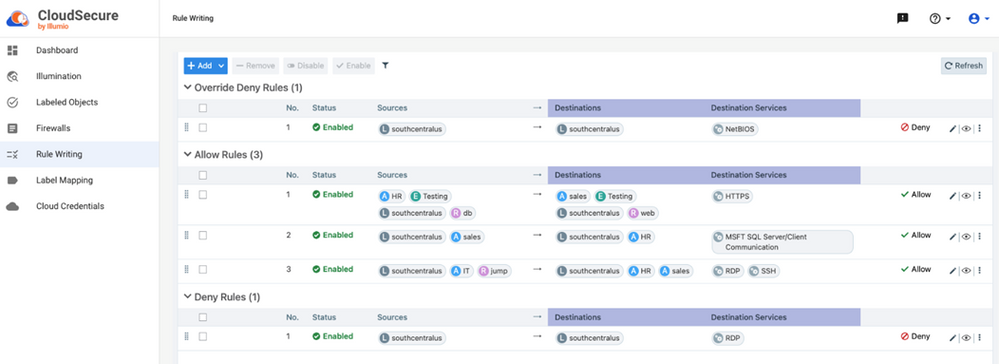
Illumio for Azure Firewall - Combines Benefits of Zero Trust Segmentation and Cloud-Native Firewall
Illumio has partnered with Microsoft to develop an integrated solution, Illumio for Azure Firewall, that enables organizations to understand application traffic and dependencies, and apply consistent protection across their environment. This solution uses the Azure platform to protect resources across Azure virtual networks and at the Azure perimeter, helping organizations to reduce security risks, gain a holistic view of application traffic, and easily deploy and configure Azure application-based policies.
#Illumio #Microsoft #ZeroTrust #AzureFirewall
| View » | Share on Linkedin » | Tweet » | Toot » |
Cyber Counterintelligence (CCI): Offensive & Defensive Strategies for Cybersecurity
Cyber Counterintelligence (CCI) is an approach used by organizations to prevent cyber threats posed by malicious actors. It uses both defensive and offensive techniques to mitigate these threats, such as penetration testing, threat hunting and honeypots.
#CyberCounterintelligence #ThreatHunting #Honeypots
| View » | Share on Linkedin » | Tweet » | Toot » |

Shein Shopping App Glitch Copies Android Clipboard Contents
The SHEIN shopping app was found to have a glitch that allowed it to copy data from users' Android clipboards without their knowledge or consent. The app's developers have since issued a fix for the issue.
#Shein #Shopping #AndroidClipboard
| View » | Share on Linkedin » | Tweet » | Toot » |
Delinea Adds New features for its Privilege Manager and DevOps Secrets Vault
Delinea has recently added new features to its Privilege Manager, allowing users more control over their IT environments. Additionally, it has also released a DevOps Secrets Vault to help facilitate secure storage of credentials.
#DevOps #PrivilegeManager #Security
| View » | Share on Linkedin » | Tweet » | Toot » |

CryptoRom scammers target Twitter, SMS users — Sophos
Sophos has discovered that scammers are using CryptoRom to target Twitter and SMS users. This malicious software is designed to steal personal information and money from unsuspecting victims.
#CyberSecurity #CryptoRom #IdentityTheft
| View » | Share on Linkedin » | Tweet » | Toot » |

BrandPost: Protecting the Edge Is More Important Than Ever
Edge computing is rapidly becoming a key factor in modern technology, with the global market projected to increase by 38.9% from 2022-2030. With its advantages come heightened security risks, making the need for effective protection solutions more crucial than ever.
#EdgeComputing #SecuritySolutions #Technology
| View » | Share on Linkedin » | Tweet » | Toot » |

Gitpod flaw shows cloud-based development environments need security assessments
Snyk researchers recently discovered a vulnerability in Gitpod, a popular cloud development environment, that would have allowed attackers to take over accounts and execute remote code. Organizations should assess security risks associated with cloud-based development environments due to the lack of scrutiny from the security community.
#CloudDevelopment #SecurityRisk #Gitpod
| View » | Share on Linkedin » | Tweet » | Toot » |
GCP-Terraform to deploy Private GKE Cluster.
Published in Google Cloud, GCP-Terraform can be used to deploy a secure GKE (Google Kubernetes Engine) Private Cluster. Nodes in the cluster are assigned with a private IP address, isolating them from inbound and outbound traffic, and can connect to the internet with cloud NAT. Private clusters have the option of exposing both public and private endpoints.
#GCP #GoogleCloud #GKECluster
| View » | Share on Linkedin » | Tweet » | Toot » |

Establishing a data perimeter on AWS: Allow only trusted resources from my organization
The post discusses how companies using Amazon Web Services (AWS) aim to prevent data transfers to or from outside locations to comply with regulatory and privacy agreements as well as for security purposes.
#AWS #datacompliance
| View » | Share on Linkedin » | Tweet » | Toot » |

How to set up least privilege access to your encrypted Amazon SQS queue
Amazon SQS is a fully-managed message queueing service that allows users to decouple and scale various systems, applications and services. It also provides authentication and encryption in transit for added security.
#AmazonSQS #MessageQueueing #Security
| View » | Share on Linkedin » | Tweet » | Toot » |
AWS Key Management Service now supports FIPS 140-2 enabled interface VPC endpoint
AWS Key Management Service (AWS KMS) now allows customers to add a VPC endpoint that connects through the AWS KMS Regional endpoint which has been validated under FIPS 140-2 program, enabling secure connections for workloads that require a FIPS 140-2 validated cryptographic module.
#AWSKMS #FIPS140-2 #VPCEndpoint
| View » | Share on Linkedin » | Tweet » | Toot » |

Microsoft Federal Successfully Completes Voluntary CMMC Assessment
Microsoft successfully completed a DoD DIBCAC Joint Surveillance Voluntary Assessment Program (JSVAP), receiving a perfect 110-point score and will receive a Cybersecurity Maturity Model Certification (CMMC) Level 2 accreditation. Microsoft Federal is committed to providing their customers with the highest standards of quality and security, having implemented specific data handling controls for their Azure Government cloud offerings.
#Microsoft #AzureGovernment #CMMC
| View » | Share on Linkedin » | Tweet » | Toot » |
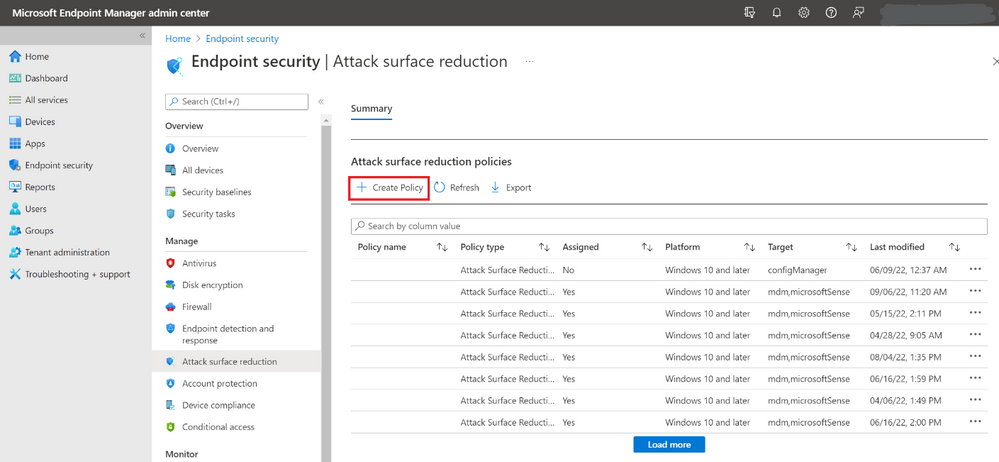
Push ASR rules with Security Settings Management on Microsoft Defender for Endpoint managed devices
Security Settings Management for Microsoft Defender for Endpoint has been expanded to include support for Attack Surface Reduction (ASR) rules, now in public preview. This will enable all Defender for Endpoint managed devices to receive ASR rules via Microsoft Intune.
#MicrosoftDefender #ASRRules #MicrosoftIntune
| View » | Share on Linkedin » | Tweet » | Toot » |
AWS Glue introduces faster and simpler permissions setup
The AWS Glue service has introduced a new guided permissions setup feature in its console. This allows administrators to grant IAM roles and user access to the service and their data, including a default role for running jobs.
#AWSGlue #IAMRoles #DataAccess
| View » | Share on Linkedin » | Tweet » | Toot » |

Remcos RAT Spyware Scurries Into Machines via Cloud Servers
Remcos RAT spyware is a malicious software that infiltrates computers by using cloud servers as an entry point. It then collects sensitive information from the infected machines without the user's knowledge.
#Remcos #RAT #Spyware
| View » | Share on Linkedin » | Tweet » | Toot » |

40% of Global ICS Systems Attacked With Malware in 2022
In 2022, a significant number of industrial control systems (ICS) across the globe were targeted by malware, affecting almost half of all ICS systems worldwide. This attack highlights the growing need for robust cybersecurity measures to protect critical infrastructure.
#ICSsecurity #Cybersecurity #CriticalInfrastructureProtection
| View » | Share on Linkedin » | Tweet » | Toot » |
Risks Using a Third Party Identity Provider with Azure
The US government has warned against using third-party Identity Providers with Azure, and provided a document outlining the risks involved. They recommend researching security related to identity providers for more information.
#Azure #IdentityProviders #Security
| View » | Share on Linkedin » | Tweet » | Toot » |

Wiz enhances its industry leading data security solution with broader cloud data coverage and customizable platform capabilities
Wiz has improved its data security solution by expanding its cloud data coverage and offering customizable platform capabilities.
#Wiz #datasecurity
| View » | Share on Linkedin » | Tweet » | Toot » |
Lacework Launches Secured by Women Initiative
Lacework has announced the launch of their Secured by Women Initiative, which aims to promote and empower female cybersecurity professionals. The initiative will provide professional development resources, community support, and mentorship opportunities for women in security.
#SecuredByWomen #CyberSecurity #WomenInSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Police Raid Rounds Up Core Members of DoppelPaymer Ransomware Gang
The police conducted a raid that resulted in the arrest of several core members of the DoppelPaymer Ransomware Gang. The raid was part of an ongoing investigation into the activities of the criminal organization.
#DoppelPaymer #Ransomware #GangArrest
| View » | Share on Linkedin » | Tweet » | Toot » |
IAM Roles for Amazon EC2 Now Provide Credential Control Properties
AWS has introduced Credential Control Properties, which allow customers to restrict the usage of IAM Roles for EC2 and limit the use of role credentials to only the location from where they originated. These properties are now available in all AWS Regions.
#AWS #IAMRoles #CredentialControl
| View » | Share on Linkedin » | Tweet » | Toot » |

SANS, Google launch academy to promote cloud security, diversity in workforce
The SANS Institute has partnered with Google to launch the SANS Cloud Diversity Academy (SCDA) in order to increase representation of underrepresented groups in the cybersecurity sector. According to reports, only 25% of the cybersecurity workforce globally is comprised of women, and only 9%, 8%, and 4% are Black, Asian, and Hispanic respectively.
#SCDA #CyberSecurity #DiversityInTech
| View » | Share on Linkedin » | Tweet » | Toot » |
SANS Institute Partners With Google to Launch Cloud Diversity Academy
The SANS Institute has announced a partnership with Google to launch the Cloud Diversity Academy, an initiative designed to promote diversity in the cloud computing industry. The academy will provide educational resources and training opportunities for those interested in pursuing careers in cloud computing.
#CloudDiversityAcademy #GoogleCloud #SANSInstitute
| View » | Share on Linkedin » | Tweet » | Toot » |

Iron Tiger updates malware to target Linux platform
Iron Tiger, an APT group, has updated their SysUpdate malware to include new features and support for Linux. Trend Micro researchers found multiple similar payloads in late October 2022 after observing the earliest sample of this version in July 2022.
#SysUpdate #Linux #APTGroup
| View » | Share on Linkedin » | Tweet » | Toot » |

Cado Announces $20M in Funding to Drive Innovation and Global Expansion
Cado Security, a cyber startup, has raised $20M in funding led by Eurazeo to accelerate the transformation of security operations through cloud technology and to support global expansion.
#cyber #startup #funding
| View » | Share on Linkedin » | Tweet » | Toot » |

Indigo Books Refuses LockBit Ransomware Demand
Indigo Books, a major Canadian retailer, has refused to pay the ransom demanded by LockBit ransomware attackers. The company has instead opted to restore their systems from backups rather than comply with the attackers' demands.
#LockBit #Ransomware #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

Cloud trends 2023: Cost management surpasses security as top priority
According to the Flexera 2023 State of the Cloud Report, managing cloud spend has become the top challenge for cloud users, surpassing security which had been the top challenge in past surveys. Additionally, lack of resources or expertise was reported as a top cloud challenge by 78% of respondents.
#CloudSpend #CloudChallenges #CloudSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

What are the biggest cyberthreats heading our way in 2023?
What are the biggest cyberthreats heading our way in 2023?
#CyberSecurity #CyberThreats #2023
| View » | Share on Linkedin » | Tweet » | Toot » |

Hiatus Campaign Infects DrayTek Gear for Cyber Espionage, Proxy Control
The Hiatus Campaign has been infecting DrayTek devices with malicious code for the purpose of cyber espionage and proxy control. This malicious activity has been identified by researchers as part of a larger campaign targeting vulnerable devices around the world.
#CyberEspionage #ProxyControl #MaliciousCode
| View » | Share on Linkedin » | Tweet » | Toot » |
Amazon Aurora MySQL-Compatible Edition now supports Microsoft Active Directory authentication
The Amazon Aurora MySQL-Compatible Edition now enables authentication of database users through Microsoft Active Directory. This can be done by using AWS Directory Service for Microsoft Active Directory or establishing a trusted domain relationship with the on-premise Active Directory.
#AmazonAurora #MySQLCompatible #MicrosoftActiveDirectory
| View » | Share on Linkedin » | Tweet » | Toot » |
Inexpensive solution for managing access to SQL health, performance and security information
Microsoft Purview DevOps policies provide an inexpensive solution to provision access at-scale for IT/DevOps personnel tasked with monitoring and auditing SQL system health, performance, and security. It is integrated with the data map and can help provision user access to data sources and datasets automatically.
#MicrosoftPurview #DevOps #SQL
| View » | Share on Linkedin » | Tweet » | Toot » |
Inspecting and Reporting Sensitive Data with Google Cloud’s DLP API
Zach, a Google Cloud employee, introduces readers to the Google Cloud Data Loss Prevention API, which helps organizations protect their sensitive data. He then explains how it can be used in conjunction with other Google Cloud services to obfuscate and report on this data.
#GoogleCloud #DataLossPrevention #CloudSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |

BrandPost: How 3 Tools Can Revitalize Your Security Strategy
The security industry must shift from a prevention-focused approach to one that emphasizes early detection and response. No matter how sophisticated our security tools are, the constant game of attackers and defenders requires us to detect and address suspicious activity as soon as possible for a more secure posture.
#SecurityIndustry #EarlyDetection #CyberSecurity
| View » | Share on Linkedin » | Tweet » | Toot » |
Azure WAF Notebook for Microsoft Sentinel
Azure WAF is able to detect SQLI attacks, but may result in false positives that require investigation. Microsoft has released a Sentinel Notebook to automate the investigation process and implement Azure WAF exclusions.
#AzureWAF #SQLI #SentinelNotebook
| View » | Share on Linkedin » | Tweet » | Toot » |
Outlook Mac for All
Outlook for Mac is now free to use, allowing Mac users everywhere to easily add Outlook.com, Gmail, iCloud, Yahoo! or IMAP accounts and benefit from its enterprise-grade security and optimized user interface.
#OutlookForMac #Gmail #iCloud
| View » | Share on Linkedin » | Tweet » | Toot » |

Open letter demands OWASP overhaul, warns of mass project exodus
OWASP has been providing free and open resources for over twenty years to help with software security, and recently there have been questions raised about their ability to keep up with the modern internet and security industry.
#OWASP #SoftwareSecurity #CyberSecurity





![[Coming soon] Microsoft Sentinel out-of-the-box content centralization!](https://techcommunity.microsoft.com/t5/image/serverpage/image-id/449315iDAD3E67697EF9BA9/image-size/large?v=v2&px=999)