💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Bridging the Security Gap: Mitigating Lateral Movement Risks from On-Premises to Cloud Environments | Wiz Blog
This post from Wiz Blog talks about bridging the security gap in on-premises to cloud environments. It highlights the benefits of Wiz in improving cloud security posture and reducing risks from lateral movement. The post includes testimonials from customers who have used Wiz and experienced significant improvements in their cloud security.
#cloud #security #softcorpremium
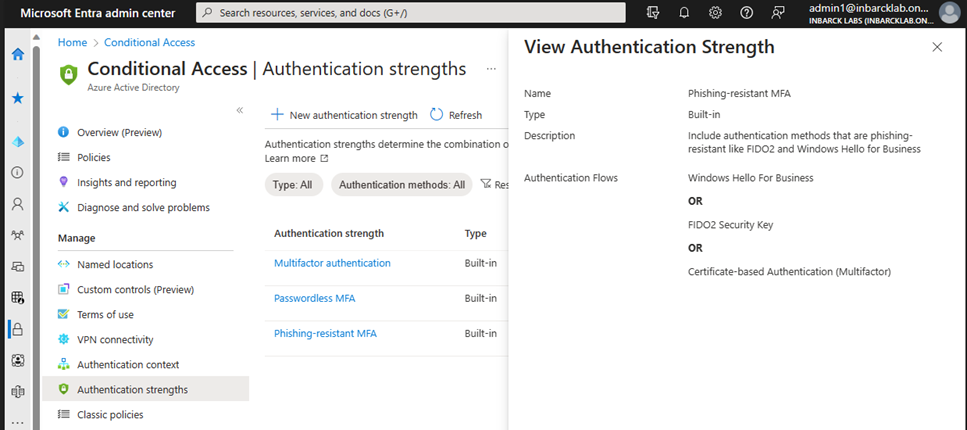
Conditional Access authentication strength is now Generally Available! - Microsoft Community Hub
Microsoft has announced the general availability of the Conditional Access authentication strength feature. This feature will help organizations to tighten their security posture by allowing them to set conditions for accessing sensitive data. By using this feature, organizations can ensure that only authorized users with strong authentication methods can access their data. This feature is now available for all Microsoft 365 and Azure AD customers.
#Microsoft #ConditionalAccess #softcorpremium
Learn to defend against threats with Microsoft Defender and Microsoft Sentinel - Microsoft Community Hub
Learn to defend against threats with Microsoft Defender and Microsoft Sentinel - Microsoft Community Hub
#MicrosoftDefender #MicrosoftSentinel #softcorpremium
What's New at Microsoft Secure - Microsoft Community Hub
Microsoft has made updates to its Secure Community Hub, which provides resources and support for security-related topics. The hub covers a variety of Microsoft products and services, including Windows, Azure, and Microsoft 365, and includes articles, videos, and discussions. Users can browse hubs by product or topic, and can also join the community to ask questions and share best practices with other security professionals.
#MicrosoftSecure #MicrosoftCommunity #softcorpremium
Microsoft Enterprise SSO for Apple Devices Is Now Available for Everyone - Microsoft Community Hub
Microsoft announces the availability of Enterprise SSO for Apple devices to everyone. The new feature allows for secure and seamless sign-on for enterprise applications and services on Apple devices. This integration includes Microsoft Azure AD, Microsoft 365, and other cloud services. With Single Sign-On (SSO), users can sign in once and access multiple applications without the need for additional authentication. This feature provides improved security and enhances the user experience.
#Microsoft #enterprise #SSO #softcorpremium
Exclude cipher suites at the API gateway using a Network Load Balancer security policy | AWS Security Blog
AWS has announced the ability to exclude cipher suites at the API gateway using a Network Load Balancer security policy. This feature allows users to control the cipher suites that are used for SSL/TLS connections between the client and the API Gateway. The cipher suites that are not included in the security policy are excluded from the API Gateway, reducing the attack surface. Users can customize the security policy to include or exclude cipher suites based on their needs.
#APIgateway #cipherSuites #AWS #softcorpremium
GitLab Critical Security Release: 16.0.1 | GitLab
GitLab has released the critical security version 16.0.1 for GitLab Community Edition (CE) and Enterprise Edition (EE), meant only for installations running 16.0.0. This version includes important security fixes, and GitLab recommends that GitLab installations running 16.0.0 be upgraded immediately. GitLab.com is already running the patched version.
#GitLab #security #softcorpremium
How to get rid of AWS access keys- Part 1: The easy wins | Wiz Blog
This post provides a guide on how to get rid of AWS access keys. The post is divided into two parts, with Part 1 focusing on easy wins. The author explains that access keys are a high-value target for attackers and can lead to data breaches. The post suggests using IAM roles, temporary credentials, and AWS Secrets Manager as alternatives to access keys. Additionally, it recommends disabling inactive access keys and rotating access keys regularly to enhance security.
#AWS #accesskeys #softcorpremium
Building a Strong Foundation: Prioritizing Developer Security at Microsoft Build 2023
Microsoft is prioritizing developer security at Microsoft Build 2023, focusing on building a strong foundation for developing secure applications. The company is determined to integrate security at every level of the software development process, from infrastructure to code, to ensure that every app built on their platform is secure. Microsoft aims to provide developers with the necessary tools, resources and training to develop secure software and prevent cyber attacks.
#MicrosoftBuild2023 #DeveloperSecurity #softcorpremium
How we Sped up Acquiring Forensic Data From Managed Kubernetes Services by 97% by Rebuilding the SDK - Cado Security | Cloud Forensics & Incident Response
Cado Security has rebuilt its SDK to speed up acquiring forensic data from managed Kubernetes services by 97%. The non-persistent agent integration eliminates the need for persistent agents to capture forensic details from Kubernetes and Docker containers. The architecture of Cado’s Kubernetes stack allows support for Managed Kubernetes Services to be added quickly, and the new integration reduces the time needed to build a feature from two weeks to just one day.
#Kubernetes #forensics #softcorpremium
OWASP Top 10 for Large Language Model Applications | OWASP Foundation
The OWASP Top 10 for Large Language Model Applications project aims to educate developers, designers, architects, managers, and organizations about the potential security risks when deploying and managing Large Language Models (LLMs). The project provides a list of the top 10 most critical vulnerabilities often seen in LLM applications, highlighting their potential impact, ease of exploitation, and prevalence in real-world applications. The goal is to raise awareness of these vulnerabilities, suggest remediation strategies, and ultimately improve the security posture of LLM applications.
#OWASP #LLM #security #softcorpremium
Red Hat Tackles Software Supply Chain Security
Red Hat is addressing software supply chain security with the release of its latest product, OpenShift GitOps. The platform aims to automate the delivery and operation of Kubernetes-native applications in a way that is secure by default. OpenShift GitOps comes with built-in security features that allow for an auditable, secure pipeline from source code to production, ultimately safeguarding the software supply chain.
#security #supplychain #softcorpremium
130K+ Patients' Social Security Numbers Leaked in UHS of Delaware Data Breach
Over 130,000 patient social security numbers were leaked in a data breach at UHS of Delaware.
#DataBreach #UHSofDelaware #softcorpremium
Tesla Whistleblower Leaks 100GB of Data, Revealing Safety Complaints
A Tesla whistleblower has leaked 100GB of data that reveals safety complaints. The information includes documents related to the company's manufacturing practices and the number of cars rejected for defects at its Fremont factory. The whistleblower also claims that Tesla has installed batteries with punctured holes, which could lead to leakages and fires. Tesla has denied the allegations and has stated that the whistleblower is a former employee who was fired for stealing confidential data.
#Tesla #whistleblower #safety #complaints #softcorpremium
Honeywell Releases Cyber Insights to Better Identify Cybersecurity Threats and Vulnerabilities
Honeywell has released Cyber Insights, a tool that helps organizations identify cybersecurity threats and vulnerabilities. The tool uses advanced analytics and artificial intelligence to analyze data from various sources and provide actionable insights to security teams. With Cyber Insights, organizations can better prioritize their security efforts and minimize the risk of cyber attacks. Honeywell's Cybersecurity Vice President, Jeff Zindel, said the tool enables security teams to move from reactive to proactive security measures.
#cybersecurity #vulnerabilitymanagement #softcorpremium
AI Risk Database
AI Risk Database is a tool for discovering and reporting the risks associated with public machine learning models. The database provides organizations with a comprehensive and up-to-date overview of the risks and vulnerabilities associated with publicly available models. The database is continuously updated with the latest models, file reputation, and model vulnerabilities.
#AI #vulnerability #softcorpremium