💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
General Availability of Structured Logs and Single Click Upgrade/Downgrade in Azure Firewall - Microsoft Community Hub
Azure Firewall offers centralized traffic flow governance and logging using a DevOps approach. It supports application and network-level filtering rules and has built-in auto-scaling and integration with feeds to filter known malicious IP addresses and domains. Recently, the service has announced the general availability of Azure Firewall Structured Logs, which provides an enhanced logging experience for firewall events. It also supports an easy upgrade and downgrade operation, making it suitable for organizations with more complex network architectures, regulatory compliance, and security requirements.
#AzureFirewall #CentralizedTrafficGovernance #EnhancedLoggingExperience #softcorpremium
What’s new in Microsoft Intune: 2306 (June) edition - Microsoft Community Hub
Microsoft Intune is offering significant additions to its security and productivity features in the June 2023 service release. The first addition is Mobile Application Management (MAM) for Microsoft Edge for Business on Windows, which is now available in public preview. The MAM capability provides users with secure access to organizational data on personal Windows devices. The second addition is improved management for Windows drivers and firmware updates in Intune, making it easier to keep drivers and firmware on Windows devices up to date. Microsoft is also hosting a Tech Community Live event focused on Intune, and feedback on the new features is welcome.
#MicrosoftIntune #MAM #WindowsUpdates #softcorpremium
Digital Event: Microsoft Entra Innovations - Microsoft Community Hub
Microsoft Entra's Reimagine secure access event has been rescheduled to July 11, 2023, from June 20, 2023. The event will showcase the next set of innovations from Microsoft Entra, including insights into identity and access management trends, new product features, and a panel discussion with Microsoft Security leaders and experts. Interested participants can register for the digital event on Microsoft Entra's website.
#MicrosoftEntra #SecureAccess #IdentityManagementTrends #softcorpremium
Live series 6/27 & 7/20: Microsoft Entra Tech Accelerator - Microsoft Community Hub
Microsoft's digital event, Reimagine secure access with Microsoft Entra, has been rescheduled for July 11, 2023, with complementary up-close conversations with technical experts split into two sessions on June 27 and July 20, 2023. The sessions will cover the latest solutions and innovations in Microsoft Entra, with opportunities to ask Microsoft anything. The sessions will be streamed live on Microsoft Tech Community, YouTube, and Twitter. Attendees can RSVP and participate in the live Q&A after signing into the Tech Community.
#MicrosoftEntra #SecureAccess #TechCommunity #softcorpremium
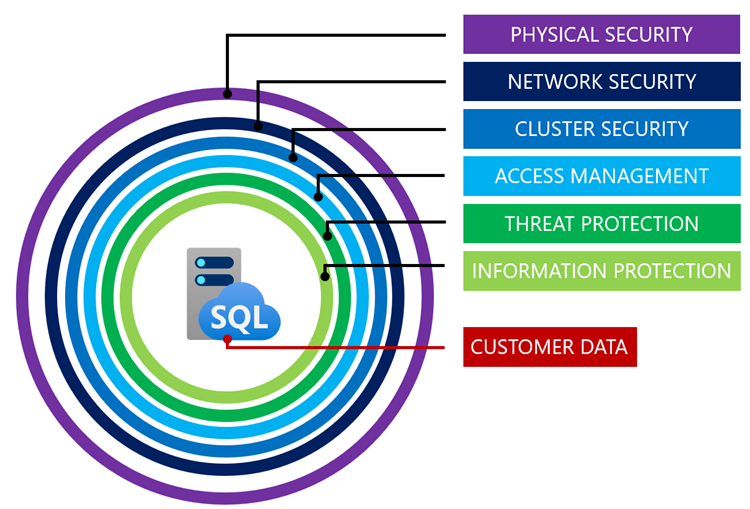
Securing your data ecosystem in Azure SQL Managed Instance
Azure SQL Managed Instance offers multiple layers of security, including physical security measures, network security, access management, and threat protection. Users can benefit from private endpoints, Azure Firewall, and Azure Active Directory authentication for centralized management of user identities and permissions. Microsoft also offers advanced security capabilities such as SQL Vulnerability Assessment and Advanced Threat Protection. Transparent Data Encryption (TDE) encrypts the entire database using Advanced Encryption Standard (AES) algorithm, protecting against theft or unsecured disposal of hardware or media. Additionally, Microsoft Purview offers trustworthy data management with comprehensive security and compliance know-how from over 3,500 dedicated security experts.
#AzureSQL #ManagedInstanceSecurity #DataEncryptionandCompliance #softcorpremium
Lesson Learned #379: ADALNativeWrapper.ADALGetAccessToken error using AAD - Password Authentication - Microsoft Community Hub
The article discusses issues that can arise when using Azure Active Directory for password authentication and provides possible solutions. It also explains the workflow process for receiving a token and how to test for connectivity. The article includes a PowerShell script for obtaining an access token and lists possible problems with the script, such as errors in parameters, network connectivity issues, and permission and role issues. The article suggests verifying parameter values, checking network connectivity, configuring firewall or proxy restrictions properly, ensuring appropriate permissions are in place, considering token lifetimes, and addressing potential DNS or port-related issues to ensure successful authentication.
#AzureActiveDirectory #PasswordAuthentication #PowerShellScript #softcorpremium
Elastio Integrates with AWS Backup for Secure Backups to Enhance Ransomware Defense | AWS Partner Network (APN) Blog
Elastio has integrated with AWS Backup to enhance ransomware defense for AWS customers. Elastio is a platform that scans supported AWS Backup recovery points for threats, continuously recovery tests them, identifies the last clean recovery point, and integrates with existing notification processes when ransomware, corruption, or any other threat is detected. The integration allows customers to ensure that their backups are clean, non-compromised, recoverable, and resilient to ransomware attacks. Elastio's platform is run completely from within the customer’s AWS account, and the company does not have access to view or take custody of customer data.
#AWSBackup #RansomwareDefense #DataSecurity #softcorpremium
US feds stress urgent MOVEit platform patching after attacks hit agencies | CSO Online
The US federal government is urging urgent patching of the MOVEit platform after several agencies were hit by attacks from the Clop ransomware gang. The gang has exploited vulnerabilities in Progress Software’s MOVEit Transfer security file transfer platform to attack dozens of public and private sector organizations worldwide. The US State Department's Rewards for Justice program is offering up to a $10m reward for information conclusively linking the Clop ransomware attacks to a foreign government. The Clop gang has threatened to extort or release data stolen from government agencies.
#cybersecurity #ransomware #datasecurity #softcorpremium
Policy-based access control in application development with Amazon Verified Permissions | AWS DevOps Blog
The AWS DevOps Blog discusses policy-based access control (PBAC) in application development using Amazon Verified Permissions. PBAC is a more flexible access control model that enables fine-grained control over access to resources in an application. Amazon Verified Permissions allows developers to externalize access control rules from the application code and centralize policy management and administration. This simplifies the application development process, reduces the risks of security vulnerabilities, and aligns with industry regulations. PBAC also offers flexibility, scalability, and centralized permissions management across various stages of the DevOps process.
#AWSDevOps #PolicyBasedAccessControl #AmazonVerifiedPermissions #softcorpremium
Support Tip: Retrieving Intune apps reporting data from Microsoft Graph Beta API - Microsoft Community Hub
Starting in mid-May 2023, to retrieve Intune app reporting data through the Microsoft Graph Beta API, admins should follow the documented instructions to ensure reporting automation and scripts continue to work as expected. The documentation explains how to export reports that have export functionality, and for reports that do not have this functionality, the report can be called directly through the Graph API. No action is required if documentation and reporting automation are up to date, but awareness is necessary.
#IntuneReportingAutomation #MicrosoftGraphBetaAPI #ReportExportFunctionality #softcorpremium
The False Identifier Anti-pattern
The \"false identifier anti-pattern\" is a dangerous practice where an application assumes an attribute other than the subject of an assertion from a federated identity provider is a unique and trustworthy account identifier. This can lead to ineffective and counter-productive results, as personal user data like phone numbers and email addresses can be used as identifiers in some contexts, but there is a critical difference in using them as login identifiers. The OpenID Connect spec requires unique local identifiers to prevent duplication and ensure SSO remains unaffected. The article discusses the risk of local conflation within a single tenant, where an identity provider sends tokens for two different accounts with the same email address to an application. The use of Bring Your Own Identity (BYOI) and B2B federated use cases is breaking down the captive paradigm, posing a growing risk for identity providers. It is important to use the token subject and issuer together to form the primary key when identifying a federated account, and to ensure every token subject generated for SSO is locally unique, never reassigned, and stable over time. Microsoft Entra offers solutions and resources for securely mapping user identities.
#identitysecurity #federatedidentity #BYOI #softcorpremium
Updated Requirements for SMTP Relay through Exchange Online - Microsoft Community Hub
Microsoft is updating its requirements for SMTP relay through Exchange Online. After November 1, 2023, relaying email through Exchange Online will require a certificate domain and an accepted domain of the organization. This may affect email routing or delivery for organizations that relay non-delivery reports generated by their on-premises system through Exchange Online or use a third-party cloud service to relay messages. To minimize the effects of this change, organizations must update their Inbound Connector of OnPremises type to use a certificate domain and add it as an accepted domain of the organization. Third-party add-on services must also support a unique certificate for the organization, and the certificate domain must be an accepted domain of the organization.
#ExchangeOnline #SMTPRelay #EmailRouting #softcorpremium
Trend Micro adds generative AI to Vision One for enhanced XDR | CSO Online
Trend Micro has integrated generative AI into its Vision One platform to enhance its extended detection and response (XDR) capabilities. The new tool, Companion, uses advanced AI and machine learning analytics to amplify security operations and improve threat hunting speeds for analysts of varying skill levels. Companion works with the broader Vision One platform to enhance XDR alerts, facilitate quicker understanding, and provide contextualized AI-driven recommendations for security events. Additionally, Companion can provide plain-language summaries of complex multi-step, multi-layer attacks and automate incident reporting to streamline incident response workflows. Trend Micro's generative AI and large language model (LLM) capabilities are built to prioritize security and compliance, including measures to prevent the mixing of LLM instances and training data from other vendors. However, there is a potential pitfall where analysts may become too reliant upon generative AI to provide answers.
#AIsecurity #XDR #incidentresponse #softcorpremium
Mitigate risks using in-place eDiscovery | Uncovering Hidden Risks
Microsoft's Director of Discovery Programs discusses strategies to mitigate security and compliance risks by using in-place eDiscovery to support investigations and litigation. The discussion covers trends affecting the eDiscovery space, advice for handling large amounts of data, Microsoft's approach to new technology innovations, implementing an effective eDiscovery strategy, and the benefits of using Purview eDiscovery Premium internally. The episode is available on various podcast platforms.
#eDiscoveryStrategy #MicrosoftPurview #DataComplianceSolutions #softcorpremium
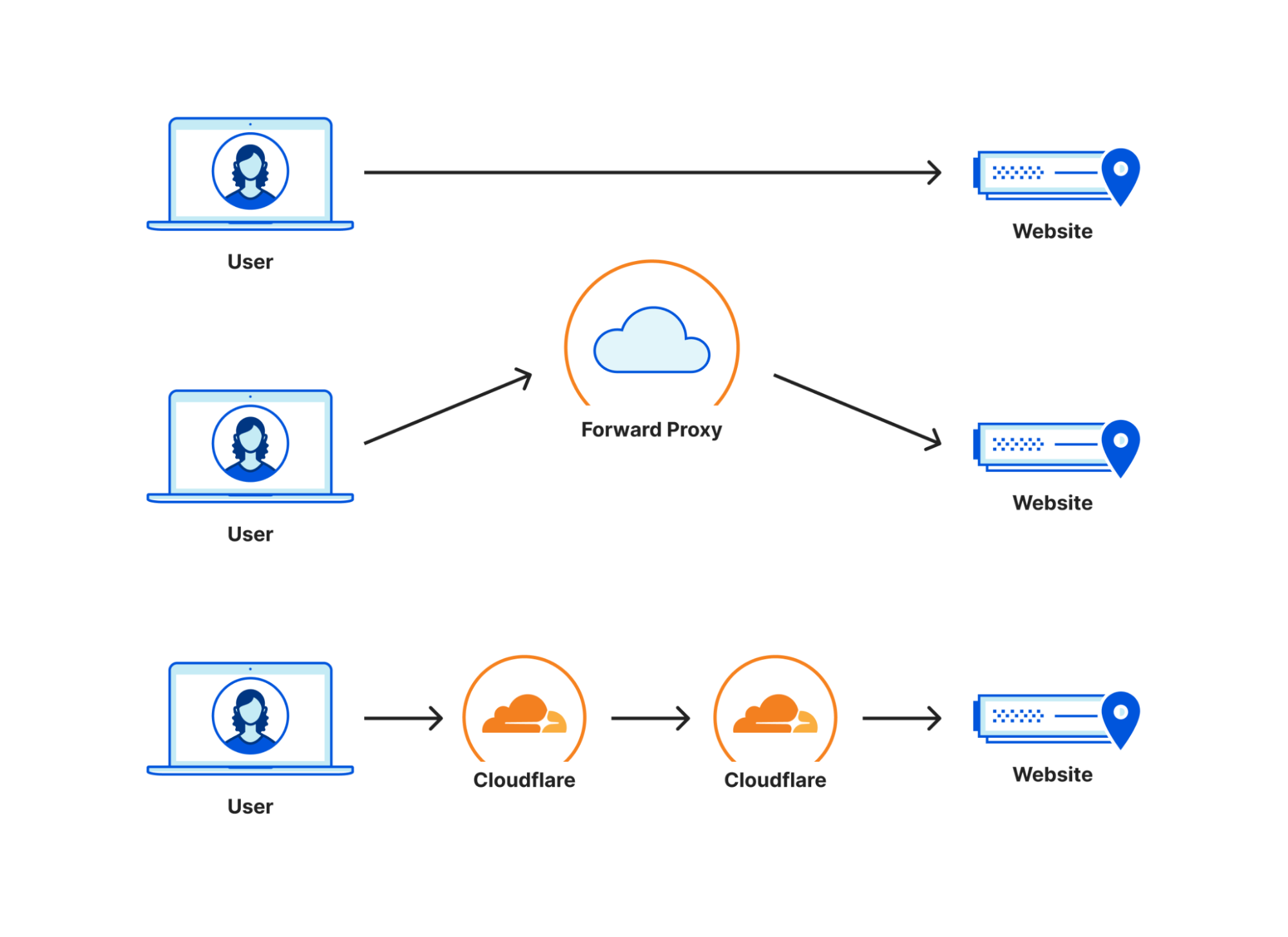
How we think about Zero Trust Performance
Cloudflare is conducting tests to improve the performance of their Zero Trust services in order to enhance user security and productivity. They measure Zero Trust performance using end-to-end HTTP response measurements, which they believe is the best method. Improving Zero Trust performance requires good processing times, well-peered last mile connections, well-peered networks hosting important applications, and diverse paths on the internet. Cloudflare emphasizes the importance of proximity to users in achieving a small path in Zero Trust networks. They offer tools to monitor performance and track Zero Trust performance on their platform, DEX, and offer a free app to make internet browsing faster and safer while also protecting against DDoS attacks.
#CloudflareZeroTrust #improvingsecurity #DDoSprotection #softcorpremium
How do we best govern AI? - Microsoft On the Issues
Microsoft has released a report titled \"Governing AI: A Blueprint for the Future,\" which outlines five ways governments should consider policies, laws, and regulations around AI. The company emphasizes its commitment to ethical AI and building a culture of responsible AI. The report proposes a KY3C approach for AI models, and the implementation of effective safety brakes for AI systems that control critical infrastructure. Microsoft also suggests that legal protections for AI at the applications layer are necessary to ensure the safety and rights of people. The company is committed to advancing responsible AI through a multi-disciplinary approach, and offers the paper as a collective journey towards a responsible future for AI.
#ResponsibleAI #AIethics #AIfuture #softcorpremium
CloudTweaks | SIS LMS Integration
This collection of articles covers various topics related to education technology and cybersecurity. It explores the benefits of integrating Student Information Systems (SIS) and Learning Management Systems (LMS) for teachers, students, and administrators, as well as the challenges and best practices for successful integration. It also discusses the importance of ongoing education and the need for effective cybersecurity measures, including multicloud security and improved data culture. The rise of data clean rooms for customer insights is highlighted, along with the hidden costs of free cloud migration tools.
#edtech #cybersecurity #dataprivacy #softcorpremium
AWS IAM now supports FIDO2 for multi-factor authentication in AWS GovCloud (US) Regions
AWS IAM now supports FIDO2 security keys for multi-factor authentication in the AWS GovCloud (US-East and US-West) Regions. This provides cryptographically secure and phishing-resistant MFA authentication and expands existing MFA functionality with additional options such as FIPS-validated security keys. Customers can specify the registration of specific authenticators in their IAM policies, based on their preferred certification type and level, to meet specific security or compliance requirements. This update strengthens the security of AWS accounts while ensuring usability, security, and compliance goals are met.
#AWSIAM #FIDO2 #MFAauthentication #softcorpremium
Partner Center Technical Corner: June 2023 edition - Microsoft Community Hub
The Technical Corner blog highlights new security alerts launched to help prevent Azure fraud and the Action Center to stay updated on Partner Center communications. Recent updates and enhancements are also discussed, along with access to the technical roadmap and resources. Starting June 1, 2023, all Cloud Solution Provider partners will have visibility into new security alerts. Feedback is encouraged through a short survey.
#AzureSecurityAlerts #PartnerCenterUpdates #CSPFeedbackSurvey #softcorpremium
Amazon MemoryDB for Redis achieves FedRAMP Moderate compliance
Amazon MemoryDB for Redis has achieved FedRAMP Moderate compliance, making it suitable for building applications for workloads that require this level of security. MemoryDB is an in-memory database that offers microsecond reads, millisecond writes, scalability, and enterprise security. It is also HIPAA eligible, HITRUST, ISO certified, SOC, and PCI DSS compliant. Customers can learn more about MemoryDB by visiting the AWS services compliance page and MemoryDB page, or by contacting the MemoryDB team via email.
#AmazonMemoryDB #FedRAMPCompliance #EnterpriseSecurity #softcorpremium
Amazon Redshift improves the experience for encrypting the data warehouse
Amazon Redshift has improved its encryption capabilities for data warehouses with RA3 node types by reducing encryption time and improving warehouse availability during the process. This enhancement makes the encryption process 5x faster, reducing encryption time from weeks to just a few days. The improved availability of the data warehouse during encryption allows businesses to continue operating without interruption. These encryption enhancements are available in all commercial and AWS GovCloud (US) Regions.
#AmazonRedshift #DataWarehouseEncryption #RA3NodeTypes #softcorpremium
Terraform on Google Cloud V1.3 — Secret manager and its what, why and how. | by Akhilesh Mishra | Google Cloud - Community | Jun, 2023 | Medium
The blog post discusses the use of Google Cloud Secret Manager with Terraform to store service account keys securely. The author suggests using Secret Manager to avoid security concerns with storing keys in GitHub secrets, and provides steps for deploying Secret Manager with Terraform. The post also covers the benefits of using Secret Manager and the importance of state locking in Terraform. The author plans to follow up with a post on deploying a Cloud Function to rotate service account keys stored in Secret Manager.
#GoogleCloudSecretManager #TerraformDeployment #CloudSecurityTips #softcorpremium
Hackers Will Be Quick to Bypass Gmail's Blue Check Verification System
Google has introduced a blue verified check mark for Gmail addresses to protect against malicious and unwanted emails, but experts warn that hackers will quickly find ways to bypass this new security measure. The article covers various topics related to cybersecurity, including database security risks, advanced threats, and insider threats. It also highlights upcoming security events and webinars, with resources available including reports, white papers, and partner perspectives. The article emphasizes the importance of investing in security solutions such as SPF, DKIM, and DMARC, as well as using multifactor authentication and leveraging threat intelligence. The website uses cookies to tailor content and ads to users' interests, but blocking certain types of cookies may impact user experience on the website and services offered.
#cybersecurity #emailsecurity #multifactorauthentication #softcorpremium
Western Digital blocks unpatched My Cloud devices | CSO Online
Western Digital has blocked devices running vulnerable firmware versions from accessing its cloud services, following the release of firmware updates for its My Cloud product line to address a critical path traversal bug that leads to remote code execution (RCE). Devices running unpatched firmware versions will not be able to connect to Western Digital cloud services starting June 15, 2023, and users will not be able to access their data until the device updates to the latest firmware. However, users can continue to access their data via Local Access, the procedure that enables access through network-mapped drives on a local network. Last month, ransomware group BlackCat released screenshots of videoconferences and internal emails from data stolen from the Western Digital breach.
#WesternDigitalCloud #FirmwareUpdates #Cybersecurity #softcorpremium
Keeper Security: Poor password practices increase risks of hacking - Back End News
A study by Keeper Security, a provider of zero-knowledge security and encryption software, has found that poor password management increases the vulnerability of users to hacking. The company assessed the password habits of over 8,000 individuals and found that three in four people globally don’t adhere to widely accepted password best practices, with a majority either using weak passwords or repeating variations of passwords to protect their online accounts. The report noted that emotion might be playing a role in putting digital users at greater risk of being hacked.
#passwordmanagement #cybersecurityawareness #digitalvulnerability #softcorpremium