💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
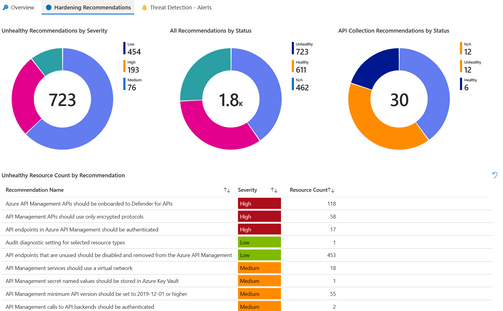
Microsoft Defender for API Security Dashboard - Microsoft Community Hub
Microsoft Defender for APIs is a plan that offers full lifecycle protection, detection, and response coverage for APIs published in Azure API Management. It provides security admins with visibility to their business-critical managed APIs, security findings to investigate and improve API security posture, and real-time threat detection that generates alerts for suspicious activities. The Microsoft Defender for API Security Dashboard provides a unified view and deep visibility into API security issues, allowing users to visualize the state of their API posture, investigate detected threats, and prioritize security recommendations. The dashboard is built into the Microsoft Defender for Cloud portal and requires users to enable Defender for APIs and onboard API endpoints.
#MicrosoftDefenderforAPIs #APIsecurity #AzureAPIManagement #softcorpremium
Share your feedback on Microsoft 365 Defender via the new feedback portal
Microsoft has launched a new community feedback experience for its Microsoft 365 Defender customers. The feedback portal allows customers to submit suggestions and feature requests for security products. The portal also offers features for customers to search and vote on the most important features, leave comments, and monitor the progression of their suggestions. However, due to the volume of feedback received, Microsoft cannot guarantee an individual reply to all suggestions.
#Microsoft365DefenderFeedback #CustomerFeedbackPortal #SecurityProductSuggestions #softcorpremium
Action required: Last chance to migrate ADAL apps! - Microsoft Community Hub
Microsoft has announced a recommendation for customers to migrate from the legacy Azure AD Authentication Library (ADAL) to the Microsoft Authentication Library (MSAL) in its ongoing effort to improve developer experience, service reliability, and security. The deadline for migration has been extended to June 30, 2023, and the use of MSAL is designed to simplify and manage acquiring, caching, and refreshing tokens, as well as follow best practices for resilience. Azure AD recommendations can be found for customers to easily migrate their apps using ADAL to MSAL.
#AzureADmigration #MSALmigration #developerexperience #softcorpremium
Frontend mTLS support for External HTTPS Load Balancing | Google Cloud Blog
Google Cloud has announced mutual Transport Layer Security (mTLS) support for external HTTPS load balancing, enabling clients to be authenticated using certificates. With mTLS, customers can build value-added security services for IoT and industrial use cases, and meet regulatory standards such as OpenBanking. To set up mTLS, customers configure how the load balancer should authenticate incoming requests and handle failed certificate validations. Google Cloud plans to extend mTLS support to regional internal and external load balancers and offer additional features.
#GoogleCloudSecurity #mTLS #LoadBalancing #softcorpremium
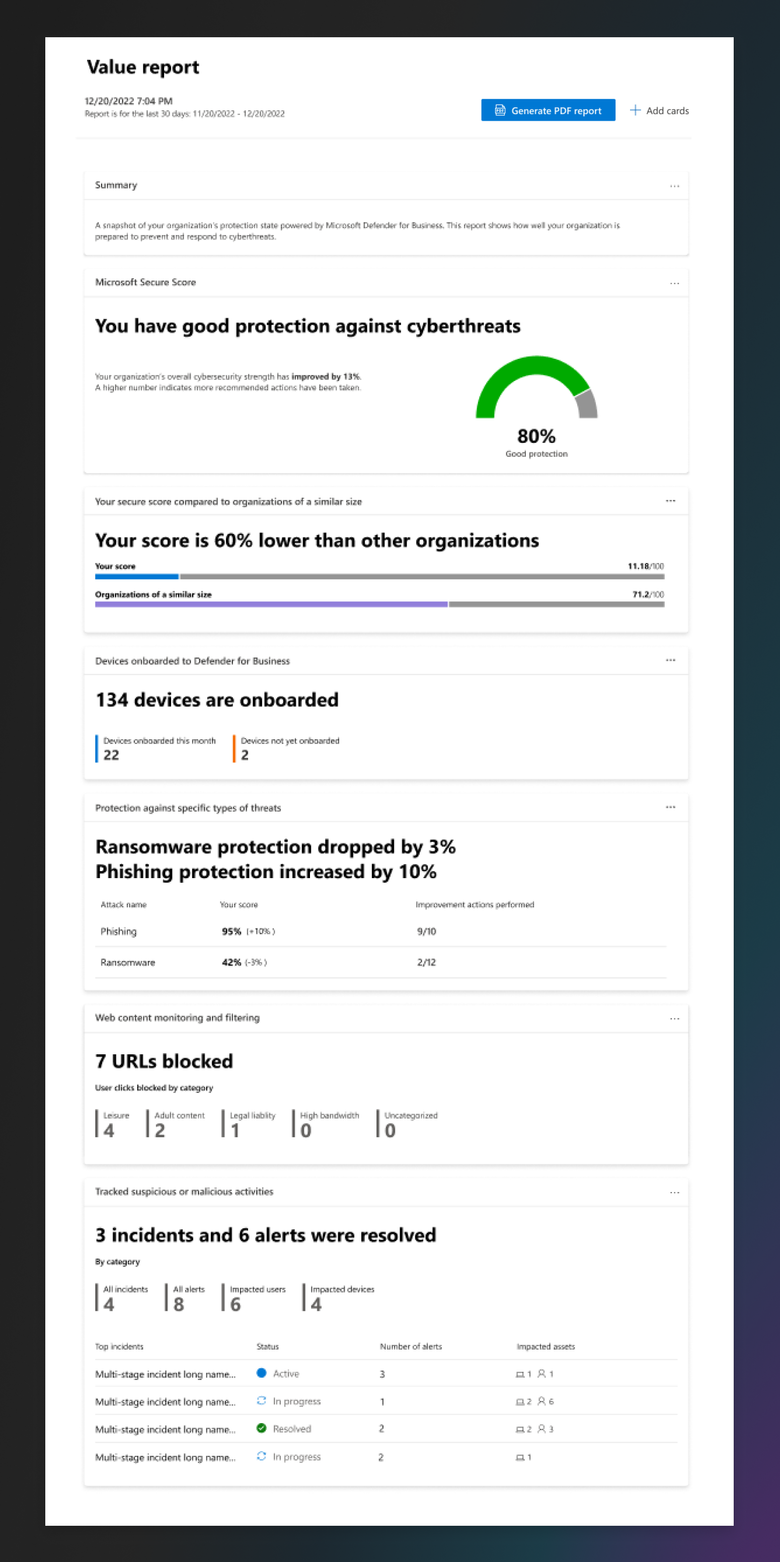
Defender for Endpoint - Monthly security summary report
Microsoft Defender for Endpoint has launched a public preview of its monthly security summary report, which streamlines security progress reporting for service providers and SOC teams. The report enables stakeholders to gain insights into an organisation's security performance and gives security teams an easily consumable PDF report to look back on their actions and accomplishments managing the environment. The report contains six sections that highlight key aspects of an organisation's security performance, including Microsoft Secure Score, Secure score compared to other organisations, devices onboarded, protection against threats, web content monitoring and filtering, and suspicious or malicious activities. The monthly security summary report is available for Microsoft 365 Defender, Microsoft Defender for Endpoint P1/P2, and Microsoft Defender for Business customers.
#MicrosoftDefender #SecurityPerformance #MonthlyReport #softcorpremium
Announcing Azure Firewall Structured Logs General Availability - Microsoft Community Hub
Azure Firewall has announced the general availability of its Structured Logs capability, which provides an enhanced logging experience for firewall events. Structured logs use a predefined schema to structure log data, making it easy to search, filter, and analyze. The feature can be easily integrated with other security tools and can help in troubleshooting network performance issues. Customers can choose to use resource-specific tables instead of AzureDiagnostics, and the logs can be exported to various destinations for further analysis. The new capability offers a more detailed view of network traffic and enhances security monitoring capabilities.
#AzureFirewall #StructuredLogs #NetworkSecurity #softcorpremium
Simplify fine-grained authorization with Amazon Verified Permissions and Amazon Cognito | AWS Security Blog
Amazon Web Services has launched Amazon Verified Permissions and Amazon Cognito to provide fast authentication and authorization for applications. The Verified Permissions feature allows users to write policies using the XACML language to dictate who can take certain actions on specific resources. By integrating with Amazon Cognito, AWS removes the need to create context around the requestor's identity. The article explains how to write policies, use API operations to make authorization decisions, and modify policies to accommodate Amazon Cognito attribute namespace. The integration between Amazon Cognito and Verified Permissions can help with creating meaningful authorization requests by relieving the work needed to build entity information about principals.
#AWSVerifiedPermissions #AmazonCognitoIntegration #AuthorizationPolicies #softcorpremium
Controlling Access to Amazon API Gateway with CyberArk Identity and Amazon Verified Permissions | AWS Partner Network (APN) Blog
The AWS Partner Network Blog describes how CyberArk Identity and Amazon Verified Permissions can be used to control access to resources, reducing maintenance overhead and increasing security visibility. A policy-based access control model is used to manage access control logic in a central location with a single policy language, reducing total cost of ownership. The article provides setup instructions and code examples for using Amazon API Gateway and AWS Lambda authorizer for controlling resource access. The integration can be modified to support different enforcement points technologies and Cedar offers flexibility in constructing policies. CyberArk is a global leader in identity security and offers subscription-based SaaS products for AWS customers.
#AWSpartners #Identitysecurity #Accesscontrol #softcorpremium
Protecting Sensitive Data with Collibra Protect and AWS Lake Formation | AWS Partner Network (APN) Blog
Collibra Protect and AWS Lake Formation offer a comprehensive solution for enterprise data access governance. Collibra Protect provides intelligent controls for better results with less risk, while AWS Lake Formation is a fully managed serverless service for building clean and secure data lakes. The combination of both products allows organizations to simplify access governance, promote ethical data access and privacy management, and scale data governance across data sources and services. The solution strikes a balance between data openness and security, and facilitates a secure data sharing environment that can drive business growth.
#CollibraProtect #AWSLakeFormation #DataAccessGovernance #softcorpremium
Google Cloud Blog
Snap Inc, the creators of Snapchat, has chosen Google Cloud's BeyondCorp Enterprise (BCE) to build a durable Zero Trust framework for its security program. BCE allows secure access to applications and resources anywhere in the world through its device-attestation framework and context-aware access policy definitions. Snap's in-house HTTP reverse proxy was integrated with BCE's Identity-Aware Proxy (IAP) to provide a context-rich system for Zero Trust. Snap plans to expand the use of BCE functionalities such as Data Loss Prevention (DLP), malware, and phishing prevention.
#SnapIncOnGoogleCloud #ZeroTrustSecurity #BeyondCorpEnterprise #softcorpremium
New – Move Payment Processing to the Cloud with AWS Payment Cryptography | AWS News Blog
AWS has introduced a new service called AWS Payment Cryptography, which provides secure payment processing in the cloud. The service uses encryption to protect communications and offers multiple tools such as AWS Key Management Service and AWS CloudHSM to manage keys and encryption. The service simplifies the implementation of cryptographic functions and key management for secure payment processing, eliminates the need for on-premises payment HSMs, and offers tools to avoid error-prone key exchange processes. AWS Payment Cryptography offers pay-as-you-go pricing for active keys and API calls and encourages users to move their payment processing applications to the cloud with this service.
#AWSPaymentCryptography #SecurePaymentProcessing #CloudEncryption #softcorpremium
Cyber liability insurance vs. data breach insurance: What's the difference? | CSO Online
The article discusses the importance of understanding the difference between cyber liability insurance and data breach insurance, as companies seek protection against increasing cyber threats. The global cyber insurance market is expected to grow, with North America projected to dominate. Cyber liability insurance covers third-party claims while data breach insurance covers first-party losses. Companies should ensure they have the right coverage and read the fine print to determine limitations. Cyber insurance is complementary, not a substitute, for a robust cybersecurity policy. The article also highlights hot cybersecurity trends and emphasizes the importance of data and information security.
#cyberinsurance #dataliability #cybersecuritytrends #softcorpremium
Business email compromise scams take new dimension with multi-stage attacks | CSO Online
Business email compromise (BEC) scams have taken a new dimension with multi-stage attacks that exploit the relationships between different organizations, according to Microsoft researchers. Attackers managed to chain BEC against four or more organizations by leveraging the relationships between them. The campaign, which Microsoft researchers call multi-stage adversary-in-the-middle (AiTM) phishing, started with a compromise at a trusted vendor and targeted organizations from the banking and financial services sectors. The attack shows the complexity of AiTM and BEC threats, which abuse trusted relationships between vendors, suppliers, and other partner organisations with the intent of financial fraud.
#BECScams #AiTMPhishing #FinancialFraud #softcorpremium
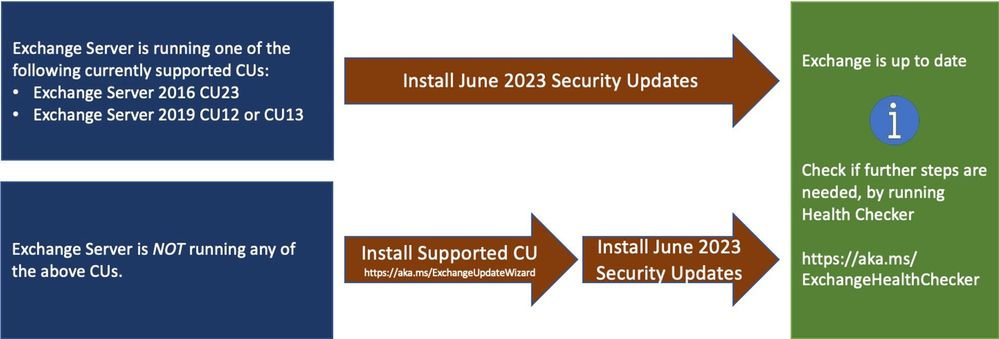
Released: June 2023 Exchange Server Security Updates - Microsoft Community Hub
Microsoft has released Security Updates for vulnerabilities found in Exchange Server 2016 and 2019. The updates are available for specific versions of Exchange Server and can be downloaded from the Microsoft Update Catalog. Exchange Online customers are already protected and do not need to take any action. There are no known issues with this release, and the updates are cumulative. Exchange Server 2013 is no longer supported, and Exchange Server 2019 CU11 is not a supported CU anymore. The Exchange Server Team recommends installing Security Updates on Exchange Servers and all servers and workstations running the Exchange Management Tools to ensure compatibility.
#MicrosoftSecurityUpdates #ExchangeServerUpdates #CybersecurityUpdates #softcorpremium
Rezilion releases agentless runtime software vulnerability management solution | CSO Online
Rezilion has launched an agentless runtime software vulnerability management solution that enables security teams to monitor exploitable software attack surfaces in runtime without using an agent, reducing the time and overhead required for traditional runtime-based software vulnerability analysis. The solution covers all versions of Windows and Linux across 12 code languages. Organizations are losing thousands of hours in time and productivity dealing with backlogs of vulnerabilities that they have neither the time or resources to tackle effectively. Rezilion's new solution facilitates vulnerability prioritization using runtime data to reduce vulnerability management \"noise\" by detecting which specific components need patching, and which don't.
#runtimevulnerabilitymanagement #agentlesssecurity #vulnerabilityprioritization #softcorpremium
Prevent account creation fraud with AWS WAF Fraud Control – Account Creation Fraud Prevention | AWS Security Blog
AWS has introduced AWS WAF Fraud Control - Account Creation Fraud Prevention to protect applications' sign-up pages against fake account creation requests. This feature detects and blocks fraudulent account creation attempts, including those used for taking advantage of promotional bonuses, publishing fake reviews, and spreading malware. AWS WAF Fraud Control - Account Creation Fraud Prevention can be combined with Account Takeover Prevention for comprehensive account fraud prevention. The article provides instructions on how to configure ACFP rules and add them to web ACLs and how to add the AWS WAF JavaScript SDK to application pages. The article also discusses the importance of using .immunity timeout integration fetch wrapper getToken operationfetch and enabling the ATP rule group in the same web ACL as ACFP to prevent account fraud.
#AWSSecurity #FraudPrevention #AccountProtection #softcorpremium
AWS Security Hub launches a new capability for automating actions to update findings | AWS Security Blog
AWS Security Hub has introduced automation rules that allow users to automate actions to update findings and create automation rules, providing a comprehensive view of security posture across AWS accounts. The rules can be used to simplify work for cloud security and DevOps engineers and reduce the mean time to response. Users can specify criteria and actions to update severity levels and add notes to indicate urgency for certain security findings. Users can also prioritize findings based on contextual fields such as severity and account ID. Templates are available for creating new rules based on applicable use cases.
#AWSSecurityHub #cloudsecurity #DevOpsengineering #softcorpremium
Simplify How You Manage Authorization in Your Applications with Amazon Verified Permissions – Now Generally Available | AWS News Blog
Amazon has launched Amazon Verified Permissions, a fine-grained permissions management and authorization service that simplifies authorization management in a consistent and scalable way. It allows for fine-grained permissions using a schema for principal types, resource types, and valid actions, and simplifies policy creation with templates. Users can create a policy store to store policies and schema, and authorization decisions are made based on all the policies present. The feature is now generally available and comes with new capabilities and a simplified user experience in the AWS Management Console.
#AmazonVerifiedPermissions #FineGrainedPermissions #AWSManagementConsole #softcorpremium
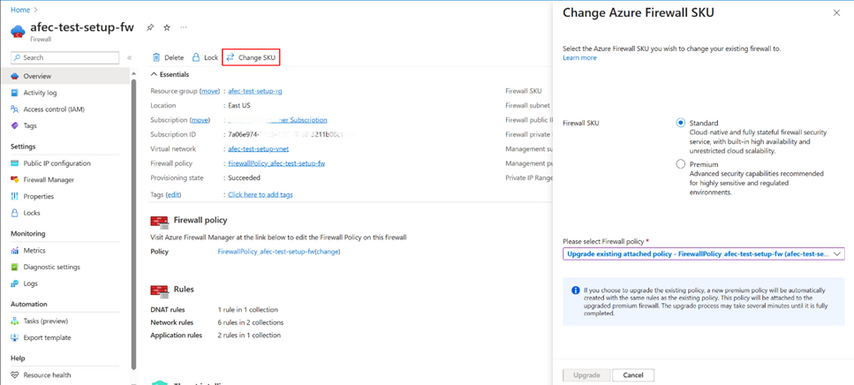
Announcing Azure Firewall Upgrade/Downgrade General Availability - Microsoft Community Hub
Microsoft's Azure Firewall Standard and Premium now support an easy upgrade and downgrade operation, simplifying the process and reducing the effort and time required to upgrade the firewall. The upgrade/downgrade feature automates the entire process, ensuring that the firewall is always up and running and service downtime is not expected. Upgrading to the Premium SKU ensures improved security with more features such as URL filtering, intrusion detection and prevention, TLS inspection, and more comprehensive threat intelligence capabilities, making it more suitable for organizations with complex network architectures, regulatory compliance, and security requirements.
#MicrosoftAzureFirewall #FirewallUpgrade #PremiumSecurityFeatures #softcorpremium
Vault Agent with GKE. Vault Agent behaves as a client-side… | by Jasbir Singh | Google Cloud - Community | Jun, 2023 | Medium
The article discusses using Vault Agent for automatic authentication and secrets management in Kubernetes environments. It provides instructions on configuring Vault Agent Auto-Auth with Kubernetes, creating a Pod with Vault Agent and Nginx containers, and verifying the successful creation of a Pod. The article also includes information on other Kubernetes-related topics such as Kubeshark, K8s 1.27 release, and using AI for infrastructure as code. Additionally, it recommends resources for productivity, DevSecOps, system design, and Google Cloud.
#VaultAgent #KubernetesSecrets #DevSecOps #softcorpremium
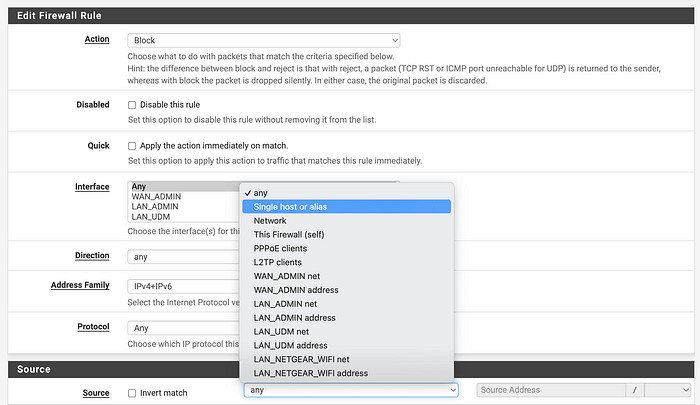
Blocking Networks You Don’t Need. And being able to easily see what you… | by Teri Radichel | Cloud Security | Jun, 2023 | Medium
The article discusses how to block unnecessary network connections by blocking large swaths of IP addresses that are not needed, particularly those from countries with which a company does not do business. The author suggests creating an Alias in PFSense and creating a Float rule to block all inbound traffic from unwanted CIDR blocks without logging it, while creating a separate Float rule to block outbound traffic from the same CIDR blocks and logging it. The article also suggests creating an exception alias to allow traffic from specific IP ranges that are inadvertently blocked by the rules.
#networksecurity #PFsense #IPblocking #softcorpremium
Introducing Secure Web Proxy for egress traffic protection | Google Cloud Blog
Google Cloud has announced the general availability of Secure Web Proxy (Cloud SWP), a cloud-first network security offering that provides web egress traffic inspection, protection, and control. The new offering enables organisations to enforce granular access policies, limit egress web traffic based on sources, identities, destination, or request types, and intercept TLS traffic to inspect encrypted requests and enforce policies. Cloud SWP integrates with Cloud Logging to record metrics and transaction logs for requests handled by the proxy. Additionally, Cloud SWP offers operational efficiencies for customers as it is easy to deploy and manage since it is a managed service that automatically handles security patching and growing of proxy infrastructure.
#CloudSWP #SecureWebProxy #CloudNetworkSecurity #softcorpremium
Microsoft Purview- Paint By Numbers Series (Part 10)- Defender for Cloud Apps & DLP - Overview - Microsoft Community Hub
The article discusses Microsoft Defender for Cloud Apps (MDCA) and its use for Data Loss Prevention (DLP) in cloud-based applications. It provides definitions, use cases, and a list of MDCA's security features, including thread detection, information protection, and conditional access. The article focuses on session policies for DLP and their related control types and activities. It also includes links to additional resources and a disclaimer about official documentation and testing with test data.
#cloudsecurity #datalossprevention #MicrosoftDefender #softcorpremium
Fixes & Reporting | Multicloud Vulnerability Detection with Microsoft Purview
Microsoft Purview's Compliance Manager automates regulatory assessments for multicloud data estates, providing a single view of compliance status and links to required settings for fixing issues. It includes a Data Protection Baseline that assesses compliance controls for common regulations and highlights incomplete controls. The tool enables users to maintain compliance across various cloud services and SaaS platforms, with automated scanning and alerts for changes or required controls. The article also provides step-by-step instructions for setting up and connecting cloud services with Compliance Manager.
#MicrosoftPurview #ComplianceManager #MulticloudCompliance #softcorpremium
Attackers set up rogue GitHub repos with malware posing as zero-day exploits | CSO Online
Attackers have created fake GitHub repositories that claim to host zero-day exploits for popular applications but instead deliver malware. The attacker also created fake GitHub and Twitter accounts posing as security researchers using real photos of researchers from well-known cybersecurity firms. Researchers from security firm VulnCheck found the rogue repositories and reported them to GitHub, which promptly took them down. The attacker set up new accounts and repositories with fake exploits for Microsoft Exchange, Google Chrome, Discord, and Chromium. Experienced security researchers generally take precautions when working with potentially malicious code.
#GitHubFakeRepositories #ZeroDayExploitScams #CybersecurityThreats #softcorpremium