💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
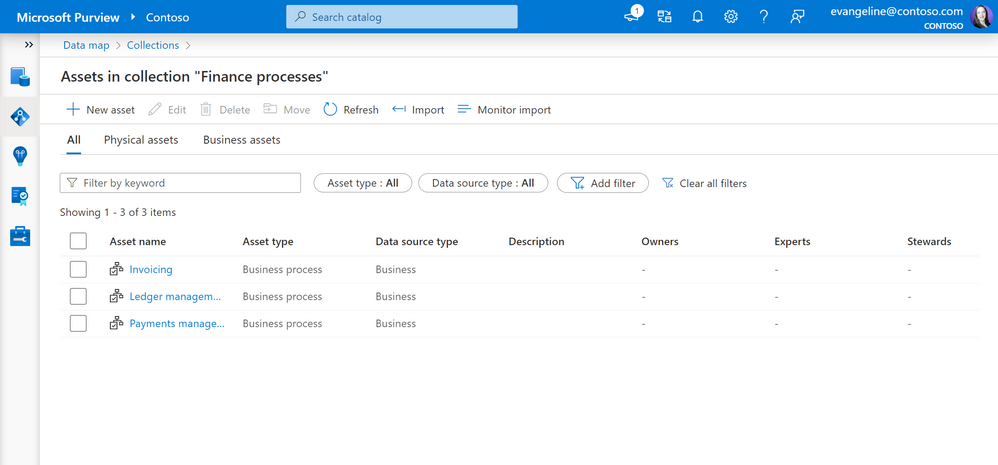
Manage access to business assets using collections in Microsoft Purview - Microsoft Community Hub
Purview will soon allow users to manage access to business assets using collections, which can be curated by experts and assigned to physical data. The update will be available on June 8 and will include a redesigned collection interface with more space for working with assets and filters for asset and source types. Best practices for working with business assets can be found in the provided link.
#Purview #data #management #softcorpremium
Announcing first Google Cloud OSCAL package submission for DoD Impact Level 5 | Google Cloud Blog
Google Cloud has announced the successful submission of its Open Security Control Assessment Language (OSCAL) package for Department of Defense Impact Level 5 (IL5) to eMASS. This represents a significant milestone for the company, as it enables the automation of security assessments and helps protect data and reduce risks. Google Cloud's adoption of OSCAL is seen as a significant step forward in achieving and supporting compliance, providing a single source of truth for security documentation, standardizing compliance artifacts, and automating security assessments and remediation. The company is committed to enhancing, scaling, and supporting compliance to help customers.
#GoogleCloudCompliance #OSCALforSecurityAssessments #AutomatingSecurityRemediation #softcorpremium
Crypto Security Firm Unciphered Claims Ability to Physically Hack Trezor T Wallet
Crypto security firm Unciphered claims the ability to physically hack Trezor T wallet.
#CryptoSecurity #TrezorT #softcorpremium
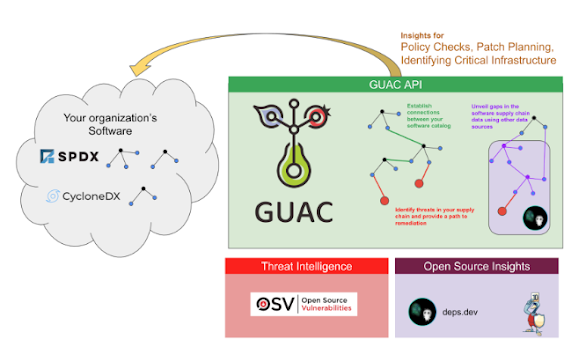
Google Online Security Blog: Announcing the launch of GUAC v0.1
Google has announced the release of Graph for Understanding Artifact Composition (GUAC) v0.1. GUAC helps to understand the software supply chain and to link information from different supply chain ecosystems to keep up with attackers and prevent exposure. GUAC aggregates software security metadata and maps it to a standard vocabulary of concepts relevant to the software supply chain. GUAC is now available as an API for security professionals to start developing on top of, and integrating into, their systems.
#GUAC #softwaresecurity #API #softcorpremium
NCS Case Study - End-to-End Integration of Custom BYOML model with Sentinel - Microsoft Community Hub
The post describes a case study on the end-to-end integration of a custom Bring Your Own Machine Learning (BYOML) model with Sentinel, a security information and event management (SIEM) solution, on the Microsoft Community Hub. The NCS team successfully integrated the BYOML model with Sentinel, which allowed them to detect security threats in real-time and reduce the number of false positives. The post provides technical details on how the integration was achieved and the benefits it provided to the NCS team.
#BYOML #MicrosoftCommunity #NCS #softcorpremium
Microsoft Defender for Cloud - Automate Notifications when new Attack Paths are created - Microsoft Community Hub
Microsoft Defender for Cloud has introduced a new feature that enables users to automate notifications whenever new attack paths are created. This feature will help security teams to stay informed and alert regarding any potential threats to their cloud security. Microsoft Defender for Cloud is a cloud-native security solution that offers unified security management and advanced threat protection for cloud workloads and services across multi-cloud environments.
#MicrosoftDefender #cloudsecurity #attackpaths #softcorpremium
Threat Explorer: UX enhancements, URL clicks tab and customizable export - Microsoft Community Hub
Microsoft has announced enhancements to its Threat Explorer tool, which helps security teams investigate and respond to threats in Microsoft 365 Defender. Updates include UX improvements, a new URL clicks tab, and customizable export options. Threat Explorer allows security analysts to quickly access and analyze potential threats across various Microsoft 365 services. These latest enhancements aim to make the tool more user-friendly and efficient for security teams.
#Microsoft #ThreatExplorer #UX #softcorpremium
What's New: Intel Profiles Deliver Crucial Information, Context About Threats - Microsoft Community Hub
Intel Profiles now provide crucial information and context about threats, according to a post in the Microsoft Community Hub. The profiles use threat intelligence to provide security teams with the necessary details to help them identify and address threats. The profiles include a summary of the threat, its severity, and the potential impact on the affected systems. The profiles also provide information on the indicators of compromise (IOCs) that can help identify and remediate the threat.
#IntelProfiles #Threats #softcorpremium
Increasing Transparency into Azure Active Directory's Resilience Model - Microsoft Community Hub
Microsoft has announced two new ways to enhance Azure AD's transparency and resilience capabilities. Firstly, administrators can now view the actual SLA performance of their tenant in addition to the global SLA attainment for all tenants. Secondly, improvements have been made to the automatic backup authentication service to provide seamless protection for mission-critical applications and services. These updates aim to increase confidence in Azure AD's resilience and provide users with deeper insights into their own applications and services' performance.
#AzureAD #SLA #transparency #softcorpremium
Amazon Security Lake is now generally available | AWS Security Blog
Amazon Security Lake is now generally available for AWS customers. It is a fully managed, scalable, and centralized data lake that allows customers to store, tag, and classify data from various security services and data sources. Security Lake enables customers to analyze and identify security threats, investigate incidents, and meet regulatory compliance requirements. It also integrates with AWS security services like Amazon GuardDuty and AWS Security Hub. With the availability of Security Lake, AWS customers can now easily manage their security data and improve their security posture.
#Amazon #SecurityLake #AWS #softcorpremium
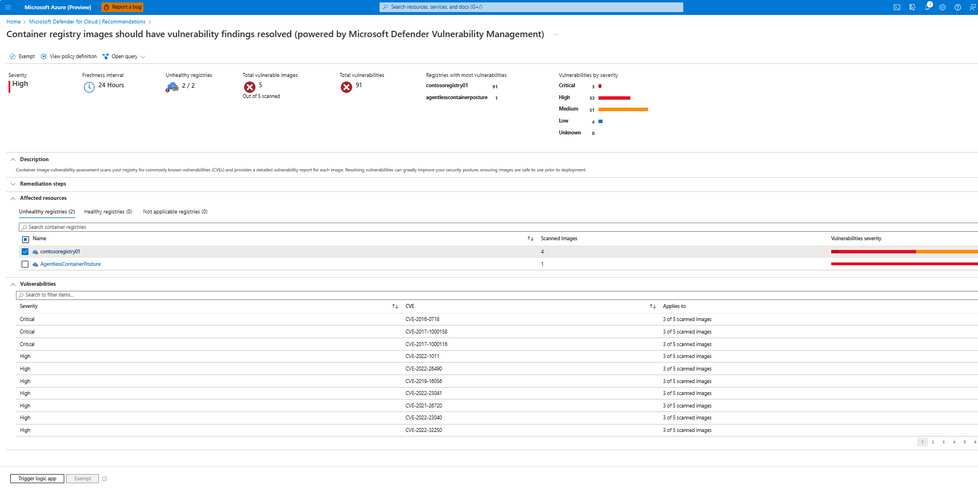
Your Ultimate Solution for Catching Container Image Exposure Before It Happens - Microsoft Community Hub
This post discusses the importance of securing container images and the vulnerabilities that come with it. It introduces the Azure Container Registry as a secure and scalable way to store and manage container images within the Azure ecosystem. It also highlights the significance of uncovering image vulnerabilities and creating a robust security strategy to protect sensitive data, reputation, and customer trust.
#containersecurity #AzureContainerRegistry #softcorpremium
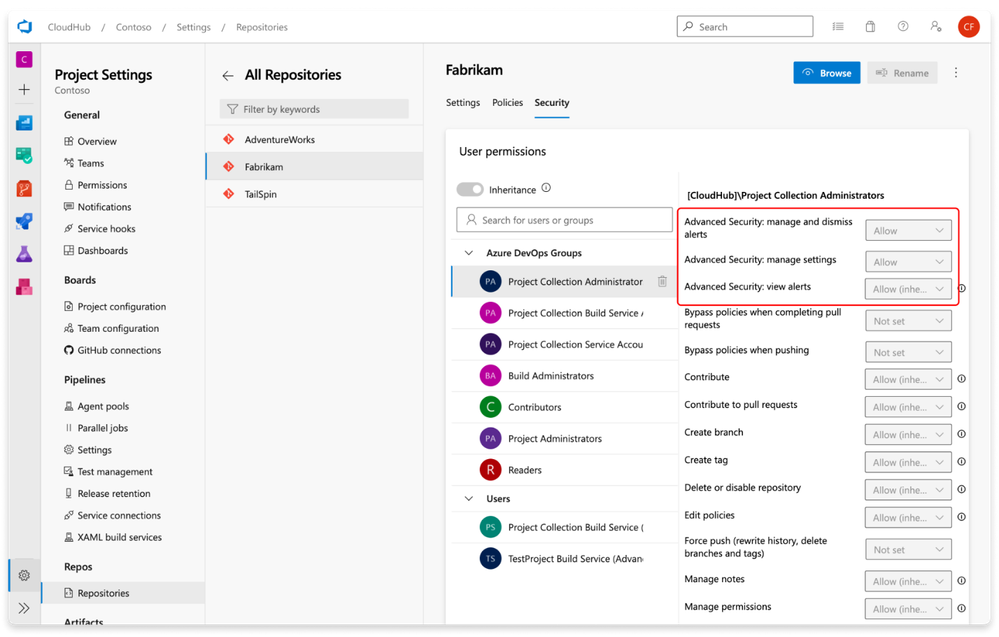
GitHub Advanced Security in Azure DevOps service with industry leading capabilities. - Microsoft Community Hub
GitHub Advanced Security is integrated into Azure DevOps, allowing for enhanced developer productivity without sacrificing security. It includes features such as secret scanning, dependency scanning, and CodeQL code scanning to detect vulnerabilities in early stages of development. The platform also offers straightforward remediation guidance and has a lower rate of false positives. Permissions and access levels can be adjusted, and alerts can be viewed and dismissed by project administrators.
#ShiftLeftSecurity #SecretScanning #CodeQL #softcorpremium
Container security fundamentals part 4: Cgroups | Datadog Security Labs
Managing system resources can be a challenge when multiple processes are running on a host. To tackle this problem, Linux relies on control groups (cgroups) to manage each process's access to resources, such as CPU and memory. Docker and other containerization tools use cgroups to restrict the resources that containers can use, which can help avoid 'noisy neighbor' issues. In this post, we will take a closer look at cgroups and explore how they ensure that each process has access to the resources it requires to operate efficiently.
#cgroups #Kubernetes #softcorpremium
Barracuda patches zero-day vulnerability exploited since October | CSO Online
Barracuda Networks has patched a zero-day vulnerability that had been exploited since October to backdoor customers' Email Security Gateway appliances with custom malware and steal data.
#Barracuda #vulnerability #softcorpremium
How to check for new exploits in real time? VulnCheck has an answer | CSO Online
Cybersecurity professionals can now track the latest vulnerability exploits through VulnCheck XDB, a database of exploits and proof of concepts. The tool is designed to make their job easier and allow them to monitor for new exploits in real-time.
#VulnCheck #CSOOnline #softcorpremium
Governments worldwide grapple with regulation to rein in AI dangers | Computerworld
Governments around the world are struggling to regulate the dangers of AI, with concerns about generative AI technology creating false information and making inappropriate suggestions to users. The UK government has outlined five principles for companies to follow, while the European Commission has published the first draft of its AI Act, which includes requirements for generative AI models to mitigate against foreseeable risks. China has implemented AI regulations requiring firms to submit security assessments and ensure content generated by generative AI aligns with socialist values. Education is seen as key to tackling the spread of disinformation through technology, particularly among young people and those who are less technologically savvy.
#AI #regulation #softcorpremium
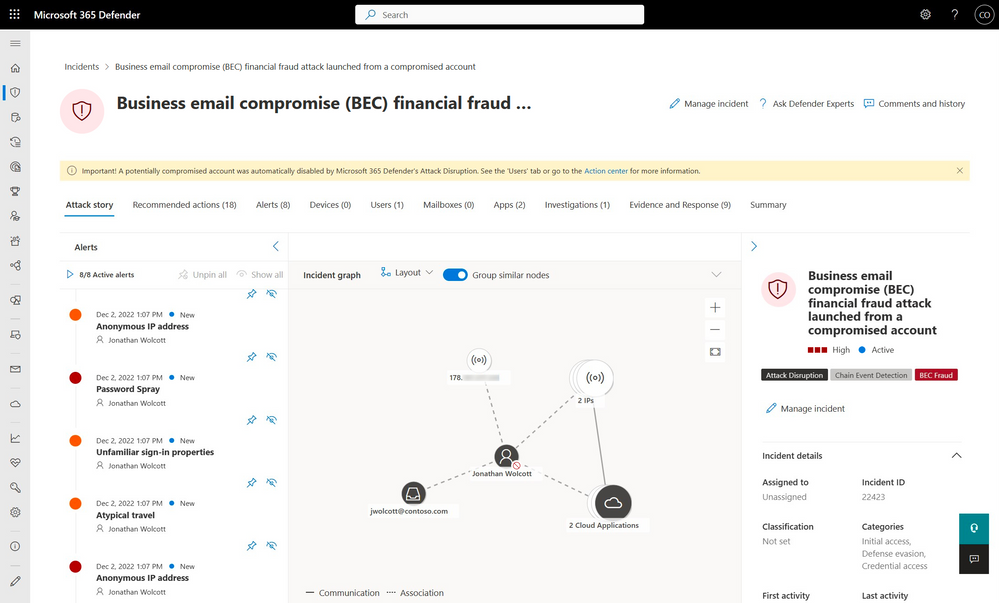
Stop attack progression with automatic disruption of ransomware and BEC attacks
Microsoft has made its automatic attack disruption capability in Microsoft 365 Defender generally available, which helps Security Operations (SOC) teams to quickly identify and contain high-impact attacks to limit the impact on organizations. The feature uses high-confidence Extended Detection and Response (XDR) signals across endpoints, identities, email, and SaaS apps to contain active cybersecurity attacks quickly and effectively. The automatic attack disruption feature is visible through visual cues in the user experience, including tags and banners, and the SOC retains full control and can easily undo any automatic actions. Additionally, experts recommend enabling ransomware protection features such as Controlled Folder Access to prevent attacks, rather than relying on remediation and incident response.
#Microsoft365Defender #automaticattackdisruption #softcorpremium
New phishing technique poses as a browser-based file archiver | CSO Online
A security researcher has uncovered a new phishing technique that uses a 'file archiver in browser' exploit to trick victims into thinking they are using a legitimate archiving application in their web browser. The attacker can leverage this technique when a victim visits a .zip domain. The technique can be used to deliver malware.
#phishing #browserexploit #malware #softcorpremium
Shadow IT is increasing and so are the associated security risks | CSO Online
CISOs are still facing the problem of shadow IT, which refers to technology operated within an organization without official approval or visibility of IT department, increasing security risks. Unapproved software, unauthorized cloud services, and unmanaged devices pose a potential threat to an organization's security. This article highlights the need for companies to identify shadow IT and implement measures to mitigate the risks associated with it.
#shadowIT #securityrisks #softcorpremium
Insider risk management: Where your program resides shapes its focus | CSO Online
The post discusses the importance of where a company's insider risk management program resides in shaping its focus. It highlights that data loss from insider events are increasing despite the presence of IRM programs. The author, who has over 30 years of experience dealing with such issues, suggests that prevention and detection of insider risk should be a priority for businesses.
#InsiderRiskManagement #IRM #softcorpremium
Sysdig adds “end-to-end” detection and response to CNAPP | CSO Online
Cloud security company Sysdig has integrated cloud detection and response (CDR) into its cloud-native application protection platform (CNAPP), allowing the platform to detect threats with 360-degree visibility. This makes Sysdig the first vendor to offer this consolidation, according to the company.
#cloud #security #softcorpremium
How the combination of XDR and SIEM can improve SOC operations | CSO Online
The combination of extended detection and response (XDR) and security information and event management (SIEM) solutions can improve security operations center (SOC) operations by providing end-to-end threat visibility, correlating and prioritizing security alerts, and using AI and ML to surface the most pressing security alerts. This can help SOC teams cut down on alert fatigue, decrease their mean time to acknowledge and respond to threat alerts, prioritize attention, and reduce the time needed for reporting and post-incident activity. SOC teams face challenges such as a growing number of attack vectors, an increase in cyberthreat activity, a widening cybersecurity skills gap, and a lack of skilled cybersecurity workers.
#XDR #SIEM #softcorpremium
Introducing LOOBins. Announcing the release of LOOBins, a… | by Brendan Chamberlain | May, 2023 | Medium
Brendan Chamberlain has announced the release of LOOBins, a new open-source project that aims to help cybersecurity professionals understand how various macOS binaries could be used for malicious purposes. LOOBins is a library of macOS binaries that can be used for “living off the land” techniques, and it provides example uses of each binary, recommendations and signatures on how to best detect malicious activity, and links to other third-party resources. LOOBins can be accessed through its website, and it can also be programmatically consumed using the JSON API or by using the Python SDK/CLI tool, PyLOOBins.
#macOS #cybersecurity #LOOBins #softcorpremium
SMBs and regional MSPs are increasingly targeted by state-sponsored APT groups | CSO Online
APT attacks targeting small- and medium-sized businesses (SMBs) have increased significantly over the past year. Cybersecurity firm Proofpoint analyzed its telemetry data more than 200,000 SMB customers and saw a rise in phishing campaigns originating from APT groups, particularly those serving Russian, Iranian, and North Korean interests.
#SMBs #MSPs #state-sponsored #APT #cybersecurity #phishing #softcorpremium
SAFE Security claims to predict data breaches with new generative AI offering | CSO Online
SAFE Security has launched Cyber Risk Cloud of Clouds, a new offering that uses generative AI to help businesses predict and prevent cyber breaches. The service answers questions about a customer’s cybersecurity posture and generates likelihoods for different risk scenarios, including the likelihood of a business suffering a ransomware attack in the next 12 months and the dollar impact of an attack. The service enables organisations to make informed, prognostic security decisions to reduce risk. SAFE’s generative AI chat interface SafeGPT, powered by LLM models, provides stakeholders with a clear and comprehensible overview of an organisation’s cybersecurity posture.
#generativeAI #cybersecurity #data breaches #softcorpremium


:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/O5DUYMRBNVAFHCHSYEXEKXCJUU.jpeg)