💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Sophos launches managed detection and response for Microsoft Defender - Back End News
Sophos has launched Sophos Managed Detection and Response (MDR) for Microsoft Defender, a managed service that improves the security of Microsoft environments. The service provides threat response capabilities and protection against data breaches and cyberattacks. It integrates telemetry from various Microsoft Security tools, consolidating and prioritizing the data to identify and mitigate threats more effectively. The service aims to support organizations without requiring them to replace their existing technologies. According to IDC research, despite significant investments in cybersecurity tools, 65% of organizations have experienced a significant ransomware event in the past year.
#Cybersecurity #DataProtection #softcorpremium
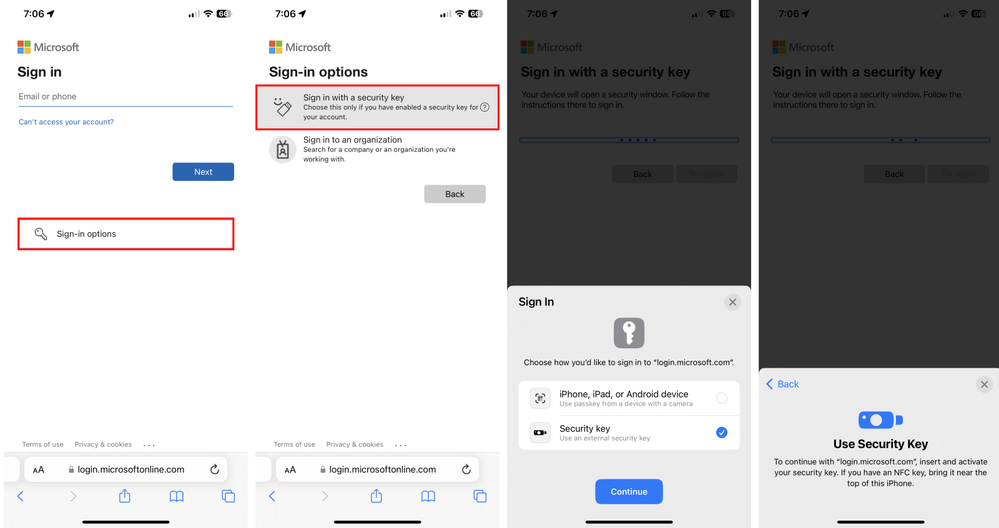
Advancing Modern Strong Authentication - Microsoft Community Hub
Microsoft is encouraging users to move away from phone-based authentication methods, such as SMS and voice, due to their vulnerabilities. A recent study by Microsoft found that SMS is 40% less effective than their Authenticator app in stopping bad actors. Despite this, 44% of multi-factor authentication (MFA) traffic still uses SMS and voice calls. To address this, Microsoft is improving the registration campaign capabilities for strong authentication and releasing FIDO2 support for iOS and macOS browsers. FIDO2 security keys provide strong, phishing-resistant authentication. These changes aim to improve MFA and protect users.
#MicrosoftSecurity #StrongAuthentication #MFAimprovement #softcorpremium
Microsoft Sentinel’s Upgraded Entity Pages
Microsoft Sentinel has announced the public preview of upgraded entity pages, offering enhanced insights and improved latency reduction for more effective security investigations. The update includes comprehensive entity data, a revamped timeline UI, and the ability to add IPs to Threat Intelligence. The integration of the Log Analytics window also provides a more streamlined investigative experience. These improvements aim to provide a smoother and faster user experience, keeping security teams one step ahead of potential threats.
#MicrosoftSentinel #EnhancedSecurityInvestigations #StreamlinedUserExperience #softcorpremium
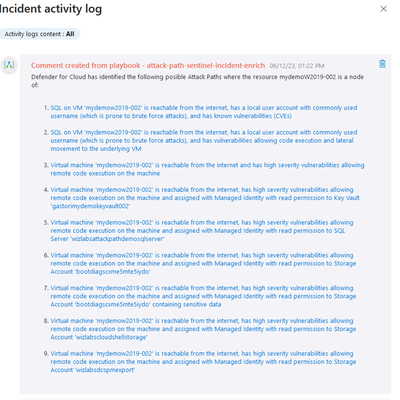
Incident Triage: Microsoft Defender for Cloud Attack Path Analysis and Microsoft Sentinel - Microsoft Community Hub
This article discusses the challenges faced by security analysts in triaging cybersecurity incidents in cloud environments and the solution developed by Microsoft using Microsoft Defender for Cloud Attack Path Analysis and Microsoft Sentinel. The solution is an Azure Logic App that automates incident triaging by identifying attack paths and enriching incident data. It improves response times, prioritizes incidents, enhances collaboration, and strengthens the overall security posture. The article also provides instructions on configuring and executing the Logic App.
#cybersecurity #incidenttriaging #cloudsecurity #softcorpremium
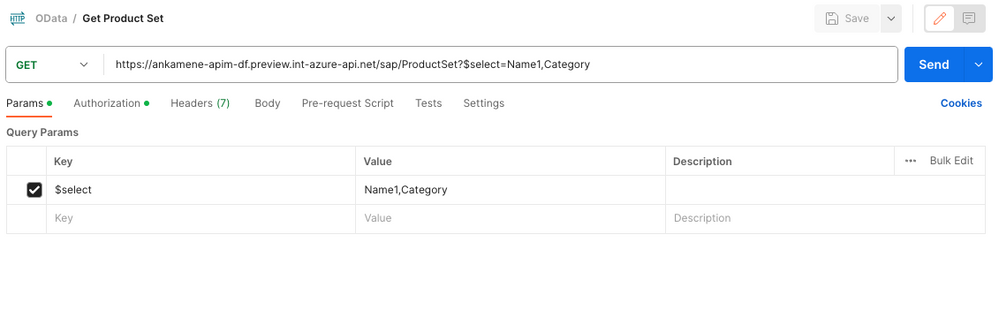
Publish, Protect and Validate OData APIs in API Management - Microsoft Community Hub
Azure API Management has announced the public preview of the OData API type. This allows users to secure and protect OData APIs with standard API protections, such as authentication and rate limiting. This new capability eliminates the need to convert OData metadata to OpenAPI before publishing in API Management. The blog provides an example of importing and protecting an OData API from SAP and explains how to create an OData API within the Azure API Management service. The introduction of the OData API type also includes a new policy for OData request validation. Users can further enhance the security of their OData APIs by utilizing the various policies available in API Management. The OData API type in Azure API Management is currently in public preview.
#AzureAPIManagement #ODataAPI #APIsecurity #softcorpremium
Become a Microsoft Priva Ninja - Microsoft Community Hub
The Ninja Training Series by Microsoft Priva provides resources and training modules to help users master privacy management and compliance with regulations like GDPR and CCPA. The series is divided into beginner, intermediate, and advanced levels, covering topics such as risk management and subject rights requests. Microsoft Priva offers solutions to identify and mitigate privacy risks, automate privacy operations, empower employees to handle data responsibly, and manage subject rights requests efficiently. The Subject Rights Requests module helps organizations fulfill data subject requests through automation, insights, and workflows. Both modules offer interactive guides for practical application of the knowledge gained.
#PrivacyManagement #ComplianceTraining #SubjectRightsRequests #softcorpremium
Monitor AKS cluster security using Syslog and Microsoft Sentinel - Microsoft Community Hub
The blog post discusses how Azure customers can use Microsoft Sentinel to ingest and analyze Syslog data from their AKS clusters. By sending Syslog data to Sentinel, users can monitor the security and health of their AKS workloads, detect and respond to threats, troubleshoot issues, and track historical changes. The process involves enabling Syslog collection on AKS clusters using Azure Monitor - Container Insights and setting up a Sentinel workspace. Once enabled, users can analyze Syslog data using various capabilities in Sentinel such as the Overview dashboard, built-in Syslog overview workbook template, hunting queries, and querying the Syslog table.
#AzureSecurity #CloudMonitoring #AKS #softcorpremium
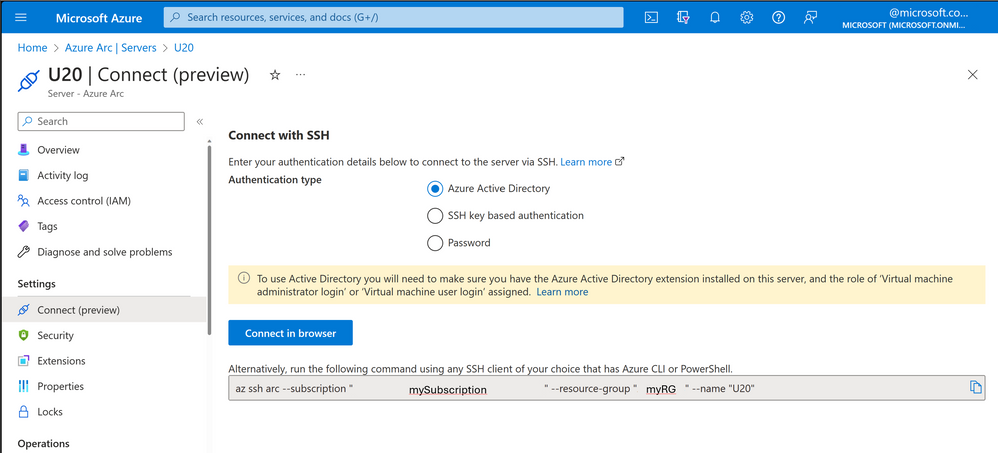
SSH for Azure Arc is now generally available! - Microsoft Community Hub
Microsoft is announcing the general availability of SSH for Azure Arc, a tool that allows users to securely connect to Azure Arc-enabled servers via SSH without the need for a public IP address or additional inbound ports. This feature is available for both Linux and Windows machines and supports existing OpenSSH-based automation and tooling. Users can easily connect to their servers in a simplified and automatable manner using Azure CLI or Azure PowerShell commands. SSH traffic is sent over the existing connection between the Azure Arc agent and Azure, eliminating the need for additional firewall ports or exposing the machine to the internet.
#AzureSSH #AzureArc #softcorpremium
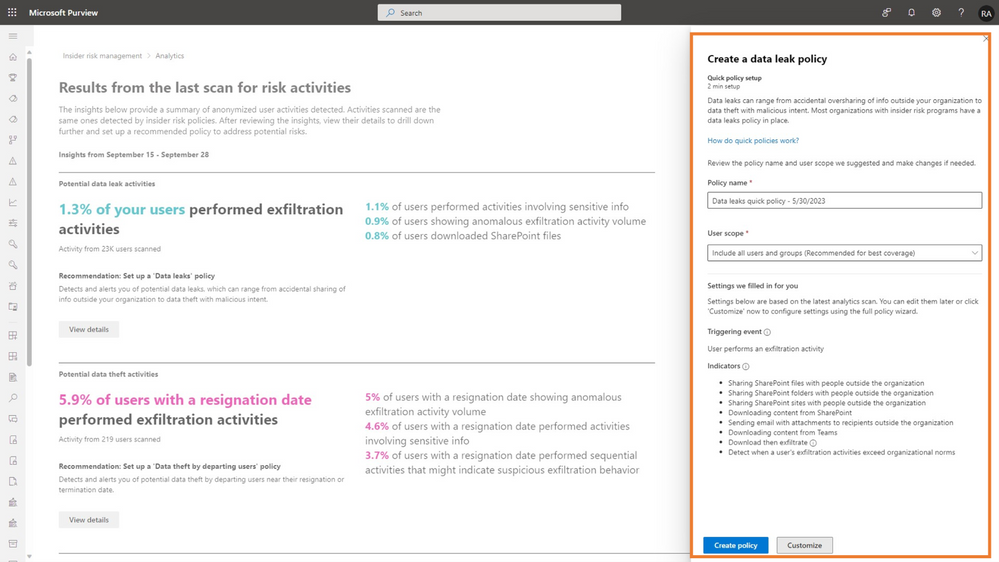
New Insider Risk Management features in general availability - Microsoft Community Hub
Microsoft has announced the general availability of more than 25 features for its Insider Risk Management solution, which helps government and commercial customers protect sensitive data from insider threats. The solution includes machine learning models and ready-to-use indicators to detect risks such as data theft and security violations. New features include ML-enabled cumulative exfiltration detection, high-quality insider risk alerts with sequence detections, integration with Microsoft Purview Communication Compliance, and more built-in indicators. The solution also includes features to reduce noise and streamline risk detection, as well as analytics and quick policy setup for easy implementation.
#InsiderRiskManagement #DataProtection #SecuritySolutions #softcorpremium
Palo Alto Networks: Malware posing as AI tool targets Android devices - Back End News
Palo Alto Networks' research has found that threat actors are spreading malware disguised as the AI Chatbot ChatGPT, targeting Android devices. The malware, disguised as \"SuperGPT\" and \"ChatGPT\" apps, sends premium-rate text messages resulting in charges for victims. The malware can steal sensitive information, spy on user activities, and cause financial losses. The digital code-signing certificate used in the malware is associated with an attacker named \"Hax4Us.\" The company advises users to be cautious when downloading applications and to protect their devices with security solutions.
#cybersecurity #malwarethreats #androidsecurity #softcorpremium
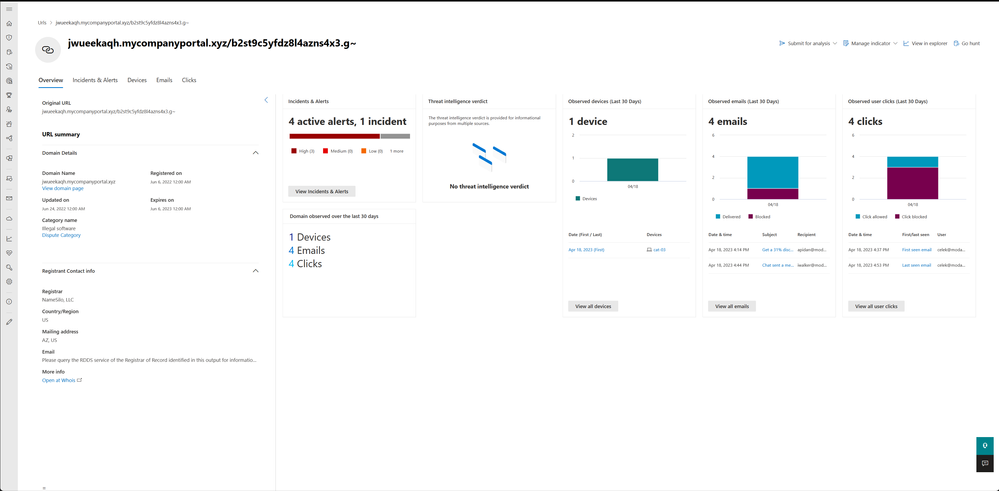
Investigate URLs and domains more efficiently with the new URL page - Microsoft Community Hub
Microsoft has introduced a new URL page in Microsoft 365 Defender to help SOC analysts investigate and manage URLs more effectively. The page offers enhanced functionality, allowing analysts to view all data related to URLs in one place and pivot to relevant tabs for deeper investigation. Analysts can tag, submit, and block URLs, and gain valuable insights into the popularity and reputation of a URL or domain. The new URL page streamlines workflows and improves efficiency for SOC teams, further strengthening cybersecurity efforts.
#Microsoft365Defender #SOCAnalysts #cybersecurity #softcorpremium
Announcing Microsoft Defender for Cloud capabilities to counter identity-based supply chain attacks - Microsoft Community Hub
Cloud supply chain attacks, specifically identity-based supply chain attacks, have become a growing concern. These attacks occur when attackers gain access to a target organization through trusted suppliers or third-party service providers. The use of cloud computing introduces unique risks to these attacks. Attackers often target service providers who have excessive permissions and access to multiple organizations. Microsoft Defender for Cloud offers a new alert enrichment feature to help detect and remediate these threats. Implementing security best practices and creating visibility for delegated access operations can help minimize the risk of identity-based supply chain attacks.
#cloudsecurity #supplychainattacks #identitybasedattacks #softcorpremium
Kaspersky: Scammers turn to Threads to spread phishing links - Back End News
Kaspersky has discovered that scammers are taking advantage of the popularity of Meta's social networking platform, Threads, by creating phishing pages that lure users. The scammers claim to offer a web version of Threads, even though Meta has not developed one. Users who fall for the scams may expose their personal information tied to Facebook and Instagram. Additionally, scammers are capitalizing on the rise of cryptocurrency phishing by creating a non-existent Threads Coin. Kaspersky advises users to be cautious when downloading software, use strong passwords and two-factor authentication, and employ reliable security solutions.
#CyberSecurity #PhishingScams #OnlineSafety #softcorpremium
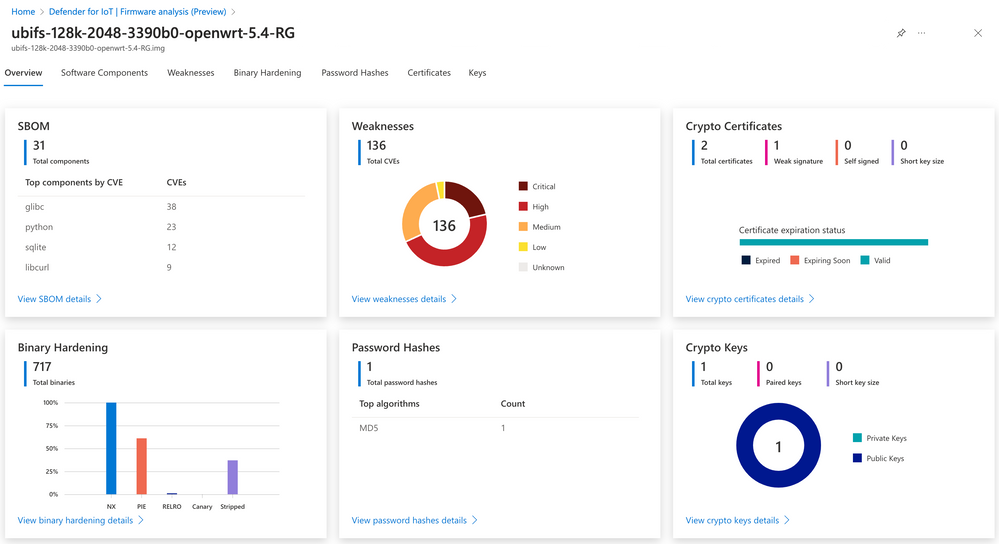
Analyze IoT/OT device firmware with Microsoft Defender for IoT
Microsoft has announced the availability of firmware analysis capability in Microsoft Defender for IoT, now in public preview. This capability allows organizations to analyze the firmware of IoT and OT devices, providing insights into software inventory, vulnerabilities, and potential anomalies. Firmware analysis includes identifying software packages and vulnerabilities, assessing binary hardening, and identifying weak accounts and cryptographic materials embedded in the device. This tool aims to provide better visibility and security for IoT environments. Feedback on the firmware analysis capability is welcomed by Microsoft. To learn more, click here.
#MicrosoftDefenderforIoT #FirmwareAnalysis #softcorpremium
How to install Microsoft Defender for Identity - Azure Cloud & AI Domain Blog
This blog provides a step-by-step guide on how to install Microsoft Defender for Identity (MDI) in the Azure Cloud. It outlines the prerequisites, licensing requirements, and necessary permissions. The blog also explains how to create a Defender for Identity workspace, validate access to the Defender cloud service, and add a directory service account. It further covers the installation of the MDI sensor and provides tips for troubleshooting.
#MicrosoftDefenderforIdentity #AzureCloudInstallation #MDISensorInstallation #softcorpremium
Application Security Testing in the Cloud: A Practical Guide
Application security testing, or AST, is a crucial component of software development that involves identifying and mitigating potential vulnerabilities in an application. In the cloud environment, application security testing becomes even more critical due to unique security challenges. The shared responsibility model outlines the responsibilities of the cloud service provider and the customer in ensuring application security.
#applicationsecuritytesting #cloudsecurity #shiftleft #softcorpremium
Defender for Endpoint on Linux now supports eBPF-based sensor
Microsoft has introduced a new eBPF-based sensor for Microsoft Defender for Endpoint on Linux in public preview. This sensor provides improved system stability, reduced log noise, optimized performance, and increased event rate throughput for Linux-based machines. It replaces the previous auditd event provider and does not require a kernel module, increasing system stability. The eBPF sensor will be gradually rolled out to all insider machines. Users will need the latest version of Microsoft Defender for Endpoint to utilize this new sensor.
#MicrosoftDefenderforEndpoint #LinuxSecurity #eBPF #softcorpremium
Public Preview of Transparent Data Encryption and Credential Rotation for Arc SQL Managed Instance
Microsoft is announcing the Public Preview of Transparent Data Encryption (TDE) and Service-Managed Credential Rotation for Arc-enabled SQL Managed Instance. These features enhance data security by encrypting-at-rest all databases and regularly refreshing access credentials. Businesses can choose between customer-managed or service-managed encryption keys, and the deployment process involves creating a Kubernetes secret and updating the SQL MI Custom Resource spec. This release aims to provide robust protection for sensitive information and mitigate potential security vulnerabilities.
#DataSecurity #Encryption #MicrosoftAnnouncement #softcorpremium
AWS Marketplace Vendor Insights now includes PCI DSS, HIPAA, and GDPR certifications
AWS Marketplace has expanded its Vendor Insights security profiles to include additional certifications such as PCI DSS, HIPAA, and GDPR compliance. This update allows buyers to quickly find products that meet their security and certification standards, reducing the need for extensive IT security assessments. Using Vendor Insights can save buyers months of effort by providing access to validated security profiles and notifications for security and compliance events. Vendor Insights is available in all public AWS regions where AWS Marketplace is accessible. To learn more, visit the AWS Marketplace Vendor Insights webpage.
#AWSMarketplace #VendorInsights #SecurityCompliance #softcorpremium
Chinese APT Cracks Microsoft Outlook Emails at 25 Government Agencies
A Chinese Advanced Persistent Threat (APT) group known as \"Storm-0558\" has successfully hacked into the Microsoft Outlook email accounts of 25 government agencies in Western Europe and the US, including the US State Department. The group used a token validation vulnerability to gain access to privileged state emails for several weeks. The hackers targeted specific officials' email accounts and it is unclear what sensitive information they were able to access. Microsoft has reported that they have mitigated the cyberespionage campaign and have contacted all known victims. This incident highlights the increasing sophistication of Chinese threat actors and the need for stronger cybersecurity measures.
#CybersecurityThreats #StateDepartmentHacked #ChineseAPT #softcorpremium
Azure Role Assignment Hygiene - Microsoft Community Hub
This blog post discusses the importance of maintaining good Azure Role Assignment Hygiene in order to ensure security, compliance, and simplify management. The author provides two scripts that can be used as Azure Automation runbooks to regularly review and clean up role assignments. The first script removes orphaned permissions, while the second script removes permissions for disabled users. The author emphasizes the need for a broader strategy that includes regular reviews and audits of role assignments. The post concludes by stating that a clean Azure environment is essential and encourages readers to stay tuned for more optimization tips.
#AzureRoleAssignmentHygiene #AzureAutomation #softcorpremium