💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
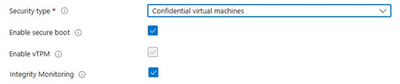
Announcing General Availability of Confidential VMs in Azure Virtual Desktop - Microsoft Community Hub
Microsoft has announced the General Availability of several security features for confidential VMs and Trusted Launch via AVD Host Pool Provisioning. Confidential VMs provide memory encryption and integrity protection, while Trusted Launch protects against advanced attacks and secures VMs. Windows 11 22H1 is now supported in confidential VMs, and additional features such as OS disk encryption and integrity monitoring are available. Trusted Launch is now enabled by default for all Windows images. Users can deploy confidential VMs and enable Trusted Launch through the Azure Portal. Microsoft provides further information and best practices for Azure Virtual Desktop security.
#ConfidentialVMs #TrustedLaunch #AzureVirtualDesktopSecurity #softcorpremium
Public Preview: Support for DRS and Mask sensitive data on Application Gateway WAF - Microsoft Community Hub
Azure WAF on Application Gateway with Default Rule Set is now available in public preview. The Microsoft Default Rule Set is based on OWASP Core Rule Set (CRS) 3.3.2 and includes additional proprietary protection rules. Users can enable log scrubbing rules to protect sensitive data in WAF logs. It is important to regularly update the security configuration of the WAF policy.
#AzureWAF #ApplicationGateway #WebApplicationFirewall #softcorpremium
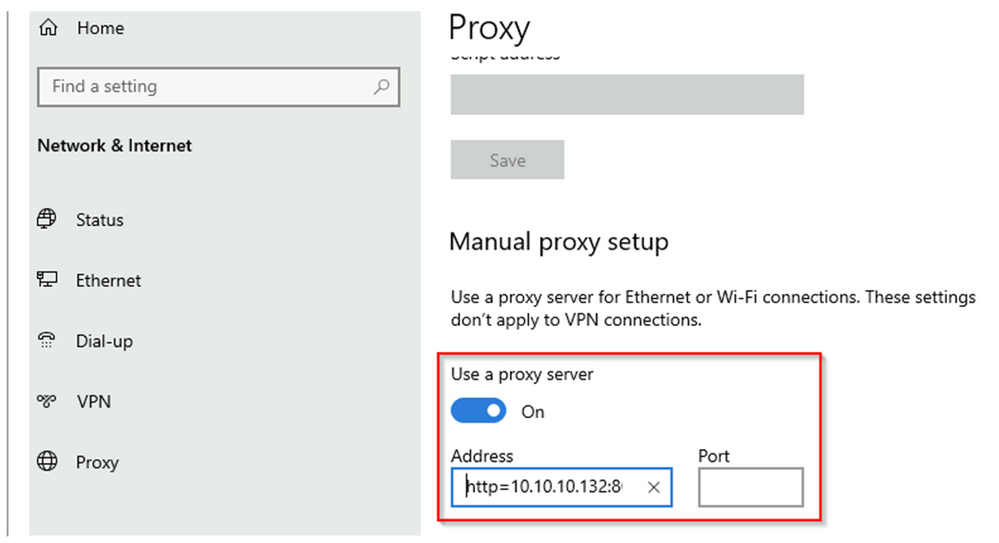
Demystifying Explicit proxy: Enhancing Security with Azure Firewall - Microsoft Community Hub
The blog post discusses the importance of secure outbound connectivity for organizations in the cybersecurity threat landscape. It introduces the Explicit proxy feature available in Azure Firewall, which acts as an intermediary between clients and servers, allowing for fine-grained traffic control and centralized management. The feature also provides advanced logging and analytics capabilities. The blog post provides instructions on how to enable and configure the Explicit proxy feature and demonstrates how to configure client applications to use it. Overall, the Explicit proxy feature in Azure Firewall enhances network security and protects against cyber threats.
#networksecurity #cybersecuritythreats #AzureFirewall #softcorpremium
Demystifying Explicit proxy: Enhancing Security with Azure Firewall - Microsoft Community Hub
The blog post discusses the Explicit proxy feature in Azure Firewall, which is a powerful tool for securing outbound connectivity and addressing cybersecurity concerns. By enabling Explicit proxy, organizations can enforce granular traffic control, implement content filtering policies, and ensure secure access for users. The feature provides centralized management, advanced logging, and analytics capabilities, helping organizations protect against cyber threats. The blog post also provides instructions on how to enable and configure the Explicit proxy feature in Azure Firewall.
#AzureFirewall #Cybersecurity #ProxyFeature #softcorpremium
Exploring Azure Firewall's Threat Protection - Microsoft Community Hub
This blog post discusses the threat protection capabilities of Azure Firewall, a cloud-native firewall-as-a-service solution. It explains how customers can use Azure Firewall to safeguard their workload deployments in Azure by leveraging features such as application and network-level filtering rules, integration with Microsoft Threat Intelligence feed, and high availability with built-in auto scaling. The blog also covers the importance of URL filtering, TLS inspection, and intrusion detection and prevention system (IDPS) in enhancing security and protecting against various threats. Overall, Azure Firewall offers a comprehensive set of features to improve security posture and protect against future threats in Azure cloud workloads.
#AzureFirewall #CloudSecurity #ThreatProtection #softcorpremium
Manage your security settings across Windows, macOS, and Linux natively in Defender for Endpoint
Microsoft has announced a unified security settings management experience in the Microsoft 365 Defender portal that allows organizations to manage endpoint security settings across Windows, macOS, and Linux devices. This integration of Microsoft Intune's endpoint security experience into the Microsoft Defender for Endpoint provides a single source of truth for IT and security teams and simplifies the device onboarding process. The update also includes the ability to create and edit AV policies directly from the portal and automatic syncing of policies with Microsoft Intune. Users can enable the preview features and review their configuration settings to prepare for the upgrade.
#UnifiedSecuritySettings #DeviceOnboarding #Microsoft365Defender #softcorpremium
Introducing Restricted Management Administrative Units in Microsoft Entra ID - Microsoft Community Hub
Microsoft has introduced restricted management administrative units in its Entra ID platform. This feature allows users to protect specific accounts, security groups, or devices from modification by tenant-level administrators. It is useful for safeguarding sensitive user accounts, ensuring that certain accounts can only be modified by designated administrators from specific countries, and restricting access to sensitive data. By placing sensitive objects in these units, only explicitly assigned administrators can make changes, preventing tenant-level administrators from modifying them. Users can easily create and manage these units to secure sensitive resources in their tenant.
#administrativeunits #securitymanagement #sensitiveresources #softcorpremium
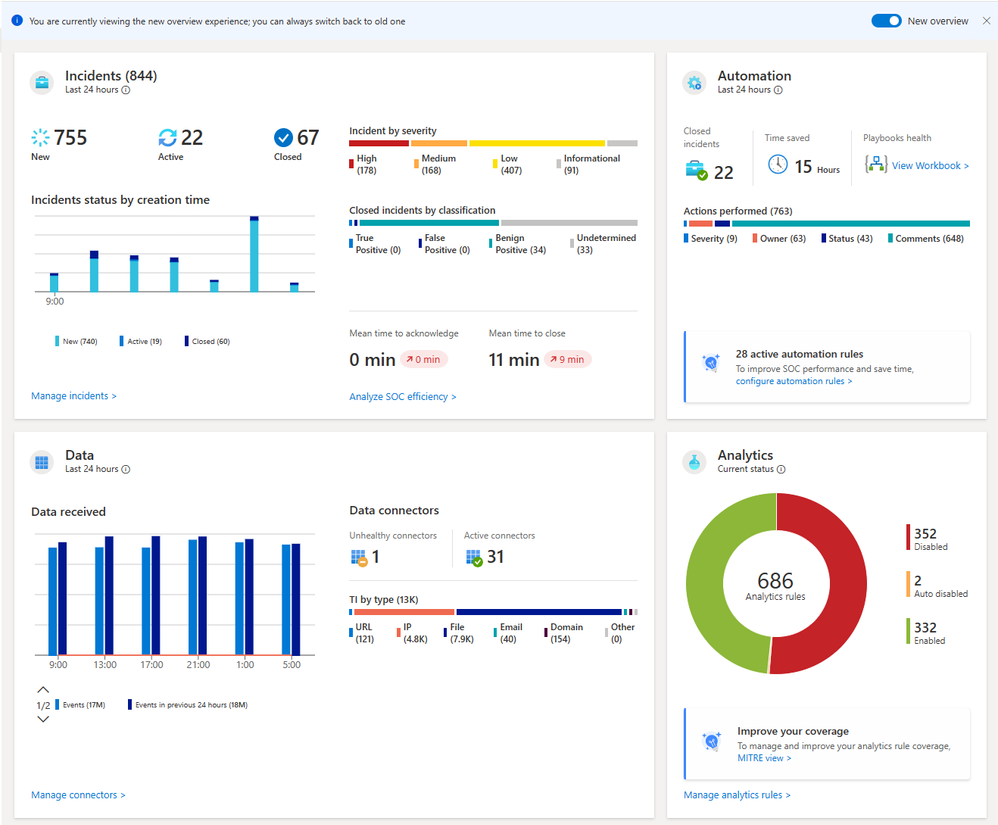
Deep dive into Microsoft Sentinel’s new Overview dashboard - Microsoft Community Hub
The Microsoft Sentinel Overview dashboard provides operational and health insights for the main function domains of Microsoft Sentinel. It includes widgets that display data on incidents, data connectors, automation, threat intelligence, and analytics. The code provided calculates mean time to acknowledge and close incidents, counts incidents closed by automation, and displays the status of data connectors. The dashboard also provides visibility into ingestion volumes, threat intelligence records, and the status of analytics rules. The Alert Rules API allows users to adapt and reuse queries and create custom detection rules. The blog post also discusses monitoring the health and role of Microsoft Sentinel SAP systems.
#MicrosoftSentinel #OperationalInsights #ThreatIntelligence #softcorpremium
AD FS to Microsoft Entra | How to migrate your cloud apps
This summary discusses the migration process from Active Directory Federation Services (AD FS) to Microsoft Entra ID (Azure Active Directory). The key blockers that were present in AD FS, such as certificate-based authentication, group filtering, group transformation, and token augmentation, have been removed in Microsoft Entra ID. Additional capabilities include conditional access and phish-resistant passwordless authentication. The management and IT experience of Microsoft Entra ID is also discussed, highlighting the simplified management, increased security, and improved user experience. The steps to migrate from AD FS to Microsoft Entra ID are outlined, including identifying connected apps, using the AD FS Connect Health tool, and configuring and updating apps in Microsoft Entra ID. Detailed reports for application usage and identity-based risks are available in Microsoft Entra ID. Resources and tutorials for migration are provided.
#ADFSmigration #AzureActiveDirectory #MicrosoftEntraID #softcorpremium
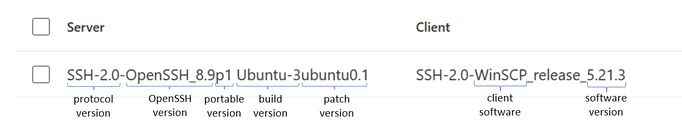
Enrich your advanced hunting experience using network layer signals from Zeek
Microsoft is deprecating certain signature action types in Advanced Hunting and introducing new action types due to the integration of Zeek. This integration provides better visibility into network sessions. The consolidation of signatures aims to improve the customer experience by reducing redundancies. Users are advised to update their queries to leverage the new action types. The article also provides information on the deprecated signatures and their corresponding alternatives. The integration of Zeek into Microsoft Defender for Endpoint allows for enhanced network threat hunting capabilities. The article discusses the use of different action types to detect specific events in network traffic, such as HTTP file downloads and SSH connections. It also provides information on analyzing ICMP, DNS, SSL, and NTLM traffic. The integration of Zeek into Microsoft Defender for Endpoint allows for the inclusion of Zeek Kerberos events, but the AdditionalFields column may not contain useful data for analysis.
#MicrosoftDefender #ZeekIntegration #NetworkThreatHunting #softcorpremium
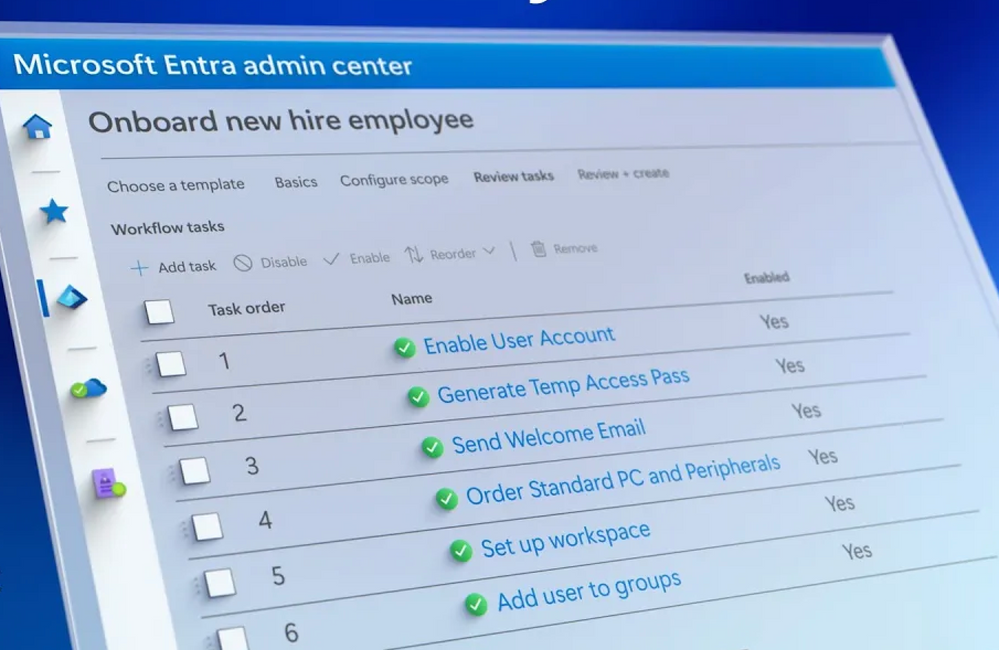
Automate onboarding & offboarding tasks with Microsoft Entra | Identity Lifecycle Management
Microsoft Entra is an identity management platform that automates the onboarding and offboarding process for users in an organization. It integrates with HR systems like Workday and SuccessFactors and offers pre-built templates to improve consistency and job satisfaction while reducing risk. The platform allows for automated onboarding tasks and real-time separation, provides access to resources, and manages hardware orders. Microsoft is inviting IT professionals to join their Tech Community to stay updated on insider knowledge. Automating identity lifecycle management tasks helps improve security and saves time. Microsoft Entra also offers automated processes for employee offboarding and allows users to track the progress and completion of tasks with a full audit log. Users can troubleshoot errors and review workflow versions for improvements.
#IdentityManagement #EmployeeLifecycleManagement #ITProfessionals #softcorpremium
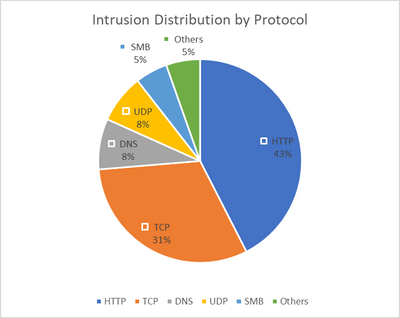
Taking Azure Firewall Premium IDPS Functionality - Microsoft Community Hub
Intrusion detection and prevention (IDPS) is a feature of Azure Firewall Premium SKU that matches traffic patterns to known malicious signatures to prevent advanced threats. Azure Firewall supports over 60,000 malicious signatures that are constantly updated. The IDPS can be configured to alert or deny suspicious traffic. Testing the IDPS configuration involves validating HTTP and HTTPS traffic by injecting malicious user agents. The IDPS logs show the blocked traffic and the corresponding signature. It is recommended to enable IDS/IPS with TLS inspection for better security. The IDS/IPS signatures are regularly updated to protect Azure environments. Zero Trust with Azure Network Security is also recommended for enhanced security.
#AzureFirewallPremium #IDPS #AzureNetworkSecurity #softcorpremium
Taking Azure Firewall IDPS on a Test Drive - Microsoft Community Hub
Azure Firewall Premium SKU supports intrusion detection and prevention (IDPS) as an advanced threat prevention mechanism. It matches traffic patterns to known malicious signatures, with over 60,000 signatures updated in real time. IDPS can be configured to alert or deny suspicious traffic based on conditions such as traffic direction and network scope. The effectiveness of IDPS can be validated by testing HTTP and HTTPS traffic, with logs showing blocked connections and the corresponding signature IDs. It is recommended to enable IDS/IPS with TLS inspection for enhanced security in Azure environments.
#AzureFirewallPremium #IntrusionDetectionAndPrevention #EnhancedSecurity #softcorpremium
Certificate Transparency Logs —What you need to know | by Teri Radichel | Cloud Security | Jul, 2023 | Medium
This article highlights the importance of Certificate Transparency Logs in ensuring the validity of TLS certificates and preventing the issuance of fraudulent certificates. It discusses the problem of fraudulent SSL certificates and the proposed solution of Certificate Transparency Logs. The article also mentions the role of public certificate authorities in validating website certificates and ensuring secure connections. It discusses the Certificate Transparency protocol and the availability of tools like SSLMate Certificate Transparency Search API to retrieve information about certificates for a specific domain. The article emphasizes the need for caution when deploying sensitive projects due to the potential for attackers to exploit these logs. It also mentions that enabling Certificate Transparency Logs is recommended by AWS and required by some browsers. The article concludes by providing information about the author, Teri Radichel, who is an editor for Cloud Security and has expertise in various security certifications and AWS.
#CertificateTransparency #TLSsecurity #CloudSecurity #softcorpremium
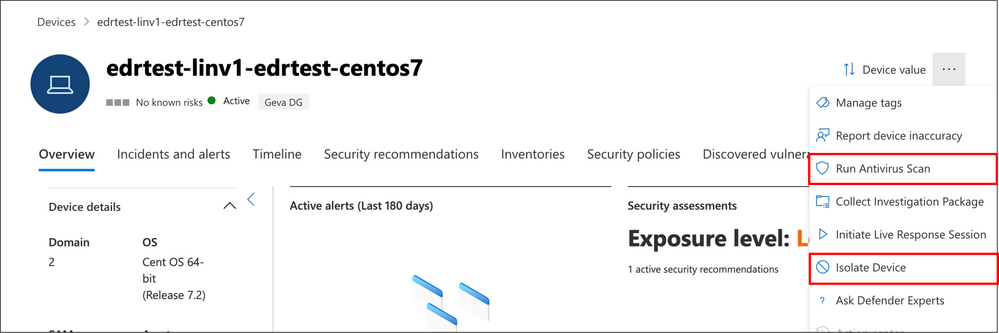
Now in Public Preview: Device isolation and AV scanning for Linux and macOS in Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is expanding its capabilities for macOS and Linux-based devices. The new features include device isolation and running antivirus scans, providing security teams with more flexibility and control in responding to cyber threats. The device isolation response action allows compromised devices to be disconnected from the network, preventing attackers from controlling the device and engaging in malicious activities. The antivirus scan response action allows for remote initiation of scans on devices to identify and remediate malware. These capabilities are now available in public preview and aim to enhance security across multi-platform enterprises.
#MicrosoftDefenderEndpoint #cybersecurity #DeviceIsolationAction #softcorpremium
Consolidating controls in Security Hub: The new controls view and consolidated findings | AWS Security Blog
The AWS Security Blog discusses the new features of AWS Security Hub, including the ability to manage controls across standards and consolidate findings. Security Hub is a cloud security posture management service that helps ensure proper configuration and mitigate security risks. It integrates with over 30 AWS services and 85 partner products to centralize security findings across AWS accounts and regions. The new features in AWS Control Tower and Security Hub allow for easier control management and prioritization of misconfigured resources. The blog also mentions API operations for managing security controls and the availability of consolidated control findings. Enabling consolidated control findings can reduce noise and improve efficiency in investigating and remedying security issues. Users are encouraged to review and enable these features and provide feedback.
#AWS #SecurityHub #cloudsecurity #softcorpremium
How to enforce multi-party approval for creating Matter-compliant certificate authorities | AWS Security Blog
The AWS Security Blog discusses the process of enforcing multi-party approval for creating Matter-compliant certificate authorities. It explains how to use AWS Private CA to create the necessary certificates and outlines the roles and steps involved in the approval process. The blog also provides instructions on modifying trust relationships, creating IAM roles, and using Systems Manager to automate resource creation. It emphasizes the importance of compliance and security controls, and suggests using AWS Service Control Policies to restrict CA creation. The summary concludes by mentioning the ability to verify successful creation of the certificates in the AWS Private CA console and the availability of support and training resources.
#AWSPrivateCA #CertificateAuthority #ComplianceAndSecurityControls #softcorpremium
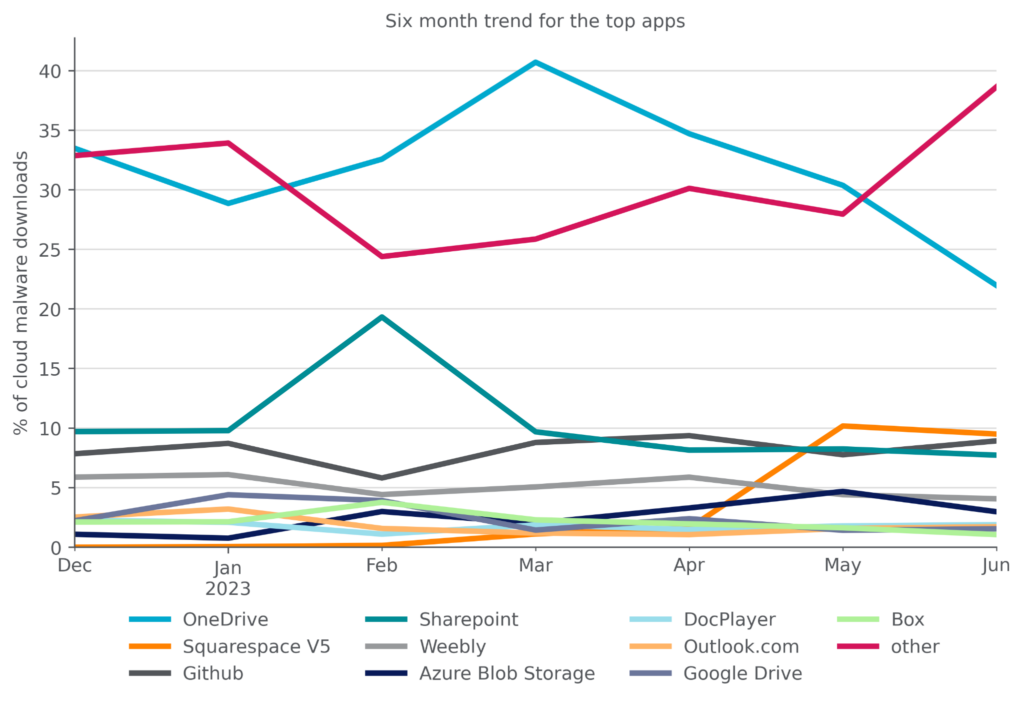
Netskope Threat Labs Stats for June 2023 - Netskope
Netskope Threat Labs released statistics on the usage of cookies on their website, highlighting the importance of essential cookies for basic website functions. Glassdoor and other websites use cookies for various purposes, such as tracking user behavior, optimizing ads, and improving user experience. The summary also discusses Netskope's security solutions, their recognition as a leader in the Gartner Magic Quadrant for Security Service Edge, and their involvement in Vision 2045. In terms of malware, attackers are using cloud apps to distribute malware, with Microsoft OneDrive being the most popular app for malware downloads. The report also mentions the types of malware and attacker tactics used, as well as the importance of advanced threat protection and security measures.
#cybersecurity #malware #securitysolutions #softcorpremium
Microsoft Entra: Simplifying Secure Access Experiences with Rebranded Azure Active Directory and New Offerings | by Jiadong Chen | Jul, 2023 | Medium
Microsoft has announced the rebranding of Azure Active Directory to Microsoft Entra ID to simplify secure access experiences. They have also introduced two new products called Microsoft Entra Internet Access and Microsoft Entra Private Access, which are part of Microsoft's Security Service Edge solution. Microsoft Entra Internet Access is a Secure Web Gateway for SaaS apps and internet traffic protection, while Microsoft Entra Private Access is a Zero Trust Network Access solution for secure access to private resources. These offerings aim to provide comprehensive security and improved access controls for users.
#MicrosoftEntraID #SecureAccess #SecurityServiceEdge #softcorpremium
Azure AD is becoming Microsoft Entra ID - Microsoft Community Hub
Microsoft is changing the name of Azure Active Directory (Azure AD) to Microsoft Entra ID as part of the expansion of their Microsoft Entra product family. This change is aimed at simplifying secure access experiences for customers and unifying Microsoft's identity and network access portfolio. The rename will not affect capabilities, pricing, or licensing plans, and all deployments and integrations will continue to work without interruption. Customers will start seeing notifications of the name change, and it will be completed across all customer-facing interfaces by the end of 2023. Additional resources are available to learn more about Microsoft Entra.
#MicrosoftEntraID #IdentityandAccessManagement #AzureAD #softcorpremium
Amazon FSx for NetApp ONTAP supports write once, read many (WORM) protection with SnapLock
Amazon FSx for NetApp ONTAP now supports SnapLock, a feature that provides write once, read many (WORM) protection. This means that data cannot be modified or deleted for a specified retention period, making it ideal for regulatory compliance and protecting against ransomware. SnapLock offers two modes of retention: Compliance, where files cannot be modified or deleted, and Enterprise, where authorized users can delete files if necessary. SnapLock volumes can be created on new file systems, with support for existing file systems coming soon.
#AmazonFSx #SnapLock #DataProtection #softcorpremium
(ISC)² Strengthens DEI Initiatives through Global Partnerships
(ISC)², an international cybersecurity certification organization, is expanding its diversity, equity, and inclusion initiatives through partnerships to promote diversity and inclusivity in the cybersecurity industry. They are collaborating with various organizations to address the workforce gap and empower underrepresented groups. Additionally, they are hosting events, webinars, and providing resources to support cybersecurity professionals and address vulnerabilities and threats in the field. There is also a mention of the use of cookies on their website and the option to customize cookie preferences.
#CybersecurityDiversity #InclusiveCybersecurity #EmpoweringUnderrepresented #softcorpremium
Less Than Half of SMBs Deploy Privileged Access Management
Less than half of small and medium-sized businesses (SMBs) have deployed privileged access management (PAM), leaving them vulnerable to cyber attacks. PAM is crucial for protecting against credential theft and lateral movement within a network. Traditional PAM solutions have been complex and expensive, making them inaccessible for smaller businesses. Cloud-based PAM solutions that are flexible, easy to use, and cost-effective are recommended to enhance security for SMBs.
#CyberSecuritySolutions #CloudPAM #ProtectingSMBs #softcorpremium
Firedome Integrates With Microsoft Defender for IoT to Enhance IoT Device Security, Using Microsoft Sentinel
Firedome, a global IoT Endpoint Protection leader, has announced its integration with Microsoft Defender for IoT, using Microsoft Sentinel. This integration combines Firedome's on-device real-time detection, prevention, and response with Microsoft Defender for IoT's network-based events, providing customers with a comprehensive view of IoT attacks. The integration allows users to create alerts, investigate security incidents, and access unique device-entry-point data for enhanced device and organizational security. The collaboration aims to empower SOC teams to detect and respond faster to cyber attacks on IoT/OT devices and networks.
#IoTSecurity #Cybersecurity #Collaboration #softcorpremium
Amazon FSx for NetApp ONTAP now supports IPSec encryption of data in transit
Amazon FSx for NetApp ONTAP now offers IPsec encryption to protect data in transit. This additional option adds to the existing encryption methods already supported by FSx for ONTAP. Nitro-based encryption is automatically enabled for data accessed directly within the same VPC or a peered VPC, while Kerberos-based encryption can be used for clients outside the VPC. The new IPsec protocol provides encryption for environments where Nitro-based encryption is not supported and there is no Active Directory available. This feature is available for new file systems and will be added to existing file systems in an upcoming maintenance window.
#FSxforONTAPencryption #datasecurity #IPsecencryption #softcorpremium