💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
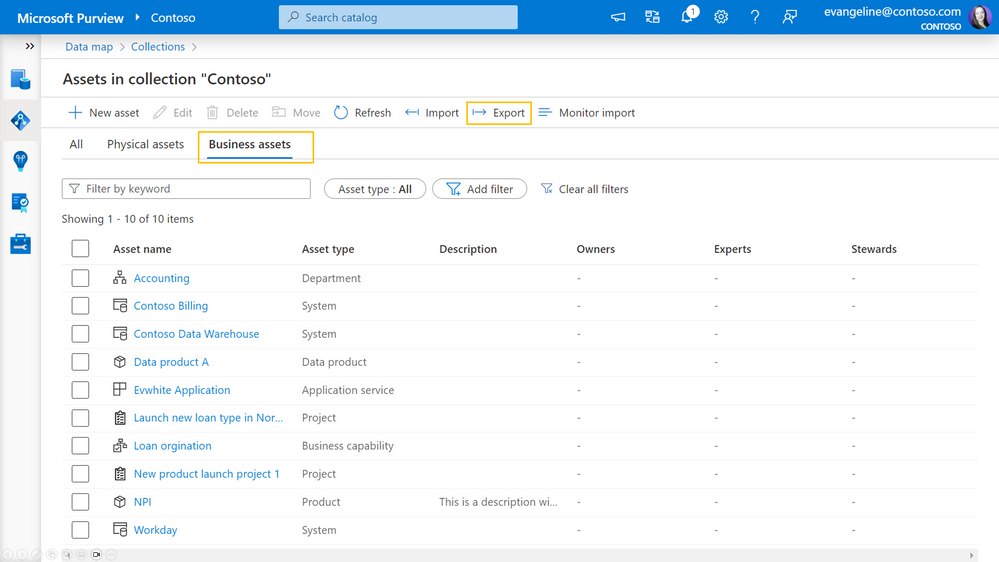
Now in preview: Export your business assets from Microsoft Purview - Microsoft Community Hub
Microsoft Purview now allows users to curate metadata by pulling information into a csv file and making bulk updates through importing. Currently, only business assets can be exported, but data assets will be supported in the future. To export, users can select the desired asset type and receive a csv file with the exported assets, guides, and chosen fields. To import, users can update the file and import it into the appropriate collection.
#MicrosoftPurview #metadatamanagement #dataassetmanagement #softcorpremium
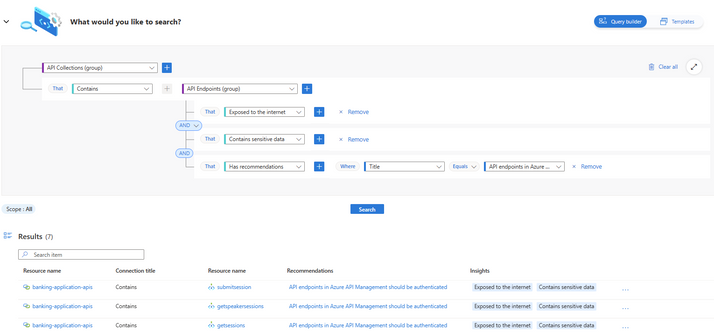
Microsoft Defender for APIs enriches Defender CSPM capabilities. - Microsoft Community Hub
Microsoft has announced the integration of Defender for APIs and Microsoft Defender for Cloud to enhance API security. Defender for APIs helps organizations prevent, detect, and respond to API security threats, such as misconfigurations and vulnerabilities, with a comprehensive set of assessment capabilities. It also provides actionable recommendations to improve API configurations. The integration allows security teams to prioritize and address critical issues more effectively. The solution offers a unified view of API security posture, enabling informed decision-making to mitigate risks. To utilize these capabilities, users need to enable Defender for APIs and onboard API endpoints to the plan.
#APIsecurity #DefenderforAPIs #MicrosoftDefender #softcorpremium
Enabling Microsoft Defender for Cloud for Arc Enabled SQL Server Machines - Microsoft Community Hub
This blog post discusses the capabilities of Microsoft Defender for SQL servers in detecting and mitigating potential threats to databases. It explains how to enable Microsoft Defender for Cloud on Azure Arc enabled SQL Server machines and provides steps for generating incidents and alerts. The post also highlights the protection and vulnerability assessment features of Microsoft Defender, as well as its support for hybrid environments and multicloud SQL servers. Overall, it emphasizes the importance of fortifying SQL Server security through the use of Microsoft Defender.
#MicrosoftDefender #SQLServerSecurity #HybridCloudSecurity #softcorpremium
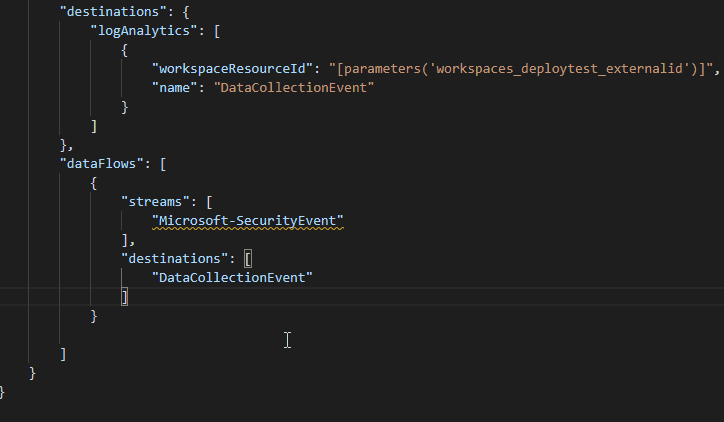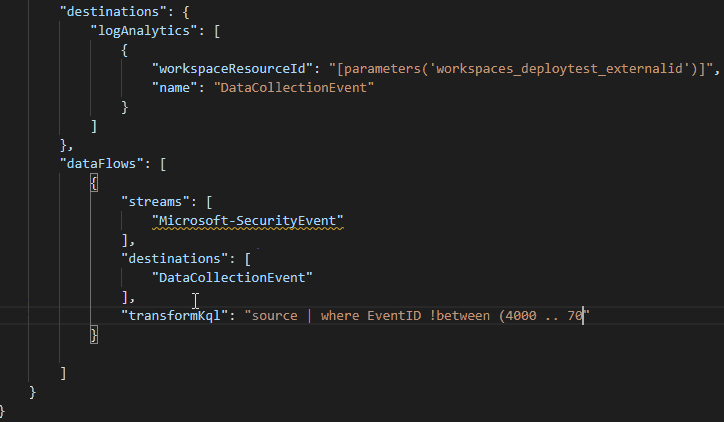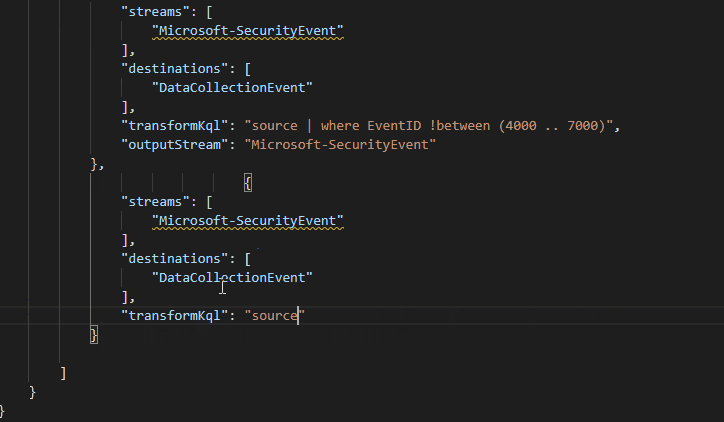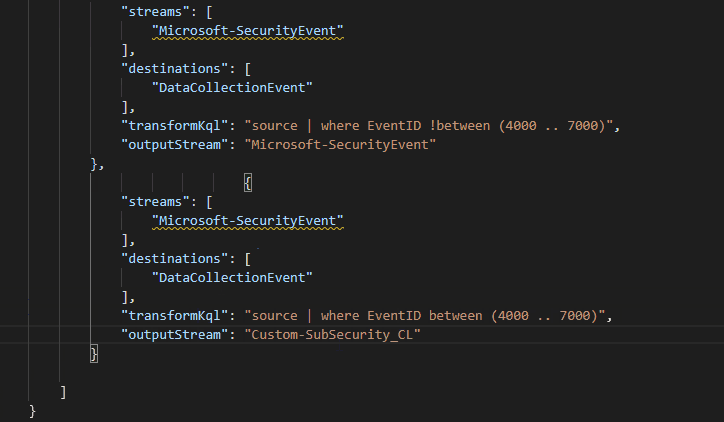
Split Microsoft Sentinel Tables with Multi-Destination Data Collection Rules - Microsoft Community Hub
The Azure Monitor team has released a new feature that allows data ingestion streams to be split into multiple tables. This feature provides benefits such as table volume management, basic log configuration, data normalization, and query performance improvement. It is particularly useful for SOC teams and organizations looking to separate valuable security data from general information. By using the basic log tier, users can reduce ingestion costs while still having access to the data for compliance reasons. The feature uses existing components within data collection rules to configure the data flow and transformation logic. Users can modify existing data collection rules or create new ones to leverage this functionality. It is important to note that certain tables are excluded from this feature. Overall, this feature expands the use cases for Azure Monitor and provides improved cost management and query performance.
#AzureMonitorFeatures #DataIngestion #softcorpremium
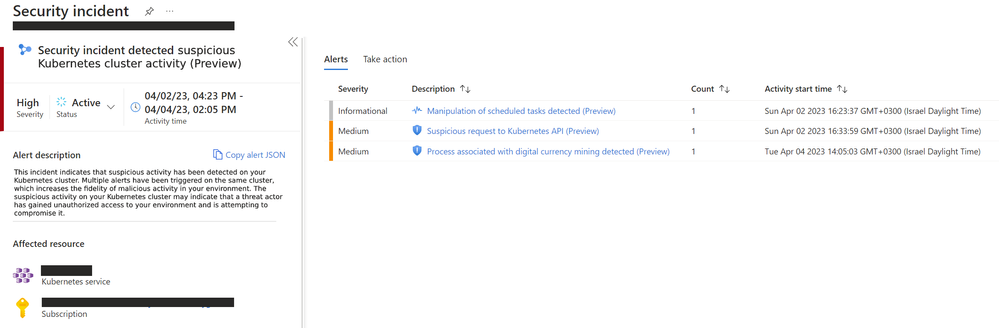
Correlating alerts in Microsoft Defender for Cloud - Microsoft Community Hub
Microsoft Defender for Cloud generates alerts to notify users of potential security threats and anomalous activities in their cloud environment. These alerts provide important information for SecOps teams to effectively identify and respond to potential malicious activity. However, too many alerts can overwhelm security teams and lead to alert fatigue, potentially leaving critical cyber threats unaddressed. To address this, Microsoft Defender for Cloud correlates alerts into incidents, allowing security teams to prioritize and manage their response efforts more efficiently. This correlation enables teams to understand the different phases of an attack and detect suspicious activities more effectively. The blog also provides a case study on incident templatization with a focus on crypto mining as an example.
#MicrosoftDefenderforCloud #SecurityAlerts #IncidentManagement #softcorpremium
Protect against PaperCut vulnerability with Azure Firewall Premium - Microsoft Community Hub
On May 16, 2023, software company PaperCut released an update addressing a vulnerability (CVE-2023-27350) in their print management software. This vulnerability allowed remote attackers to bypass authentication and execute arbitrary code. A patch was made available, but attackers took advantage of the vulnerability before all users could update. The FBI discovered that the Bl00dy Ransomware Gang targeted educational facilities with vulnerable PaperCut servers. To protect against this vulnerability and similar exploits, it is recommended to promptly apply the patch and consider using Azure Firewall Premium for enhanced protection.
#vulnerabilitymanagement #cybersecurity #softwareupdate #softcorpremium
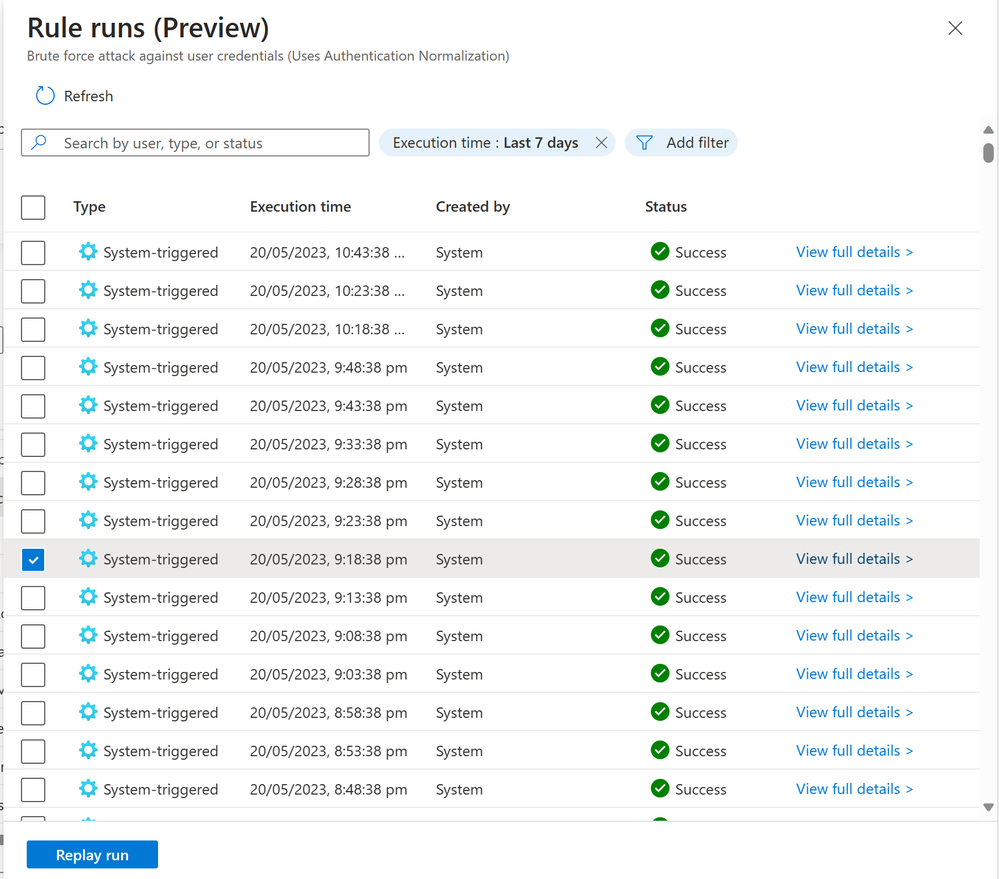
What’s new: Monitor and optimize the execution of your scheduled analytics rules - Microsoft Community Hub
Microsoft Sentinel has introduced new capabilities to help organizations monitor the health and integrity of their analytics rules. This includes insights into rule execution success or failure, as well as the ability to re-run scheduled rules on-demand for validation and troubleshooting. The Analytics rule Insights panel provides further information on rule performance, and the ability to manually re-run rules allows for testing and refining rule effectiveness. These capabilities are beneficial for efficient security operations, incident response, and compliance monitoring.
#MicrosoftSentinel #AnalyticsRules #SecurityOperations #softcorpremium
Automatically disrupt adversary-in-the-middle attacks with XDR
Microsoft has expanded the automatic attack disruption capability in Microsoft 365 Defender to include adversary-in-the-middle (AiTM) attacks. AiTM attacks are a growing threat and can pose a major risk to organizations. The automatic attack disruption feature identifies and contains these attacks by disabling compromised user accounts and revoking stolen session cookies. SOC teams have full control and can configure and revert actions from the Microsoft 365 Defender portal. The feature is available in Microsoft's XDR and does not require pre-configuration by the SOC team.
#Microsoft365Defender #AutomaticAttackDisruption #SOCteams #softcorpremium
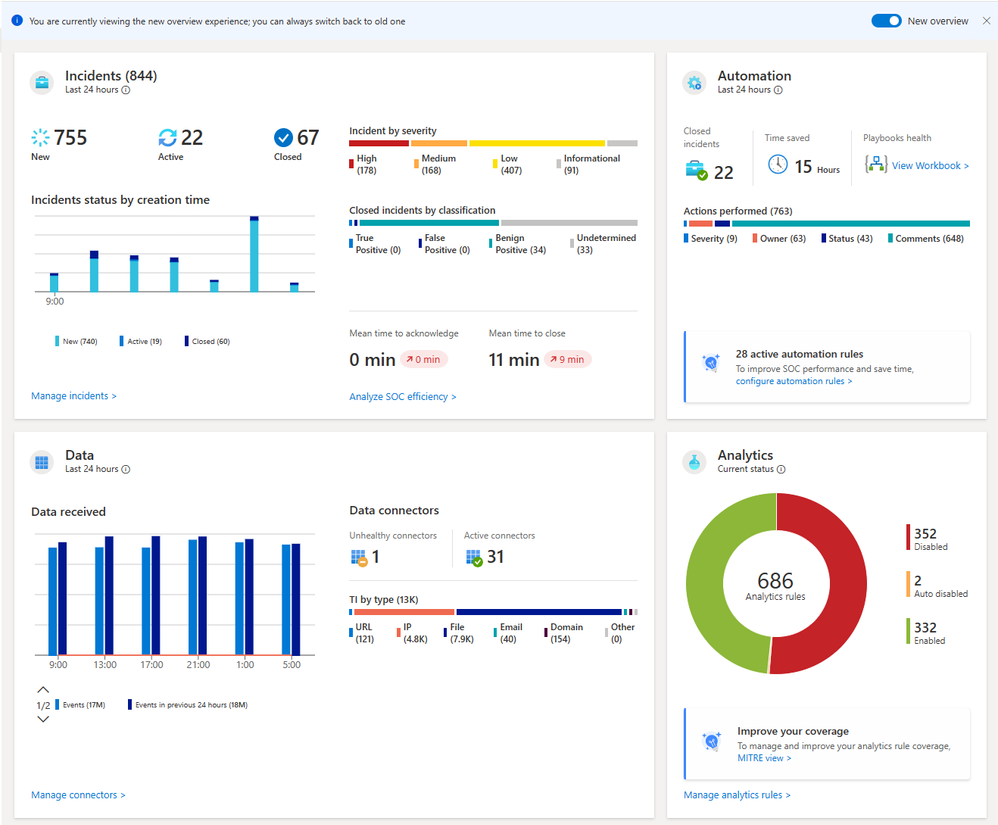
Deep dive into Microsoft Sentinel’s new Overview dashboard - Microsoft Community Hub
Microsoft Sentinel's Overview dashboard provides operational and health insights for each function domain of Microsoft Sentinel, including incidents, automation, threat intelligence, and analytics. The dashboard includes widgets that display pre-calculated data and refresh times. The code snippets provided perform various calculations and summarizations on security incidents and automation activity. The code also analyzes changes in incident severity, status, comments, and owner. The data widget provides visibility into data ingestion volumes and connector health, while the threat intelligence widget organizes records by indicators of compromise. The analytics widget tracks the status of analytics rules. The article suggests using the API to adapt and reuse queries, create personalized dashboards, and gain insights across multiple workspaces. Custom analytics rules can also be used for additional insights.
#MicrosoftSentinel #dashboardinsights #APIadaptation #softcorpremium
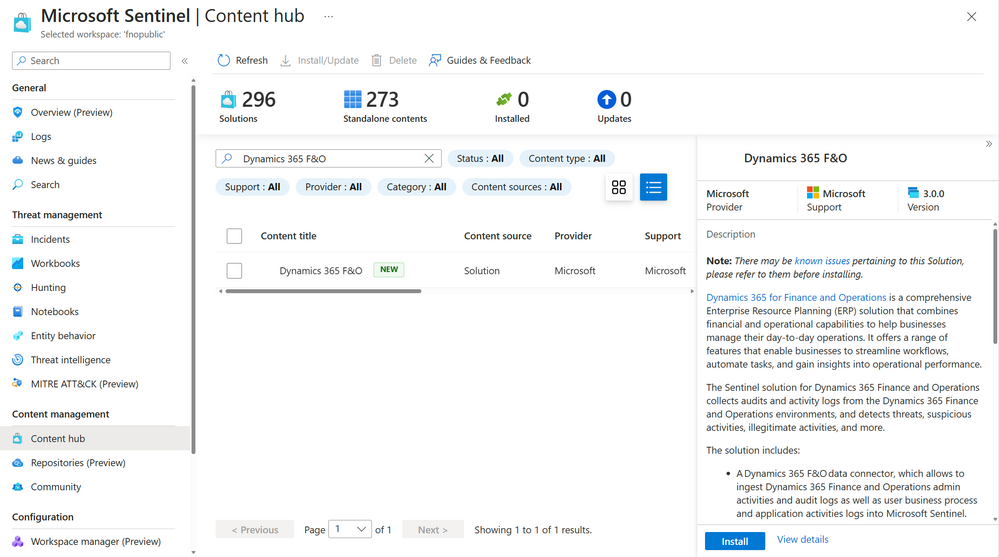
What's new: Microsoft Sentinel Solution for Dynamics 365 Finance and Operations
Microsoft has announced a new Sentinel Solution for Dynamics 365 Finance and Operations, which focuses on monitoring, detecting threats, and responding to incidents in customer's ERP systems. The solution collects audits and activity logs, detects suspicious activities, and protects sensitive business data. Dynamics 365 Finance and Operations is a major target for attackers, and the new solution aims to provide visibility, detect threats, and respond to incidents. The solution includes built-in analytics rules and is currently in preview, with pricing information to be available before general availability.
#MicrosoftSentinel #Dynamics365Security #ERPThreatDetection #softcorpremium
What's new: Sentinel Solution for Dynamics 365 Finance and Operations
Microsoft has announced a new Sentinel Solution for Dynamics 365 Finance and Operations, which is focused on monitoring and detecting threats in ERP systems. The solution collects audits and activity logs, detects threats and suspicious activities, and offers protection for sensitive business data. Dynamics 365 Finance and Operations is a major target for attackers, and breaches can result in exposed customer data and disruption of key business processes. The solution provides visibility to user activities, detects suspicious or illegitimate activities, and allows for investigation and response to incidents. It includes built-in analytics rules to address security risks. The solution is currently in public preview with pricing information to be available before general availability.
#MicrosoftSentinel #Dynamics365Security #ERPThreatDetection #softcorpremium
Logz.io Cloud SIEM Available on AWS AppFabric at Launch | Logz.io
Logz.io's Cloud SIEM is now available as part of the launch of AWS AppFabric, allowing customers to seamlessly use the cloud-based, agile SIEM alongside other critical SaaS applications. This integration simplifies the process of connecting and managing multiple SaaS applications, boosts employee productivity, and enhances security posture. Logz.io's fully-managed solution applies SIEM best practices, utilizes analytics and machine learning, and improves security posture while enhancing application performance across distributed environments. The solution is built on open-source technology with deep integrations into AWS solutions, including Amazon OpenSearch. Customers can start using Logz.io Cloud SIEM with AWS AppFabric immediately.
#CloudSIEM #AWSAppFabric #SecurityPosture #softcorpremium
Windows Autopatch: one year of managed updates and new capabilities
Windows Autopatch is a service offered by Microsoft that helps manage updates and security for enterprise endpoints. It has received positive feedback from customers for saving time and effort in updating Windows and Microsoft applications. New features, such as customizable configurations and policy naming, will be available starting July 25, 2023. The service also offers controls for feature updates, Microsoft 365 apps, drivers, and firmware. Improved reporting and issue resolution capabilities are included in the update. The development and enhancement of Windows Autopatch will continue, and feedback is encouraged from users.
#WindowsAutopatch #EnterpriseUpdates #MicrosoftSecurity #softcorpremium
May 2023 cumulative update explained - Microsoft Community Hub
The author wrote an article to explain how to mitigate the Secure Boot UEFI bootkit using the May 2023 cumulative update. They provide step-by-step instructions for installing the update and applying the UEFI patch. They also mention that applying the UEFI patch will prevent unpatched operating systems from booting. They recommend patching all running operating systems with the update first, then patching Windows PE and Windows images used for fresh installations. Finally, they suggest applying the UEFI patch on all running systems. The article includes links to the official KB article for more detailed instructions and provides information on downloading the cumulative update and updating custom images using DISM.
#SecureBootUEFI #CumulativeUpdate #UEFIPatch #softcorpremium
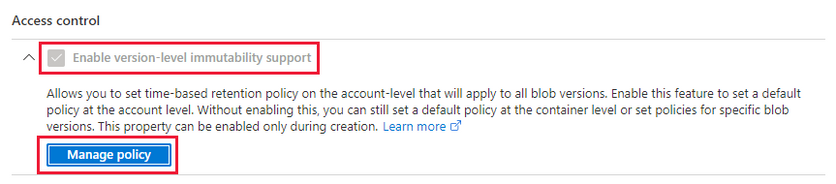
Immutable Blobs Inside Azure Storage (WORM) - Microsoft Community Hub
The passage discusses the concept of Write Once, Read Many (WORM) requirements in various industries and how Azure Blobs' immutable storage feature can be a solution. It explains the different types of WORMs supported and how they can be applied at the account or container level. The passage also provides instructions on enabling and configuring immutable storage in Azure. Additionally, it mentions the limitations and behavior of blobs when using immutable storage. The passage also introduces immutable vaults for Azure Backup, which offer protection against threats like ransomware attacks.
#WORMstorage #AzureImmutableVaults #DataProtection #softcorpremium
Microsoft Entra new feature and change announcements - Microsoft Community Hub
Microsoft has introduced new security tools and features for its Entra product family to improve organizations' security and address the increasing sophistication of cyber attacks. The updates include new features and updates to existing ones, making it easier for customers to manage lifecycle changes. Microsoft is also introducing new authentication methods, such as voice OTP, and making improvements to the Phone OTP authentication method. There will be changes to the sign-in experience for cross-tenant collaboration authentication requests. Microsoft is committed to working with customers during the migration period for the deprecation of legacy PowerShell modules and the retirement of Azure AD Graph. Additionally, Microsoft Entra has new features for permissions management and workload identities. Microsoft recently hosted a digital event showcasing their innovations and promoting their Entra ID Governance.
#MicrosoftEntraSecurity #CybersecurityUpdates #EntraIDGovernance #softcorpremium
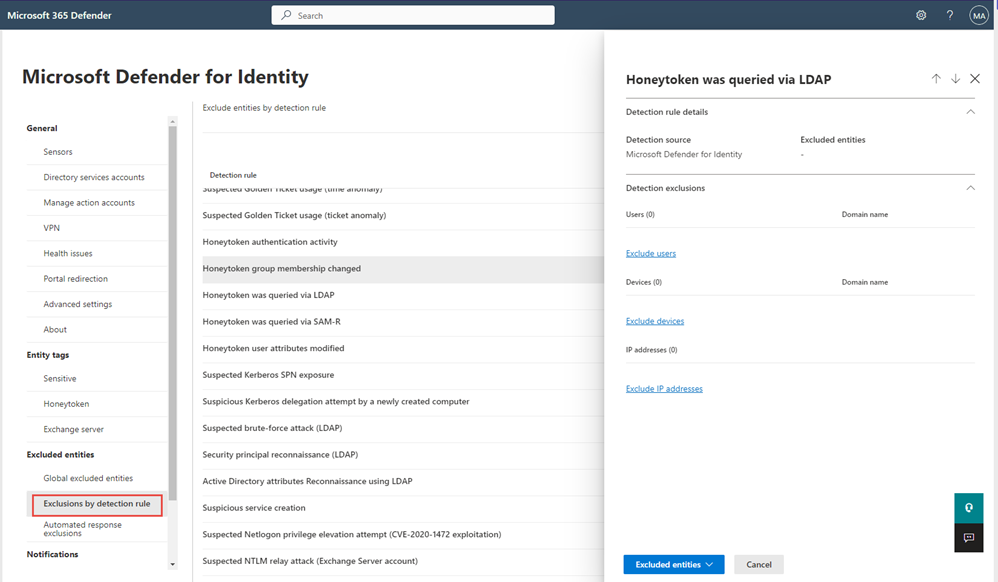
Deceptive defense: best practices for identity based honeytokens in Microsoft Defender for Identity - Microsoft Community Hub
Honeytokens are fake entities used to detect and divert attackers in digital environments. They can be placed within databases, file shares, key vaults, or identity systems. By using existing user accounts or service accounts, honeytokens can trick attackers and alert security teams to potential threats. Best practices include using enticing account names, placing honeytokens in discoverable locations like file shares or PowerShell scripts, and monitoring for activity using tools like Microsoft Sentinel. Honeytokens can also be used to monitor ongoing attacks and phishing attempts. Microsoft Defender for Identity offers a honeytoken tagging feature to enhance security.
#honeytokens #cybersecurity #digitaldefense #softcorpremium
Microsoft Entra new feature and change announcements - Microsoft Community Hub
Microsoft has introduced a range of new security tools and features for the Entra product family, including Azure AD Certificate-Based Authentication, Enterprise SSO for Apple Devices, SAML Request Signature Verification, and more. They have also made improvements to existing features such as managing passwords and introducing voice OTP for authentication. Microsoft is also retiring Azure AD Graph and deprecating certain PowerShell modules. Additionally, there are updates to B2B sign-in experience and Microsoft Entra Identity Governance. Microsoft is hosting a digital event to showcase these innovations.
#MicrosoftSecurityUpdates #EntraProductEnhancements #DigitalEventShowcase #softcorpremium
Monthly news - July 2023 - Microsoft Community Hub
Microsoft Defender for Cloud has released various product updates and new assets in June 2023. These updates include improvements to the onboarding experience, the ability to use Terraform for deployment, private endpoint support for malware scanning, a new Azure Workbook for Defender CSPM Visualization, and the availability of direct onboarding to Defender for Servers without Azure Arc. Additionally, there is a new Defender for API Security dashboard and the general availability of express configuration for vulnerability assessment in Defender for SQL. The option of streaming data from Microsoft Defender for Cloud to other systems is also available. Lastly, Dish TV, India's leading DTH company, uses Microsoft security solutions, including Defender for Cloud, to secure their environment.
#MicrosoftDefender #CloudSecurity #ProductUpdates #softcorpremium
Leveraging the convergence of Microsoft Defender for Identity in Microsoft 365 Defender Portal - Microsoft Community Hub
Microsoft Defender for Identity has been integrated into Microsoft 365 Defender, the extended detection and response (XDR) platform. This convergence allows for better pairing of advanced identity threat detection and investigation capabilities with other security workloads. The new platform provides a prioritized view of identity alerts and automatically correlates them with telemetry from across Microsoft 365 security. Users can create complex exclusion rules, investigate alerts, and take remediation actions. The platform also offers tools and insights to investigate user behavior, detect anomalies, and respond to identity-related security incidents. The unified Identity Timeline consolidates user activities across various identity workloads. Users can pivot to the Advanced hunting view for querying additional sources of information on advanced threats. Custom detection rules, environment settings, and security posture assessments are also available. Microsoft continually updates recommendations and releases new reports and assessments.
#Microsoft365Defender #IdentitySecurity #AdvancedThreatDetection #softcorpremium
Detect threats on your Power Platform based no-code/low-code applications with Microsoft Sentinel
Microsoft has announced the Microsoft Sentinel Solution for Microsoft Power Platform, which helps organizations detect and respond to security threats introduced by citizen-developed Power Apps. These low-code and no-code applications can pose security risks if not properly controlled and monitored. The solution allows customers to monitor and detect suspicious or malicious activities in their Power Platform environments, such as unauthorized app execution, data destruction, mass deletion of apps, and phishing attacks. It collects activity logs and inventory data from Power Apps, Power Automate, Power Platform Connectors, and Power Platform DLP, and analyzes them to detect threats. Customers can investigate and respond to threats using automation and response capabilities. The solution includes data connectors and analytics rules to detect various threats, and it is currently available for limited public preview.
#MicrosoftSentinelSolution #PowerPlatformSecurity #CitizenDevelopers #softcorpremium
Public preview: Azure Virtual Network encryption | Azure updates | Microsoft Azure
Microsoft Azure has introduced Virtual Network encryption, allowing customers to encrypt traffic between Virtual Machines and Virtual Machines Scale Sets within the same virtual network, as well as between regionally and globally peered virtual networks. This feature enhances existing encryption capabilities in Azure. The public preview of Azure Virtual Network encryption is currently available in select regions.
#AzureEncryption #VirtualNetworkSecurity #CloudSecurity #softcorpremium
Consensys survey shows growing support for web3, cryptocurrencies - Back End News
A recent survey conducted by Consensys reveals that 96% of Filipinos are familiar with cryptocurrencies, making it one of the highest markets worldwide. However, only 52% of Filipinos trust current internet services, with data privacy being a significant concern for 77% of users. The survey also found that 84% of respondents want more control over their internet identities. Filipinos show familiarity with the concepts of the Metaverse and NFTs. The survey emphasizes the need for broader education on web3 and crypto, as well as the importance of addressing data privacy concerns and promoting user empowerment.
#CryptoPhilippines #DataPrivacyConcerns #Web3Education #softcorpremium
Public preview: Sensitive Data Protection for Application Gateway Web Application Firewall logs | Azure updates | Microsoft Azure
Azure's regional Web Application Firewall (WAF) on Application Gateway now offers sensitive data protection through log scrubbing. This feature allows users to create rules that replace sensitive customer data with \"******\" to prevent it from being stored in plain text logs. The log scrubbing rules can be created using various variables such as request headers, cookies, arguments, JSON, and IP addresses.
#AzureWAF #logscrubbing #softcorpremium
AWS CloudFormation launches Guard 3.0 with support for stateful rules
AWS CloudFormation has released Guard 3.0, which includes support for stateful rules. Guard is an open-source domain-specific language and command line interface that helps enterprises ensure their cloud infrastructure meets company policy guidelines. The new version allows for complex rules and offers a new deployment method. It also includes built-in functions for stateful rules, an alternative deployment method using AWS SAM CLI, and auto-completions for commands in various shells. AWS CloudFormation encourages feedback and contributions to the project.
#AWSGuard #CloudInfrastructure #EnterpriseCloud #softcorpremium