💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
Black Hat USA 2023 Conference Theatre Sessions Presented by Microsoft Security - Microsoft Community Hub
Microsoft Security will be present at Black Hat USA 2023, offering sessions, product demos, and meetings at their booth. They will also have a mini-theatre in their booth, where attendees can join 20-minute presentations and ask questions. Microsoft Intelligent Security Association (MISA) members will discuss their partnership with Microsoft. Other activities include AI and threat protection sessions, diversity and mental health sessions, and security community celebrations. Microsoft Security will also be announcing new product innovations on August 9. Visit their booth for more information and to schedule a chat.
#MicrosoftSecurity #BlackHatUSA2023 #MISA #softcorpremium
Integrate Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare has announced the integration of its Zero Trust platform with Datadog Cloud SIEM. This integration allows customers to aggregate and analyze security and operational logs in real time, providing threat detection, investigation, and automated response capabilities. The integration offers out-of-the-box dashboards and detection rules, allowing security teams to quickly identify and respond to anomalous activity within the Cloudflare Zero Trust ecosystem. Additionally, it provides security detections for CASB findings and impossible travel scenarios. Customers can set up Logpush jobs to send Cloudflare Zero Trust logs to Datadog, install the Cloudflare Tile within the Datadog Integration catalog, and analyze and correlate the logs using Datadog Cloud SIEM's out-of-the-box content. This integration aims to enhance security monitoring and strengthen the overall security posture of organizations.
#CloudflareZeroTrust #DatadogSIEM #securityintegration #softcorpremium
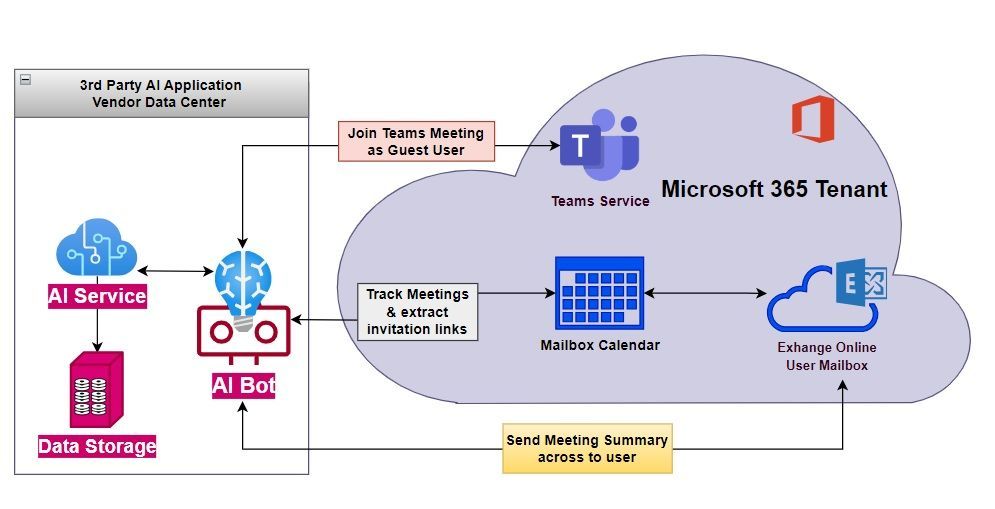
Emergence of AI Personal Assistants for Teams Meetings and Data Privacy and Security Considerations
The emergence of AI personal assistants for Teams Meetings is helping to reduce manual efforts and increase overall productivity. These AI assistants can schedule meetings, capture meeting notes, and provide holistic data and minutes for decision making. However, concerns arise regarding data privacy and security, as third-party organizations may have access to sensitive business information. Compliance with data regulations and the use of non-disclosure agreements can help mitigate these risks. Microsoft's Intelligent Recap feature in Teams Meetings provides automatic generation of meeting notes, but organizations should consider implementing stricter information controls and data restrictions to ensure data privacy and security.
#AIassistants #dataprivacy #security #softcorpremium
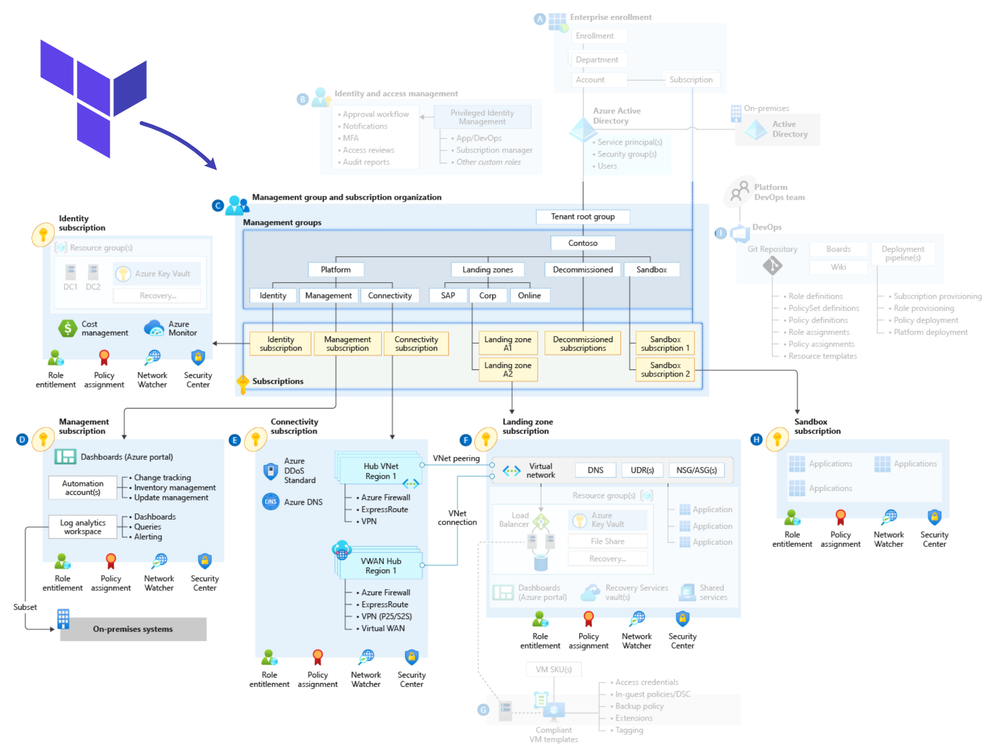
Empowering AI: Building and Deploying Azure AI Landing Zones with Terraform
Microsoft Azure is offering a secure and scalable AI environment through features like Firewall, Virtual Networks, and Private Endpoints. They have also released the Azure Cloud Adoption Framework, a comprehensive guide to successful cloud adoption. By using Terraform and the Azure OpenAI Landing Zone architecture, organizations can create a secure and scalable AI environment. The hub and spoke topology promotes efficient data flow and simplifies network management. Azure has introduced features like Private DNS Zones, Private Links, and Private Endpoints to enhance security and privacy. Azure API Management and Application Gateway optimize performance and secure access to AI services. Users can deploy AI workloads on Azure Open AI and view their network topology. Azure Bastion and private endpoints provide secure access to virtual machines. Azure App Gateway's Public IP ensures secure communication with Azure Open AI and other applications. Azure offers features to enhance data encryption and security, such as SSL/TLS certificates, Private DNS Resolver, Azure Firewall, naming conventions, resource tagging, and logging solutions. Azure Front Door offers web application balancing, SSL offloading, and enhanced security. Developers and IT teams can use Terraform to deploy and manage AI models, creating a secure and scalable AI environment.
#SecureAIEnvironment #AzureCloudAdoption #ScalableAI #softcorpremium
'DarkBERT' GPT-Based Malware Trains Up on the Entire Dark Web
New malware called 'DarkBERT' based on GPT technology has emerged on the dark web, posing significant cybersecurity threats. It has the ability to exploit vulnerabilities in cloud, remote workforce, and IoT. Cybersecurity professionals are monitoring the situation and working on countermeasures. Meanwhile, upcoming events like SecTor and Black Hat USA offer valuable resources for IT security professionals. MicrosoftTech Library is hosting webinars on enterprise cybersecurity automation and OT/IT security best practices. SlashNext warns about the rapid development of malicious AI, while S2W creates a language model called DarkBERT to fight cybercrime. Concerns are raised about the potential consequences of AI-driven cybercrime and the need for stronger defense mechanisms. Organizations are urged to stay updated on the latest cybersecurity threats and vulnerabilities. The importance of DNS attack mitigation, identity management in cloud environments, and threat intelligence is emphasized. The rise of ransomware, zero-day bugs, and AI-enabled malware is a growing concern. Users can control their cookie preferences on websites for enhanced web experience and privacy.
#cybersecuritythreats #AIenabledmalware #ITsecuritybestpractices #softcorpremium
AWS IoT Core announces new certificate signing & key generation algorithms
AWS IoT Core has announced the support for new algorithms for certificate signing and key generation, expanding the security options for IoT devices connected to AWS. The new algorithms include RSASSA-PSS signing and P-521 elliptic curve key algorithms, providing developers with more flexibility to strengthen the security of their IoT solutions. These additions are offered at no additional charge and are available in all commercial regions where AWS IoT Core is available. For more information, refer to the technical documentation.
#AWSIoTCore #IoTsecurity #certificategeneration #softcorpremium
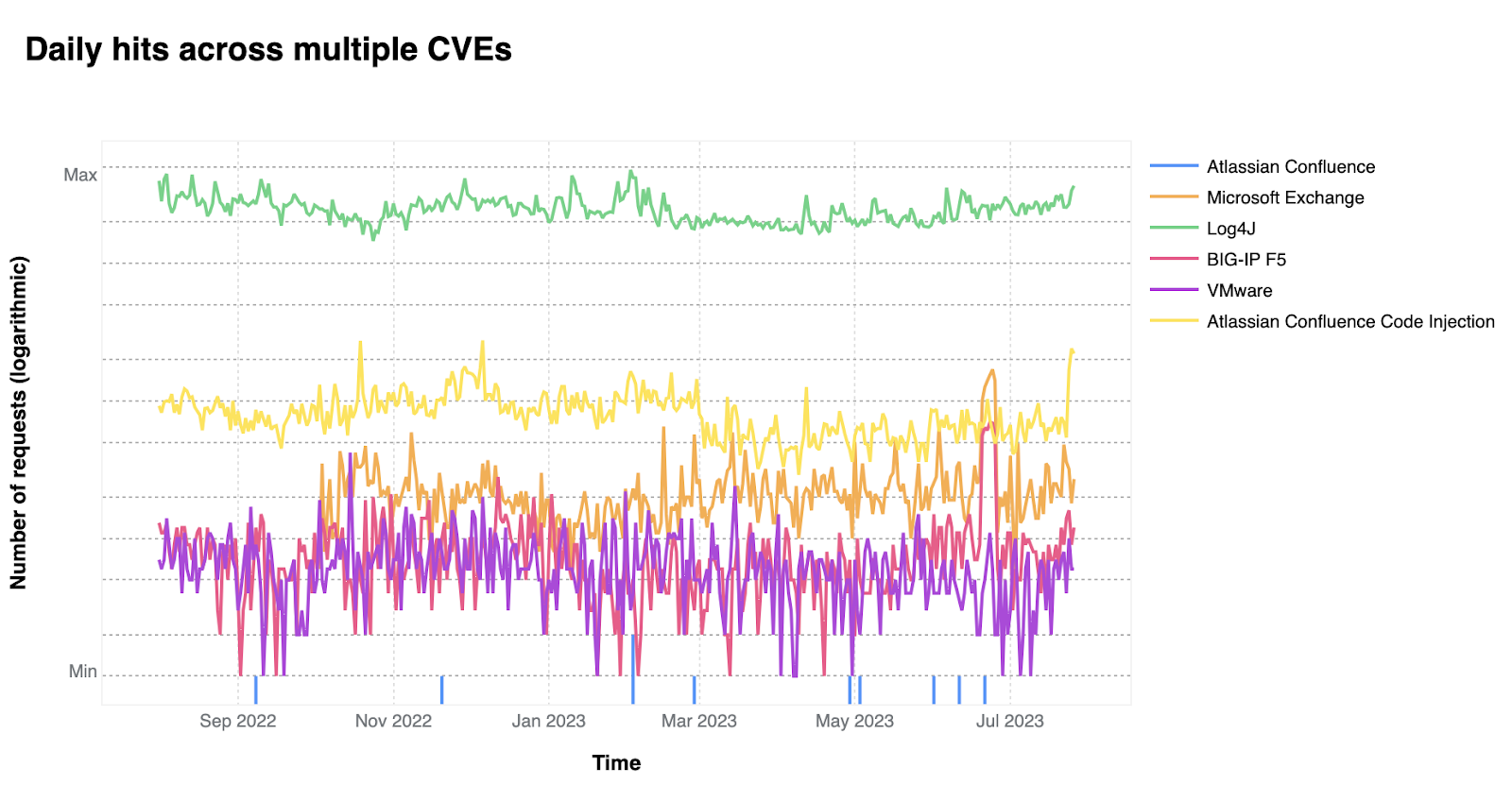
Unmasking the top exploited vulnerabilities of 2022
The Cybersecurity and Infrastructure Security Agency (CISA) has released a report highlighting the most exploited vulnerabilities of 2022. Cloudflare, as a reverse proxy to a large portion of the Internet, has analyzed the data and found that the Log4J and Atlassian Confluence Code Injection vulnerabilities were responsible for the majority of attack traffic. Log4J, in particular, has been extensively exploited and continues to be a major threat. The Atlassian Confluence vulnerability posed a significant risk to systems and organizations. Other vulnerabilities mentioned in the report include Microsoft Exchange SSRF and RCE vulnerabilities, a BIG-IP F5 exploit, and VMware vulnerabilities. Cloudflare has provided emergency releases and updated rules to protect its customers from these vulnerabilities. They emphasize the importance of regular software patching and offer their WAF and AI-powered detection features to enhance security. Overall, organizations should prioritize patching based on the list of vulnerabilities provided.
#Cybersecurity #Vulnerabilities #SoftwarePatching #softcorpremium
Microsoft Edge for Business FAQ - Microsoft Community Hub
Microsoft has announced the upcoming release of Microsoft Edge for Business, a dedicated work browsing experience built to maximize productivity and security. It will be automatically enabled for all customers signing in with Microsoft Entra ID, with the transition scheduled for the week of August 17, 2023. IT administrators will maintain full control over policy and feature management, while users will have the option to separate their work and personal browsing and take advantage of the full feature set of Edge for personal use. The personal browser window will be lightly managed, with IT controlling security, compliance, and update policies. Microsoft Edge for Business aims to provide a streamlined and secure browsing experience for both IT and end users.
#MicrosoftEdgeforBusiness #ProductivityandSecurity #WorkandPersonalBrowsing #softcorpremium
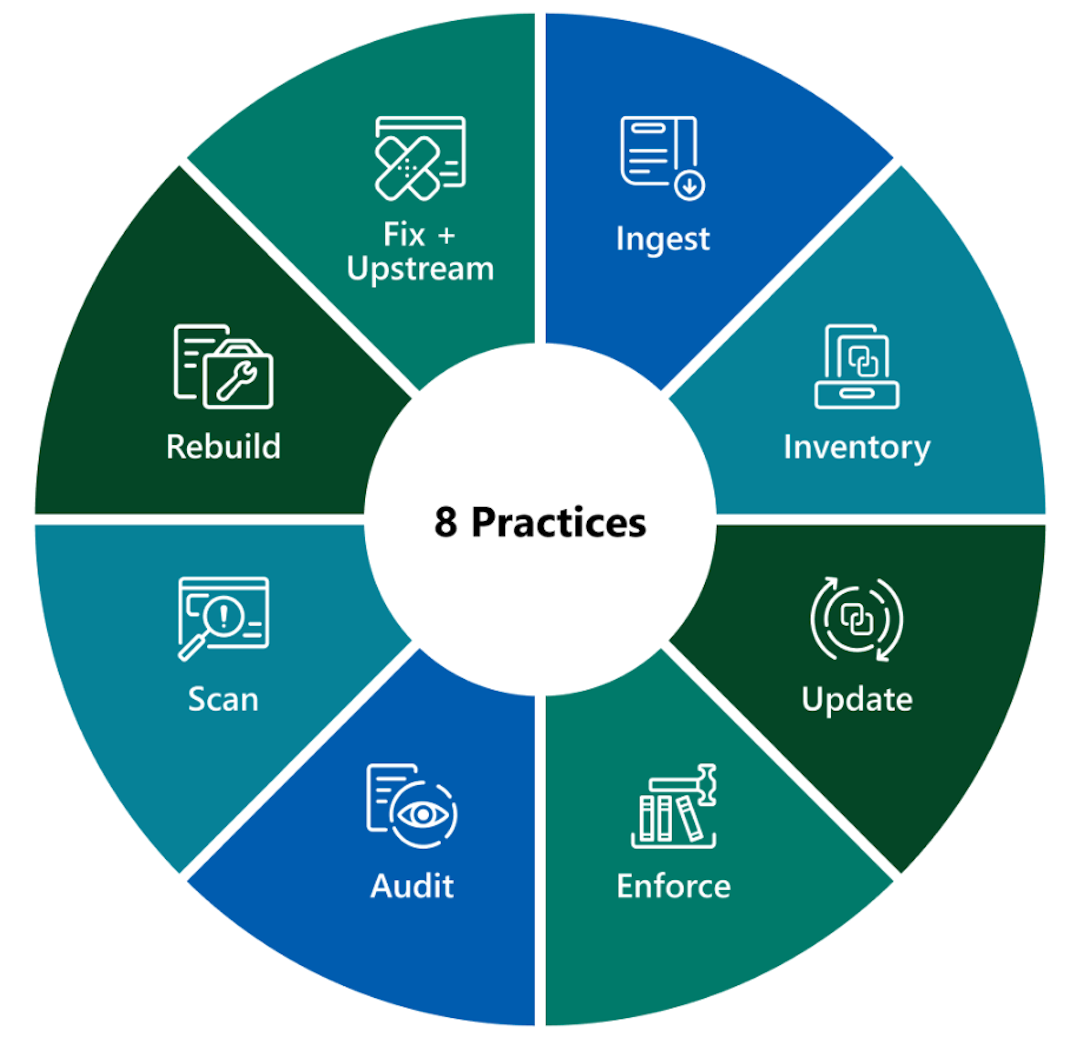
Supply chain security framework: S2C2F | Cloud Native Computing Foundation
The Secure Supply Chain Consumption Framework (S2C2F) is an open-source initiative developed by the Open Source Security Foundation in collaboration with Microsoft. It aims to provide organizations with a set of requirements and tools to securely consume and manage open source dependencies. The framework focuses on control of all artifact inputs, continuous process improvement, and scale. It offers eight best practices that can be implemented gradually to enhance supply chain security. The framework emphasizes the importance of acquiring ownership of input artifacts, maintaining a proper inventory, continuous vulnerability assessments, and updating artifacts. The S2C2F framework is expected to play a crucial role in enhancing the security of digital supply chains and mitigating the increasing number of attacks. Organizations are encouraged to adopt this framework for the resilience of their supply chains.
#supplychainsecurity #opensource #softcorpremium
Programmatically Create SAS tokens in .Net - Microsoft Community Hub
In this blog post, the author discusses the importance of data security and controlled access in today's digital landscape. They introduce Azure Blob Storage as a popular cloud storage solution and highlight the need for generating Shared Access Signature (SAS) tokens programmatically in .NET to enhance the security of Azure Blob Storage. The author mentions that while SAS tokens provide temporary, controlled access to specific resources, Role-Based Access Control (RBAC) using Azure Active Directory or other identity providers should be the primary choice for access control and security enforcement. They provide several use cases for SAS tokens and explain what a SAS token is and how it works. The author also discusses different SAS signature options and explains how to create SAS tokens programmatically in .NET using the Azure.Storage.Blobs library. They provide code examples and instructions for testing the newly created SAS tokens. The author concludes by emphasizing the importance of securing Azure Blob Storage and teases a future blog post about user-delegated keys for generating SAS tokens.
#DataSecurity #AzureBlobStorage #SharedAccessSignature #softcorpremium
Cloud Security Market Worth $62.9B by 2028
The cloud security market is expected to reach $62.9 billion by 2028 due to the increasing adoption of cloud services and the need for robust security measures. Organizations are investing in advanced threat detection, endpoint authentication, and vulnerability management solutions to protect sensitive data. Compliance and privacy regulations are also driving the demand for cloud security solutions. The IT Security Conference and Black Hat USA are upcoming events that offer valuable insights into cybersecurity. Webinars on OT and IT security best practices and tools are also available. Various resources can be accessed on Dark Reading Library and Tech Library. Cloud security providers are customizing their solutions to meet the specific needs of the retail and eCommerce industry. The Asia Pacific region is experiencing rapid growth in cloud security adoption. Key players in the market include IBM, Broadcom, Check Point, Google, and Zscaler. Recent developments include AWS's Amazon Security Lake, Check Point's expanded Harmony Endpoint protection solutions, IBM's IBM Security QRadar Suite, and Google's acquisition of Mandiant. Cloud security solutions offer flexibility, scalability, and speed in deploying security measures. They utilize AI and machine learning techniques to quickly identify and address new threats. Concerns are rising over ransomware, zero-day bugs, and AI-enabled malware. It is important to stay informed about the latest cybersecurity threats and trends.
#CloudSecurity #CybersecurityTrends #ITSecurityConference #softcorpremium
Nile Raises $175M Series C Funding to Redefine Enterprise Networks
Enterprise networking company Nile has secured $175 million in Series C funding to redefine enterprise networks and improve their EdgeDR technology. The funding will be used to enhance security monitoring, threat intelligence, and vulnerability management. Nile plans to develop identity and access management solutions and expand their physical security and IoT capabilities. Various tech events and webinars are scheduled, covering topics such as best practices for OT and IT security, the dark side of AI in cybersecurity, and emerging trends in IT security. Nile has been adopted by Stanford University to address Wi-Fi challenges on campus, and they offer a network-as-a-service (NaaS) solution that prioritizes security and automation. Concerns over cybersecurity threats like AI-enabled malware and ransomware are growing, highlighting the need for robust cybersecurity measures. Nile's funding and innovations position them as a leader in next-generation enterprise networks.
#EnterpriseNetworking #Cybersecurity #NextGenerationNetworks #softcorpremium
Center for Cyber Safety and Education Awards $174K in Cybersecurity Scholarships
The Center for Cyber Safety and Education is awarding $174,000 in cybersecurity scholarships to support students pursuing careers in the field. This comes at a time when cybersecurity threats are increasing, highlighting the need for skilled professionals. In other news, upcoming events like SecTor and Black Hat USA will cover topics such as OT and IT security, AI threats, and more. Dark Reading offers resources like reports, white papers, and slideshows on various tech security topics. (ISC)² and the Center for Cyber Safety and Education are offering scholarships, certifications, and guidance to students. Stay updated on the latest cybersecurity news and subscribe to newsletters for insights and trends. Concerns are rising over third-party vulnerabilities and the use of cookies, emphasizing the importance of privacy and informed choices.
#cybersecurity #scholarships #privacy #softcorpremium
AWS Security Hero ~ How and Why. After years of speaking about AWS… | by Teri Radichel | Cloud Security | Aug, 2023 | Medium
AWS has created a new hero category, and Teri Radichel, an AWS Hero since 2016, is excited about it. AWS heroes are recognized for their contributions to the AWS community, such as writing or speaking about AWS, contributing code and tools, and running AWS meetups. Teri Radichel has been involved in the AWS community for years, running a meetup and blogging about AWS. She was initially skeptical when she received emails about being selected as an AWS Hero, but Jeff Bar confirmed it on Twitter. Teri prefers to be recognized for her work rather than actively seeking recognition. She shares her experiences and knowledge in this post and provides a new cybersecurity tip.
#AWSHero #AWSCommunity #CybersecurityTip #softcorpremium
Wiz helps organizations innovate with AI securely and responsibly, launching support for Google Cloud Vertex AI | Wiz Blog
Wiz, a leading AI security platform, has announced its support for Google Cloud Vertex AI, allowing organizations to innovate securely. Users have praised Wiz for its value, effectiveness, and superiority over competitors. The platform offers improved visibility into cloud security, holistic governance, and easy setup. With constant updates and integrations, Wiz is becoming an essential tool for monitoring and improving cloud security. It has received high praise from users, with many considering it a game changer and the future of cloud security tools. Wiz is described as intuitive, user-friendly, and powerful, offering comprehensive features for vulnerability assessment and risk management. Overall, Wiz is hailed as a top-notch tool and one of the best in the industry.
#WizSecurity #CloudSecurityTools #AIsecurity #softcorpremium
Mission Secure, Idaho National Laboratory Announce Partnership to Protect Critical Infrastructure
Mission Secure has announced a partnership with Idaho National Laboratory to protect critical infrastructure against cyber threats. The partnership aims to expand the adoption of the Consequence-Driven, Cyber-Informed Engineering (CCE) methodology, developed by Idaho National Laboratory, which helps organizations reduce the risk of potentially catastrophic cyber attacks. Through this partnership, Mission Secure will apply the CCE methodology to help customers identify critical cyber risks and implement engineering changes and cybersecurity controls. This collaboration will enhance Mission Secure's ability to provide effective cybersecurity solutions for operational technology and industrial control systems.
#CybersecuritySolutions #CriticalInfrastructureProtection #CCEmethodology #softcorpremium
Managing AWS Account Root MFA Using CyberArk Privileged Access Manager | AWS Partner Network (APN) Blog
Amazon Web Services (AWS) has partnered with CyberArk to enhance the security of AWS account root users. By using CyberArk's Privileged Access Manager (PAM), users can securely manage the AWS account root and authenticate its use with multi-factor authentication (MFA). This integration improves security posture, increases control and visibility of root account access, and facilitates collaboration while enforcing personal-level access control and audit. The article provides a step-by-step guide on configuring CyberArk PAM to manage AWS root accounts with MFA. CyberArk is a leader in identity security and offers comprehensive security solutions for privileged access management. This integration is recommended as a security best practice to protect against unauthorized access to AWS systems and data.
#AWSsecurity #privilegedaccessmanagement #CyberArk #softcorpremium
Iran's APT34 Hits UAE With Supply Chain Attack
Iran's APT34, also known as OilRig and MuddyWater, has launched a supply chain attack targeting government clients in the United Arab Emirates (UAE). The attackers used a malicious IT job recruitment form as a lure, creating a fake website to masquerade as an IT company in the UAE. When victims opened the malicious document to apply for the advertised job, info-stealing malware was executed, allowing APT34 to collect sensitive information and access the IT company clients' networks. The group specifically targeted government clients using the victim IT group's email infrastructure for communication and data exfiltration. This attack follows a similar supply chain intrusion in Jordan, indicating a pattern of behavior for APT34.
#cybersecuritythreats #supplychainattacks #APTCyberGroup #softcorpremium
Governing Vertex AI Gen AI / LLM Model Access Via Quotas | by Ferris Argyle | Google Cloud - Community | Aug, 2023 | Medium
Google Cloud has introduced a new feature to govern access to its Vertex AI Gen AI / LLM models through quotas and role-based access control. This allows organizations to limit the usage of these models to a specific group of users who have access to Vertex AI. The implementation of an automated approval and provisioning system for Google Cloud APIs and roles/permissions ensures that only approved users have access to the necessary permissions. By setting quotas to zero, organizations can restrict access to the models and prevent unauthorized usage. However, this workaround requires implementing it against each project and region where the models are available. Out-of-policy usage may occur between scheduled jobs, so it is important to regularly scan for new regions and projects and zero out the quotas. It is also worth noting that the availability of models may change without notice. The implementation of this workaround is primarily for testing purposes and not for governance. The documentation provided by Google Cloud offers further details on how to set quotas and manage access to the Vertex AI Gen AI / LLM models.
#GoogleCloud #VertexAI #ModelGovernance #softcorpremium
Endor Labs Raises $70M to Reform Application Security and Eliminate Developer Productivity Tax
Endor Labs has secured $70 million in funding to revolutionize application security and enhance developer productivity. The company aims to eliminate the burden of time-consuming security measures and reform the way developers approach application security. The upcoming events in the tech industry include SecTor, Canada's IT Security Conference, and Black Hat USA. Webinars on OT and IT security best practices and the threats of AI in cybersecurity are also scheduled. In the world of technology, important areas of concern include authentication, mobile security, privacy vulnerabilities, and advanced threats. Physical security, the Internet of Things (IoT), disaster recovery, and global security are also significant topics. Staying informed and proactive in cybersecurity is crucial.
#ApplicationSecurityRevolution #DeveloperProductivityEnhancement #CybersecurityUpdates #softcorpremium
How to Tell if You’re Inside a Container | by Teri Radichel | Cloud Security | Aug, 2023 | Medium
In a recent article, cybersecurity expert Teri Radichel shared some commands that can help determine if you are running inside a container. This information is useful not only for developers and system administrators but also for penetration testers and attackers. Understanding the environment is crucial for determining the next steps in an attack. Radichel also highlighted the importance of properly configuring containers to prevent exploits. One way to check if you are inside a Docker container on Linux is to look for the presence of a .dockerenv file.
#cybersecurity #containersecurity #docker #softcorpremium
VALIC Retirement Services Company Experiences PBI Data Breach Exposing Approximately 798,000 Social Security Numbers
VALIC Retirement Services Company has experienced a data breach that exposed approximately 798,000 Social Security numbers. The breach was a result of a vulnerability in the vendor used by the company, Pension Benefit Information, LLC. The compromised information includes names, dates of birth, policy or account numbers, and addresses. Affected individuals are at risk of identity theft and other fraudulent activities. Console & Associates, P.C. is investigating claims on behalf of those affected. It is recommended that individuals take steps to protect themselves and consider contacting a data breach attorney for potential compensation.
#DataBreach #IdentityTheft #DataBreachAttorney #softcorpremium
BeyondTrust's Identity Security Insights Provides Unprecedented Visibility into Identity Threats
BeyondTrust has launched Identity Security Insights, a new solution that provides organizations with unparalleled visibility into identity threats and vulnerabilities. This technology aims to enhance security monitoring and authentication processes, particularly in today's remote work environment where insider threats and advanced cyber attacks are on the rise. BeyondTrust's Identity Security Insights is set to revolutionize identity and access management, making it an essential tool for organizations looking to strengthen their security posture. Additionally, upcoming tech events and resources in the tech industry cover a wide range of topics including attacks/breaches, cloud security, remote workforce, and more. Stay informed in the ever-evolving world of cybersecurity.
#IdentitySecurityInsights #Cybersecurity #RemoteWorkforce #softcorpremium
Menlo Security Establishes Browser Security With AI-Powered Phishing and Ransomware Protection
Menlo Security has introduced a new AI-powered solution called EdgeDR to protect browsers from phishing and ransomware attacks. This technology aims to enhance browser security and ensure safe online experiences. Menlo Security's EdgeDR solution provides advanced protection against these threats, leveraging artificial intelligence to detect and prevent attacks in real-time. This innovative approach is expected to significantly improve online security and reduce the likelihood of successful cyber attacks.
In other news, Menlo Security has launched HEAT Shield™ and HEAT Visibility™, a suite of threat prevention capabilities that detect and block highly evasive threats targeting users through web browsers. This technology utilizes AI-powered phishing and ransomware protection to enhance browser security. It is being implemented by top financial institutions, governments, and leading enterprises to combat highly evasive cyber attacks. Menlo Security's browser security solution is built on their cloud-based Isolation Core™, which analyzes billions of web sessions annually.
Menlo Security has also introduced Menlo Security HEAT Shield™, a tool that detects and blocks phishing attacks before they can harm enterprise networks. This technology uses AI and computer vision to analyze web page elements and determine if a link is a phishing site. Menlo Security HEAT Visibility continuously analyzes web traffic and applies AI-powered classifiers to identify highly evasive attacks. This enables security teams to quickly respond to threats and reduce detection time.
JPMorgan Chase Asset and Wealth Management's CIO, Michael Urciouli, has highlighted the increasing threat of highly evasive cyber attacks and the need to reduce the mean time to detect and respond to these threats. Menlo Security's browser security solution, including their HEAT Shield, is being implemented to combat these threats. HEAT Shield addresses the shortcomings of endpoint security and EDR solutions by focusing on web-based attacks. It applies dynamic security policies based on web session events and behavior, effectively preventing attackers from gaining access to the endpoint.
Menlo Security has announced the launch of its new HEAT Attack™ Dashboard and HEAT alerts, enhancing threat intelligence and incident response capabilities. The HEAT Attack™ Dashboard provides detailed threat intelligence that can be integrated into existing security platforms, while the HEAT alerts offer real-time threat visibility to SOC teams. Menlo Security aims to provide a secure browsing experience and believes that legacy security vendors are not adequately protecting users.
The company offers a cloud security platform that eliminates malware threats from the web, documents, and email. Their technology provides comprehensive protection without impacting the end-user experience. Menlo Security is trusted by major global businesses, financial institutions, and governmental organizations.
Overall, Menlo Security's innovative browser security solutions and threat prevention capabilities are expected to greatly enhance online security and protect against evolving cyber threats.
#AIpoweredSecurity #EnhanceBrowserSecurity #ThreatPrevention #softcorpremium
Google, Microsoft Take Refuge in Rust Language's Better Security
Tech giants Google and Microsoft are turning to the Rust programming language to enhance the security of their products and services. Rust's unique features, such as memory safety and thread safety, make it a popular choice for developers aiming to mitigate security vulnerabilities. Both companies are leveraging Rust's capabilities to bolster security. This move highlights the growing importance of prioritizing security in the tech industry. In addition, there are upcoming IT security conferences and webinars discussing best practices and tools for OT and IT security, as well as the dark side of AI in cybersecurity. Valuable resources are available in Dark Reading Library and Tech Library, covering various topics such as attacks and breaches, cloud security, and remote workforce. Stay informed and stay secure!
#RustSecurity #TechIndustrySecurity #ITSecurityConferences #softcorpremium