💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
How to use AWS Verified Access logs to write and troubleshoot access policies | AWS Security Blog
AWS has introduced an improved logging feature for its Verified Access service, providing more extensive user context information from trust providers. This feature simplifies administration and troubleshooting of access policies, aligning with zero-trust principles. Verified Access allows enterprises to securely provide access to corporate applications without using a VPN, using fine-grained access policies written in a policy language developed by AWS. The improved logging functionality eliminates the need to gather information from different sources and provides detailed context to validate and troubleshoot policies. Users can modify the logging configuration of their Verified Access instances and protect sensitive information using Amazon CloudWatch Logs. The blog post provides an example of how the improved logging feature can be used to enhance access policies.
#VerifiedAccess #ZeroTrust #softcorpremium
Monthly news - August 2023 - Microsoft Community Hub
Microsoft Defender for Cloud has released its August 2023 edition, highlighting various product updates and new assets. The latest edition includes the availability of Defender for Cloud as part of agentless scanning in Defender for Servers P2 and Defender CSPM, offering improved detection of unmanaged and insecure secrets on virtual machines. Additionally, the upcoming general availability of Malware Scanning in Defender for Storage has been announced, providing enhanced protection against malicious content in Blob storage accounts. Microsoft Defender for Cloud leverages both agent-based and agentless security, offering a versatile and powerful solution for securing cloud environments. Other updates include the ability to manage automatic updates for Linux agents and the general availability of data-aware security posture. The blog post also covers the deprecation/replacement plan for Log Analytics agent and Azure Monitoring agent, the benefits of agentless security, and the release of support for disabling vulnerability findings for container registry images. Finally, the importance of prioritization in security alerts and incidents, the vulnerabilities of databases in cloud environments, and the risks of identity-based supply chain attacks are discussed. The edition also features a case study on CTT - Correios de Portugal and upcoming webinars on Microsoft Defender for Cloud.
#MicrosoftDefender #CloudSecurity #ProductUpdates #softcorpremium
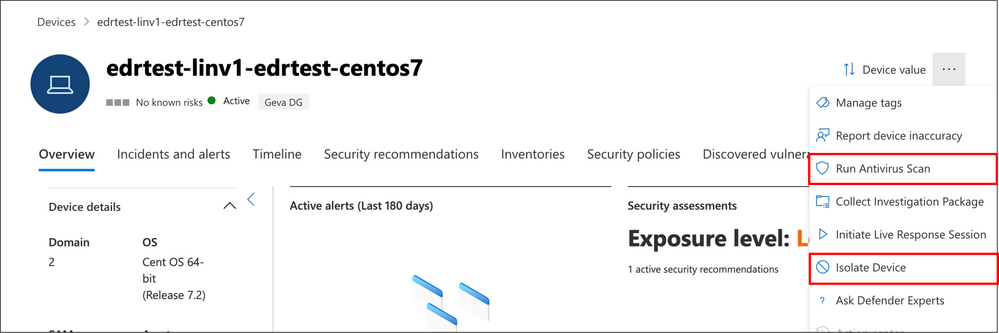
Now in Public Preview: Device isolation and AV scanning for Linux and macOS in Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is expanding its capabilities for macOS and Linux-based devices with the introduction of device isolation and the ability to run antivirus scans. The device isolation feature allows security teams to disconnect compromised devices from the network, preventing attackers from controlling the device and engaging in malicious activities. The antivirus scan feature allows users to remotely initiate scans on devices to identify and remediate malware. These new capabilities aim to provide organizations with more flexibility and control in responding to cyber threats across their multi-platform enterprise. The features are currently in public preview.
#MicrosoftDefenderforEndpoint #cybersecurity #endpointprotection #softcorpremium
ISOG highlights cybersecurity for public sector at 2nd I AM SECURE 2023 forum - Back End News
The Information Security Officers Group (ISOG) recently held its second I AM SECURE 2023 Forum, focusing on fortifying governmental and public sector cyber defenses in the era of digital change. The event brought together local and international decision-makers, C-suite executives, and cybersecurity experts. Keynote speakers discussed data privacy empowerment and ongoing projects to enhance digital transformation in the Philippines. Prominent figures from sponsor companies delivered informative sessions on topics such as cybersecurity architecture and the implications of artificial intelligence in digital transformation. The event also provided networking opportunities and highlighted the importance of staying connected in the industry. ISOG's future endeavors include a conference in October and a donation drive and corporate social responsibility project in December. ISOG aims to enhance the nation's cybersecurity landscape through education, awareness programs, and fostering fellowship among security leaders.
#CybersecurityLeaders #DigitalTransformation PH #softcorpremium
Improve your Kubernetes security posture, with the Pod Security Admission (PSA) | by Mathieu Benoit | Google Cloud - Community | Aug, 2023 | Medium
Google Cloud has introduced a new feature called Pod Security Admission (PSA) in Kubernetes 1.25, aimed at improving the security posture of Kubernetes deployments. PSA replaces the PodSecurityPolicy (PSP) and enforces Pod Security Standards (PSS) on a Pod's security context and related fields. PSS includes three levels of security: privileged, baseline, and restricted. Users can easily enforce PSS on a namespace by adding a label. The feature provides warnings and errors if any Pods violate the enforced security level. This helps organizations enhance the security of their Kubernetes deployments and ensure compliance with security standards.
#GoogleCloud #KubernetesSecurity #PodSecurityAdmission #softcorpremium
DJI Warning: All DJI-related Applications on Google Play Are Unofficial - Pandaily
Renowned drone manufacturer DJI has found imitated versions of its applications on Google Play, with names like \"DJI Fly-Go\" and \"DJI Earning.\" These fraudulent apps were created by unauthorized individuals. DJI has filed a complaint with Google Play and urges users to download apps only from official DJI channels to ensure safety. The counterfeit apps are still available on Google Play, so users should exercise caution.
#DJI #CounterfeitApps #AppSafety #softcorpremium
How to Choose a Managed Detection and Response (MDR) Solution
Tech news reporter: \"Choosing the right Managed Detection and Response (MDR) solution is crucial for enhancing organizational security. The EdgeDR Tech provides guidance on selecting the best option, covering various aspects such as attacks/breaches, cloud security, remote workforce, and more. Stay informed on the latest in the field by following their events and webinars. The SecTor IT Security Conference and webinars on best practices for OT and IT security and the threats of AI in cybersecurity are upcoming events to watch out for. Access resources in the Dark Reading Library and Tech Library to stay updated. BlackBerry highlights the importance of MDR solutions in strengthening security. MDR services offer real-time threat-hunting capabilities and relieve organizations of security operations complexities. MITRE Enginuity ATT&CK Evaluations provide insights into the performance of different endpoint security solutions. Stay informed on cybersecurity threats, vulnerabilities, and emerging trends by subscribing to BlackBerry's newsletter. Webinars and reports are available to guide enterprises in implementing zero-trust measures, securing enterprise data, protecting remote workers, and addressing application security risks. Stay updated on the latest cybersecurity forecasts and insights by attending the upcoming SecTor event. Manage your cookie preferences on websites to balance user experience and privacy preferences.\" #TechNews #Cybersecurity #MDR #SecTor
#TechNews #Cybersecurity #MDR #SecTor #softcorpremium
Kaspersky Password Manager Adds 2FA One-Time Password Storage and New Browser Support
Kaspersky Password Manager has introduced two new features, including two-factor authentication (2FA) for one-time password storage and support for new web browsers. This update aims to enhance the security of the password manager by providing an extra layer of protection through 2FA. Additionally, the support for new web browsers ensures compatibility and ease of use for a wider range of users. In other news, the SecTor IT Security Conference is set to take place from October 23-26, and there are upcoming webinars on OT and IT security best practices and the dark side of AI in cybersecurity. The Dark Reading Library offers valuable resources on various topics related to IT security, and Kaspersky highlights the importance of cybersecurity in the digital age. Furthermore, there are discussions on remote work cybersecurity, vulnerabilities in Intel CPUs, and the impact of climate change on digital security. Organizations are encouraged to prioritize the protection of their databases and stay updated on the latest trends in cybersecurity.
#cybersecurity #passwordmanager #ITsecurity #softcorpremium
AWS IAM Identity Center integration is now generally available for Amazon QuickSight
Amazon QuickSight now has integrated AWS IAM Identity Center, allowing administrators to enable users to log in using their existing credentials. This integration eliminates the need for additional single sign-on configuration and allows administrators to assign roles to users using their identity provider groups. Users can seamlessly sign in to QuickSight with their organization's identity provider and share assets with other users and groups. This feature is available in all regions where QuickSight and IAM Identity Center are available. For more information on how to configure your QuickSight account with IAM Identity Center, visit the provided resources.
#AmazonQuickSight #IAMIdentityCenter #identityprovider #softcorpremium
Microsoft Quarterly Cyber Signals Report: Issue 5, State of Play - Microsoft Community Hub
Microsoft has released its fifth edition of Cyber Signals, a quarterly cyber threat intelligence report. The report discusses the current threat landscape and tactics used by threat actors. This edition focuses on how threat actors exploit high-profile events, such as sports events, which can introduce cyber risks for organizers, facilities, and attendees. The report shares insights on attacks across venues, teams, and infrastructure, and offers guidance on defending against these types of attacks. The global sports market, valued at over $600 billion, is a lucrative target for threat actors.
#CyberSignals #CyberThreatIntelligence #SportsCyberSecurity #softcorpremium
MEF and CyberRatings.org Partner on SASE Certification Program
MEF and CyberRatings.org have partnered to develop a certification program for SASE, a cloud-based networking and security framework. This program aims to establish industry standards and provide organizations with assurance that their SASE solutions meet best practices. Tech enthusiasts can look forward to upcoming cybersecurity events, webinars, and resources, covering topics such as OT and IT security, AI in cybersecurity, and vulnerabilities and threats. Vulnerability management and identity & access management are crucial for protecting against advanced and insider threats. MEF has also announced a partnership with CyberRatings.org for a SASE certification program, aiming to provide confidence in cybersecurity products and services. The Global NaaS Event, organized by MEF, will explore the future of secure NaaS offerings. CyberRatings.org offers independent ratings of security product efficacy and provides resources for staying updated on cybersecurity trends. The report also discusses the importance of threat intelligence, zero-trust principles, and customer identity and access management.
#SASEcertification #cybersecurityevents #NaaSofferings #softcorpremium
Tips & Tricks #5: Unable to login to Azure SQL Managed Instance using AAD Integrated - Microsoft Community Hub
Users are experiencing issues when trying to login to Azure SQL Managed Instance using AAD-Integrated from SQL Server Management Studio. They receive an error message stating \"One or more errors occurred.\" This error may occur if the computer account associated with AAD-Integrated has been removed or disabled. The account is created in the on-premises Active Directory when enabling Azure Active Directory Seamless Single Sign-On feature. To mitigate this issue, users should re-enable the feature or follow the provided steps to enable the computer account. For more information, refer to the provided documentation on Azure Active Directory Seamless Single Sign-On.
#AzureSQL #AADIntegrated #SSO #softcorpremium
Keep Windows Secure with Intune Compliance Policies - Ciraltos
In a recent video, Travis Roberts discusses the importance of maintaining secure devices in Windows using Intune compliance policies. He starts by explaining tenant-wide compliance policies and then moves on to creating device compliance policies, which determine when managed devices are considered secure. Roberts also covers what actions to take if a device falls out of compliance and reviews the clients once the policy is applied. This information is crucial for IT professionals and users who want to ensure the security of their Windows devices.
#WindowsSecurity #DeviceCompliance #IntunePolicies #softcorpremium
Re-release of August 2023 Exchange Server Security Update packages - Microsoft Community Hub
Microsoft has re-released the August 2023 Security Updates (SUs) for Exchange Server to resolve a localization issue that caused setup to stop unexpectedly. Users who were affected by the issue and used a workaround to install the original release will need to take action. The actions needed depend on how the original SU was installed and whether Exchange services were disabled. The re-released SU, known as Aug SUv2, is higher in version than the original release and will be downloaded automatically for users who installed the original SU through Microsoft/Windows Update. Users who installed the original SU manually without any issues can optionally install Aug SUv2 or wait for later SUs. Those who encountered setup failures and disabled Exchange services will need to follow specific steps, including uninstalling the original SU and removing a manually created \"Network Service\" account. The re-release only addresses the localization issue, with no other changes to CVEs or post-installation recommended actions. Uninstalling the original SU will not impact any actions taken to address CVE-2023-21709.
#MicrosoftSecurityUpdates #ExchangeServerUpdates #AugSUv2 #softcorpremium
Network Security Devices Can’t Inspect Encrypted Payloads | by Teri Radichel | Cloud Security | Aug, 2023 | Medium
Network security devices like Suricata and pfSense are facing challenges in inspecting encrypted payloads, particularly when VPN and SSL encrypted traffic is involved. This issue arises because when traffic is encrypted on the client and decrypted past the firewall, security devices like Suricata can only see the encrypted payload and are unable to detect any triggering alerts. The ability to inspect encrypted traffic depends on whether the VPN encryption occurs before or after the point where Suricata inspects the traffic. Some firewalls offer a solution where traffic is sent directly to the firewall, decrypted, inspected, re-encrypted, and then sent to the final destination. However, this concept is similar to a Man-in-the-Middle attack, where attackers trick users into accepting a fake certificate, compromising the encryption of their traffic.
#networksecurity #encryptedtraffic #firewallchallenges #softcorpremium
AI Steals Passwords by Listening to Keystrokes With Scary Accuracy
Researchers at Cornell University have developed an AI model that can steal passwords with a high level of accuracy by listening to keystrokes. The model, trained on typing recordings transmitted over a smartphone, was able to replicate passwords with 95% accuracy. The researchers warn that with the prevalence of microphones and the increase in online services, acoustic side channel attacks pose a significant threat to keyboard security. This development highlights the need for stronger cybersecurity measures to protect against such attacks.
#KeyboardSecurity #AcousticSideChannelAttacks #CybersecurityMeasures #softcorpremium
Threat Intelligence Efforts, Investment Lagging, Says Opswat
Opswat, a security vendor, has released a report stating that 62% of organizations believe their threat intelligence efforts need improvement. The report also reveals that only 22% of respondents have threat intelligence programs in place. While only 11% are currently using artificial intelligence (AI) for threat detection, 56% are optimistic about its future uses. The common challenges organizations face include detecting known and unknown malware, dealing with inadequate solutions, and using compromised tools. Opswat emphasizes the importance of threat intelligence in safeguarding critical assets and staying ahead of malicious actors in the rapidly changing cybersecurity landscape.
#ThreatIntelligence #Cybersecurity #Opswat #softcorpremium
Where Are the Packets Captured by Suricata on pfSense? | by Teri Radichel | Cloud Security | Aug, 2023 | Medium
Tech writer Teri Radichel explains how to access and view network packets captured by Suricata on pfSense, a network security platform. To enable packet capture, users must navigate to the Suricata settings and check the \"Enable Packet Log\" box. The captured packets can be found in the /var/log/suricata directory, which can be accessed through the command prompt. Radichel provides step-by-step instructions on how to access these logs and view the results.
#networksecurity #packetcapture #pfSense #softcorpremium
Clearing an IP Blocked by a Suricata or Snort False Positive in pfSense | by Teri Radichel | Cloud Security | Aug, 2023 | Medium
In this article, the author shares their experience with clearing an IP that was incorrectly blocked by Suricata or Snort in pfSense. They had turned on Suricata in pfSense before going out of town, but when they returned, they couldn't access any websites on the internet. After investigating, they realized that the blocked traffic was related to Suricata. They tried various methods to clear the IP, including removing a rule and changing Suricata to non-blocking, but none of them worked. Finally, they rebooted the firewall and were able to access the internet again. The author explains that the issue was caused by a firewall rule for all Snort or Suricata blocked IP addresses in legacy mode, which added the IP to a table used by the firewall rule.
#pfSense #Suricata #firewall #softcorpremium
OX Security Receives Strategic Investment From IBM Ventures
\"OX Security, a cybersecurity company, receives a strategic investment from IBM Ventures to enhance its capabilities and expand in the industry. The SecTor IT Security Conference offers webinars on best practices and tools for OT and IT security. Focus in cybersecurity is on managing threats, vulnerability, and insider risks. IBM Ventures invests in OX Security to collaborate on software supply chain security. Intel CPUs have a major design flaw affecting billions of chips. Dark Reading highlights the impact of climate change on cybersecurity. Stay updated with Red Hat's newsletters on cybersecurity threats and emerging trends. Experts emphasize the need for strong leadership traits in cybersecurity. Concerns mount over ransomware, zero-day bugs, and AI-enabled malware. Users encouraged to use threat intelligence and manage cookie preferences for privacy and personalization. New update allows users to have more control over targeted advertising by accepting or rejecting cookies.\"
#cybersecurity #IBMVentures #threatintelligence #softcorpremium
Defining the Sensitive IAM Actions - Chris Farris
In a recent blog post, Chris Farris discusses the challenges of defining sensitive IAM actions in AWS. Farris shares his experience from his time at Turner, where concerns arose regarding the level of access provided by the ReadOnlyAccess policy. He highlights the need for a clear distinction between access to an environment and access to the data within that environment. Farris also acknowledges the ongoing discussions within the cloud security community surrounding this issue. He mentions various requests and approaches from professionals seeking read-only IAM policies for auditing purposes. Farris points out that the problem lies in the lack of comprehension of access and authorization levels, rather than the ReadOnlyAccess policy itself. To address this, he introduces the Sensitive Actions Repo, a machine-readable YAML file that enumerates actions leading to sensitive outcomes. Farris encourages collaboration and contributions to the repo to enhance policy creation and awareness in the cloud security community. Finally, he highlights the need for consistency and ownership within AWS to ensure a better experience for customers.
#IAMchallenges #cloudsecuritycommunity #AWSpolicycreation #softcorpremium
Health Data of 4M Stolen in Cl0p MOVEit Breach of Colorado Department
The Colorado Department of Health has suffered a major data breach, with the personal health information of 4 million individuals being stolen by the Cl0p ransomware group. This incident highlights the ongoing threat of cyberattacks on sensitive healthcare data. In other news, the SecTor conference in Canada will cover various topics including best practices and tools for OT and IT security. The conference will also have webinars focusing on the dark side of AI and its threats in cybersecurity. It is important to stay informed about the latest cybersecurity threats and protect against ransomware, zero-day bugs, and AI-enabled malware.
#cybersecuritythreats #healthcaredata #sektorconference #softcorpremium
Kaspersky explains how phishing works - Back End News
Cybercriminals are increasing their phishing efforts to obtain personal information through various channels such as emails, SMS, and social media. Kaspersky, a cybersecurity solutions company, explains how phishing works and provides tips on how to spot phishing attempts. Phishing involves deceiving victims into revealing personal information by posing as legitimate organizations. Kaspersky has observed a 40% increase in cryptocurrency phishing and reports that most phishing topics in 2022 were related to employment compensations, bonuses, and promotional campaigns by major banks. The company also discovered an emerging APT threat actor in APAC. Phishing attacks often unfold in multiple stages, with scammers initially requesting information about a victim's products or services before launching a phishing attack. Kaspersky predicts that phishing will continue in 2023, with cybercriminals posing as banks and large enterprises. They have also observed an increase in targeted phishing attacks involving active correspondence with victims. It is expected that new tricks will emerge in the corporate sector, generating significant profits for attackers.
#Cybersecurity #PhishingAttacks #Kaspersky #softcorpremium
What's New in the NIST Cybersecurity Framework 2.0
The National Institute for Standards and Technology (NIST) has released an updated version 2.0 of its popular Cybersecurity Framework. The new framework now includes a sixth function called \"govern\" and is aimed at organizations of all sizes, expanding beyond its original focus on critical infrastructure. The update is intended to reflect current usage and anticipate future needs in cybersecurity. The framework is designed to help organizations manage cyber hygiene, incident response, and overall cybersecurity strategy. NIST is currently gathering comments on the draft framework until November 4.
#CybersecurityFramework #NIST #CyberHygiene #softcorpremium
Phishing Operators Make Ready Use of Abandoned Websites for Bait
Phishing operators are exploiting abandoned websites to launch attacks and trick individuals into revealing sensitive information. It is important for individuals and organizations to be cautious when interacting with unfamiliar websites to protect their data. The SecTor IT Security Conference in Canada will cover best practices and tools for cybersecurity, as well as the threats posed by AI. Kaspersky reports that phishers are increasingly targeting WordPress websites due to vulnerabilities in the platform. Attackers are using new techniques to hide phishing pages on hacked websites, making detection more difficult. Phishing pages have a short lifespan, with many becoming inactive within hours. It is crucial to regularly update and secure websites to prevent phishing attacks. Cybercriminals are targeting legitimate websites to set up phishing traps, highlighting ongoing cybersecurity threats. A major security flaw has been found in Intel CPUs, and the impact of climate change on security is being addressed. Understanding the risks posed by third-party vendors and managing identity in cloud and hybrid environments is important. AI poses potential cybersecurity threats, and tools for enhancing security in OT and IT are needed. Threat intelligence is valuable in mitigating risks, and DNS attacks continue to be a prominent issue. Being aware and proactive in the face of evolving cybersecurity challenges is essential. The use of cookies on websites raises concerns about privacy and tracking, and users should carefully consider their cookie settings. Browser and internet device identification is essential for targeted advertising, but allowing cookies enables personalized ads.
#cybersecurity #phishingattacks #AIthreats #softcorpremium