💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
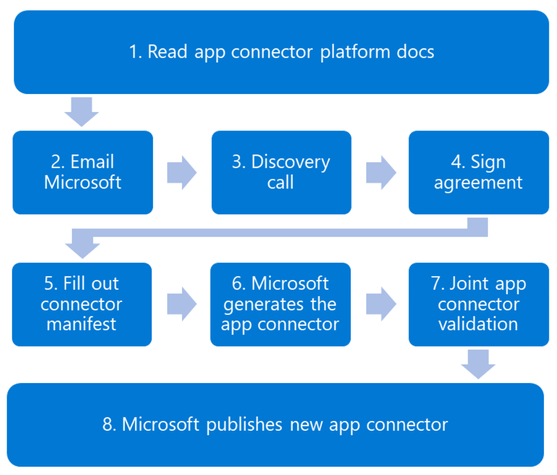
Microsoft empowers partners to securely build their own connector on its Open App Connector Platform - Microsoft Community Hub
Microsoft has announced the Open App Connector Platform in public preview, allowing SaaS vendors to easily build and maintain their own connectors while benefiting from Microsoft Defender's built-in app security features. Asana and Miro are the first partners to build connectors using this platform, enabling organizations to connect and protect both apps under the Microsoft XDR umbrella. The Open App Connector Platform simplifies connector development by eliminating the need for coding and reducing integration time. SaaS vendors can enhance their app security capabilities and expand to new customers through automatic inclusion in the Microsoft 365 Defender partner catalog. Embracing App Connectors is crucial for customers to fully leverage Microsoft's SaaS security offering and protect their business operations. SaaS vendors are invited to join the Open App Connector platform and build connectors for their SaaS apps.
#OpenAppConnectorPlatform #MicrosoftDefender #SaaSConnectors #softcorpremium
Azure Virtual Desktop Watermarking Support - Microsoft Community Hub
Microsoft has announced the general availability of watermarking support in Azure Virtual Desktop. This optional protection feature acts as a deterrent for data leakage by displaying QR codes on the session desktop. Watermarking was first introduced in February 2023 and is now available on the Azure Virtual Desktop web client. The QR codes embed the session user's Activity ID, providing traceability to help identify potential data leak sources. Currently, only clients that support this feature can connect to the remote session. Administrators can configure the opacity and granularity of the displayed QR codes. To learn more about setting up watermarking support and other security best practices, visit Microsoft Learn.
#AzureVirtualDesktop #DataSecurity #MicrosoftLearn #softcorpremium
Conditional Access for Protected Actions is Now Generally Available! - Microsoft Community Hub
Microsoft has announced the general availability of Conditional Access for Protected Actions, a feature that allows organizations to protect critical administrative operations with Conditional Access policies. Protected actions are high-risk operations that can compromise an organization's security if executed by a malicious actor. With this feature, organizations can add an extra layer of protection by defining granular policies that specify the conditions under which users can perform these actions. For example, administrators may be required to complete phishing-resistant multi-factor authentication or use a compliant device before making changes to a conditional access policy. Microsoft is continuously adding support for more protected actions based on customer feedback. Users are encouraged to explore this powerful feature and provide feedback. Learn more about Microsoft Entra and the Protected Actions feature through Microsoft's documentation and discussion spaces.
#ConditionalAccess #ProtectedActions #softcorpremium
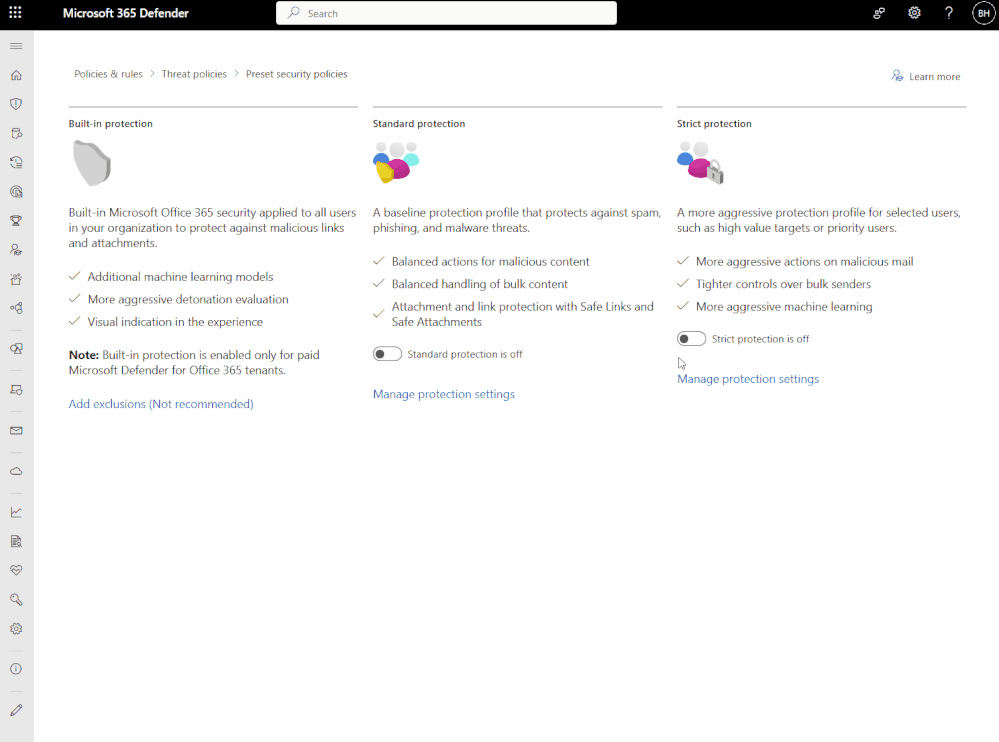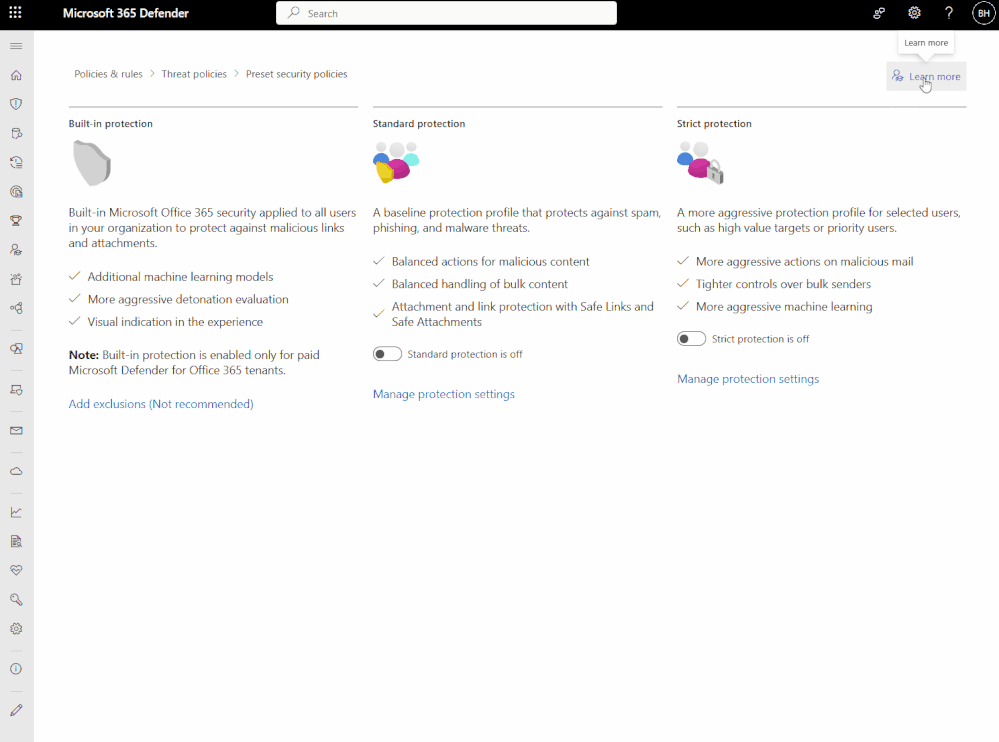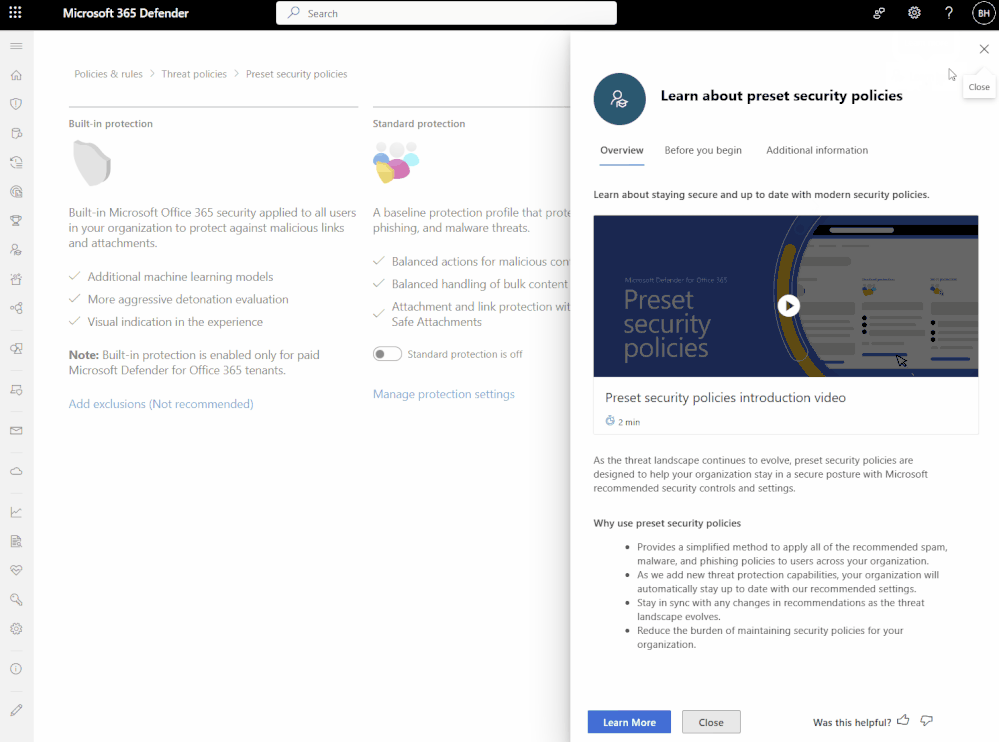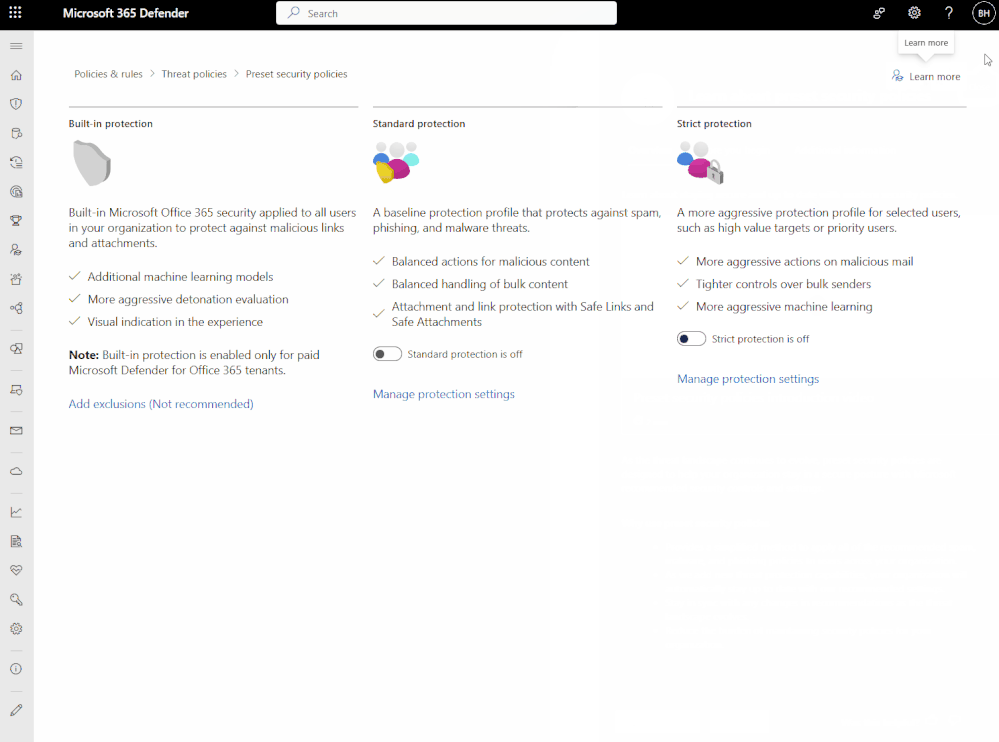
Announcing the availability of in-product guidance! - Microsoft Community Hub
Microsoft has announced the general availability of their new in-product guidance, which aims to provide users with the necessary tools to become security operations heroes. This feature is designed to help users quickly learn about and navigate through Microsoft Defender, offering step-by-step guides and key information for success. The guidance can be accessed through a \"Learn More\" button located on the top right of the interface. The new experience will automatically pop out on certain pages to assist users right from the start. Microsoft encourages users to test out the new feature and provide feedback on the content and areas they would like to see improved. Overall, the in-product guidance is part of Microsoft's ongoing efforts to enhance the user experience of Microsoft Defender for Office 365.
#MicrosoftDefenderGuidance #EnhancedUserExperience #softcorpremium
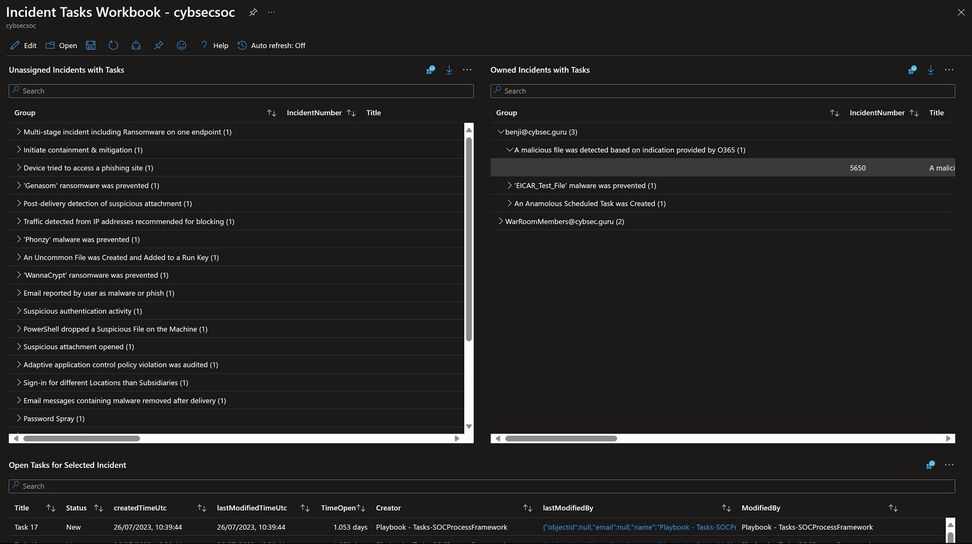
Automate tasks management to protect your organization against threats - Microsoft Community Hub
Microsoft has announced new updates to its Sentinel platform, aimed at improving task management and efficiency for security analysts. The updates include new playbooks, a workbook, and Log Analytics logs, as well as an integration with Microsoft 365 Defender SecOps. The playbooks offer guided response workflows for investigating and responding to security incidents, while the workbook provides a comprehensive overview of task progress and completion. These updates aim to streamline the workflow of security teams and enhance an organization's defenses. Additionally, the SOC Process Framework has been updated to support tasks, allowing for easier integration with Sentinel. Overall, these updates aim to automate task management and improve the efficiency of security analysts in managing and remedying incidents.
#SecurityUpdates #EfficiencyEnhancement #softcorpremium
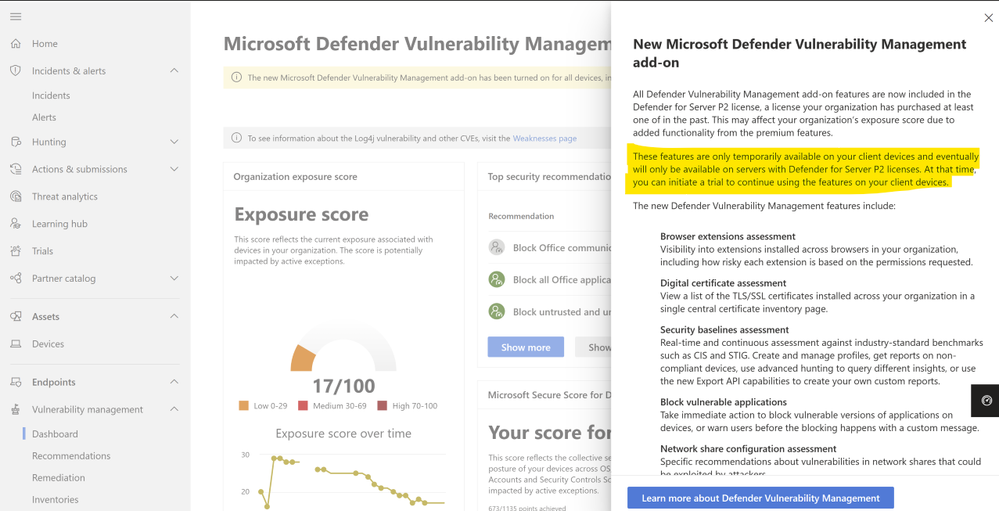
Update on Defender Vulnerability Management capabilities in Defender for Servers Plan-2 - Microsoft Community Hub
Microsoft has made changes to the availability of its Defender Vulnerability Management (MDVM) capabilities for eligible devices. These capabilities are now only accessible to customers with a Defender for Servers Plan 2 (DfS-P2) and can be accessed via the Microsoft 365 Defender portal. Customers who want to continue using these capabilities on their client devices can either start a free trial of the Defender Vulnerability Management Standalone or purchase the Defender Vulnerability Management Add-on license for their Defender for Endpoint Plan 2 devices. This update allows Defender customers to utilize the premium capabilities on their eligible server devices as well. For more information and to access a free 90-day trial, visit the Microsoft website.
#MicrosoftDefender #VulnerabilityManagement #softcorpremium
What’s new with Microsoft Entra ID Protection - Microsoft Community Hub
Microsoft Entra ID Protection (formerly Azure AD Identity Protection) has announced key enhancements to its platform, including a new dashboard, advanced detections, real-time threat intelligence, and integration with Microsoft 365 Defender. The new dashboard provides insights, visualizations, and recommendations to help organizations understand their security posture and address attacks. The platform also offers new detections to block existing attacks and protect against emerging threats. With the integration of Entra ID Protection with Microsoft 365 Defender, security teams can investigate incidents and respond to identity compromises more efficiently. These updates enhance Microsoft's goal of providing best-in-class identity security.
#MicrosoftEntraIDProtection #IdentitySecurity #Microsoft365Defender #softcorpremium
Enhanced Company Branding for Sign-in Experiences Now Generally Available - Microsoft Community Hub
Microsoft has announced the general availability of enhanced company branding functionality for Microsoft Entra ID and Microsoft 365 sign-in experiences. This feature allows for customization of sign-in pages, including the ability to create a custom look and feel, target specific browser languages, and customize self-service password reset, footer hyperlinks, and browser icons. Users can also configure layout and add custom logos. To get started, users need to set up Entra ID P1, P2, or Office 365. Learn more about this feature on the Microsoft Entra website.
#MicrosoftEntraID #Microsoft365 #CompanyBranding #softcorpremium
Unleash the Power of Threat Intel: Introducing the MDTI GitHub - Microsoft Community Hub
Microsoft Defender Threat Intelligence (Defender TI) has launched its official GitHub repository, offering technical solutions to help security operations centers maximize Microsoft Threat Intelligence. The repository provides access to various solutions, including M365 Advance hunting queries, MDTI playbooks, notebooks, Postman Collection, and workbooks. The Typosquat playbook helps with brand protection by identifying typo squat domains, while the Latest Threat Trends playbook provides visibility into the latest threat trends. Users can access the GitHub repository at aka.ms/MDTIGitHub and sign up for a trial of MDTI Premium or MDTI API licenses. Microsoft encourages feedback and contributions to the repository.
#MicrosoftDefenderThreatIntelligence #GitHubRepository #SecurityOperationsCenters #softcorpremium
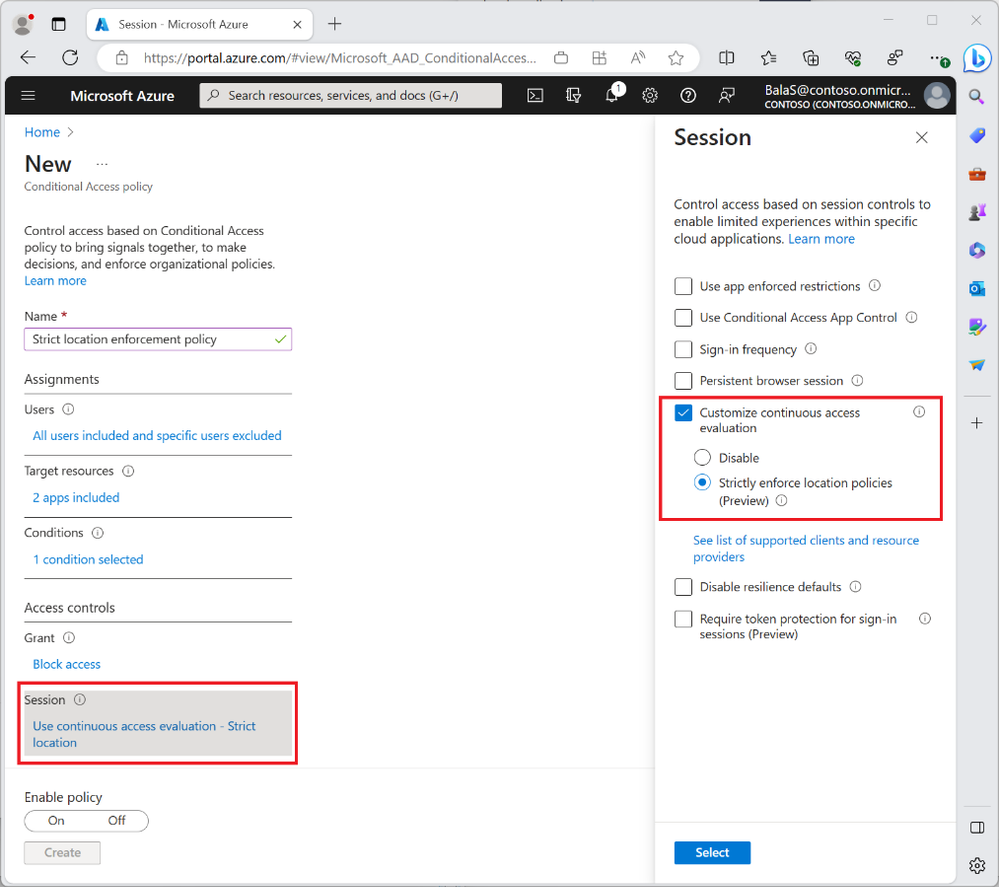
Public Preview: Strictly Enforce Location Policies with Continuous Access Evaluation - Microsoft Community Hub
Microsoft has announced a new feature in public preview that allows strict enforcement of location policies with continuous access evaluation (CAE). This feature helps prevent token theft by revoking tokens in near real-time if they violate IP-based location policies. This ensures that stolen tokens cannot be replayed outside the trusted network. To enable this feature, users must include all IP addresses from which they access Microsoft Enterprise ID and resource providers in the IP-based named locations policy. This step forward in session management provides more control and confidence to administrators while maintaining a seamless user experience.
#MicrosoftSecurity #ContinuousAccessEvaluation #SessionManagement #softcorpremium
Streamline the process to bring your own detections in Microsoft Purview Insider Risk Management - Microsoft Community Hub
Microsoft Purview Insider Risk Management allows organizations to gain a unified view of insider risks in their multicloud environments. Admins can incorporate detections from various platforms and systems, such as Sentinel, Salesforce, and Dropbox, into Insider Risk Management policies to detect data theft and leaks. By automating the process of bringing in risk detections and creating custom indicators, security teams can obtain a comprehensive understanding of potential security incidents across different applications. The process involves authoring analytics rules, streaming risk detections from Sentinel to Insider Risk Management, creating custom indicators, and conducting in-depth investigations. This feature is currently in public preview.
#MicrosoftPurview #InsiderRiskManagement #MulticloudSecurity #softcorpremium
Supercharging Investigations With Cado’s New Timeline - Cado Security | Cloud Forensics & Incident Response
Cado Security has released a new timeline feature that aims to improve investigations and incident response in complex, multi-cloud environments. The platform automates data capture and provides a unified view of hundreds of data sources across cloud-provider logs, disk, memory, and more. The new timeline view offers a more intuitive navigation experience, while faceted search allows users to narrow down search results quickly. Additionally, saved search functionality enables users to save and reuse investigation queries, saving time and enabling rapid search and visibility. Cado Security's mission is to provide security teams with a faster and smarter way to perform forensics investigations in the cloud.
#cloudsecurity #incidentresponse #forensicsinvestigations #softcorpremium
Prioritize Risks and Add Context to Amazon Inspector Findings with Solvo Data Posture Manager | AWS Partner Network (APN) Blog
Solvo, in partnership with AWS, has developed Solvo Data Posture Manager to address the lack of visibility and control over sensitive data in the cloud. This solution helps track the movement of files containing sensitive data and ensures they are protected with appropriate access policies and controls in real time. It also helps manage access and permissions for cloud resources, preventing users and applications from accumulating unnecessary privileges. Solvo's multi-dimensional security approach aims to tackle the increasing security concerns surrounding cloud environments.
#cloudsecurity #dataprivacy #accessmanagement #softcorpremium
Threat Detection Queries for Azure WAF - Microsoft Community Hub
Azure Web Application Firewall (WAF) is a cloud-native service that protects web apps from common web-hacking techniques. By integrating Azure WAF with Microsoft Sentinel, users can automate the detection and response to threats and attacks. This can be done by building Analytic rules/detections in Sentinel for attacks such as Code Injection. The process involves configuring an Analytic Rule in Sentinel using pre-built queries from the Azure-Network-Security GitHub Repository. Once the rule is set up, Sentinel will create incidents based on WAF logs that record any Code Injection attacks, providing additional support for security analysts to respond to future threats. This method allows for centralized security and saves time and effort in updating WAF policies.
#AzureWAF #AutomatedThreatResponse #CentralizedSecurity #softcorpremium
How to Receive Alerts When Your IAM Configuration Changes | AWS Security Blog
The AWS Security Blog has released a post on how to receive alerts when changes are made to your IAM (Identity and Access Management) configuration. IAM is a service that helps manage access to AWS services and resources securely. While IAM provides detailed logs of its activity, it doesn't inherently provide real-time alerts or notifications. However, you can use a combination of AWS CloudTrail, Amazon EventBridge, and Amazon SNS (Simple Notification Service) to set up notifications for IAM configuration changes. The blog post provides a step-by-step guide on how to implement this setup and ensure you're notified of critical events in your AWS environment. It also discusses how to centralize EventBridge alerts using a multi-account architecture and how to monitor calls to IAM using filter patterns. By monitoring IAM security configuration changes, you can enhance your overall security and respond to unexpected events effectively.
#AWSIAM #CloudSecurity #RealTimeAlerts #softcorpremium
Threat Detection Queries for Azure WAF - Microsoft Community Hub
Microsoft Azure Web Application Firewall (WAF) is a cloud-native service that protects web apps from common web-hacking techniques. By integrating Azure WAF with Microsoft Sentinel, users can automate the detection and response to threats and save time on updating the WAF policy. This can be done by configuring Analytic Rules in Sentinel using pre-built detection queries available in the Azure-Network-Security GitHub Repository. This allows for the automated detection and response to attacks such as Code Injection. The steps for setting up Analytic Rules in Sentinel are provided, along with a sample query for Code Injection detection. The WAF logs must be present in the Log Analytic Workspace for the Analytic Rule to work properly. The configured Analytic Rule in Sentinel will create incidents based on WAF logs, providing additional support for security analysts to respond to future threats.
#MicrosoftAzure #WebApplicationFirewall #SecurityAutomation #softcorpremium
Do I Need VPN Connectivity for Windows Hello for Business Registration - Microsoft Community Hub
In this tech news update, Zoheb Shaikh, a Solution Engineer at Microsoft, discusses the issue of users failing to register for Windows Hello for Business (WHFB) without connecting to a VPN or the office network. He explains that WHFB replaces passwords with strong two-factor authentication on devices and shares the feedback from a customer who implemented WHFB in a hybrid environment with domain controllers on 2019 and Azure AD Connect. The customer experienced smooth enrollment and authentication for users in the office, but some users working from home had issues setting their PIN or experienced failures during logon. The workaround was to connect to VPN, login with PIN, and then continue working without a VPN connection. The customer expected WHFB enrollment to work seamlessly for users working from home. Zoheb and his team researched the issue and concluded that a newly provisioned user needs line of sight to the domain controller for the first time for successful authentication. However, for users who never connect to VPN or visit the office, a Cloud Only trust model can be used without the need for the domain controller in line of sight.
#WindowsHelloForBusiness #TwoFactorAuthentication #RemoteWork #softcorpremium
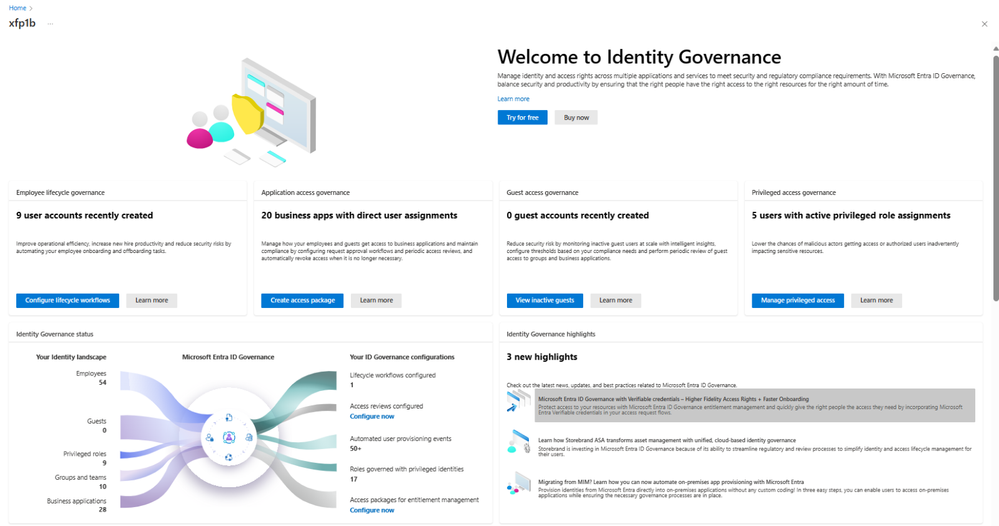
New Microsoft Entra ID Governance Dashboard Experience Rolling Out Soon - Microsoft Community Hub
Microsoft Entra has announced the general availability of its ID Governance platform, offering new capabilities for streamlined access management. The platform includes a dashboard that provides an overview of identity governance controls, access to compliance reports, and features to assess and improve security and compliance needs. Microsoft plans to further enhance the dashboard to align with user needs and simplify setup and configuration. Customers can try the new capabilities through a trial or by upgrading to Microsoft Entra ID Governance.
#MicrosoftEntra #IDGovernance #AccessManagement #softcorpremium
Optimizing endpoint security with Microsoft Defender for Endpoint's flexible licensing options - Microsoft Community Hub
Microsoft is expanding its Defender for Endpoint licensing options to allow customers to use different licenses on different devices based on their security needs. This new mixed licensing support will help organizations optimize their licensing usage, save costs, and ensure compliance. Customers can now control how licenses are applied with minimal management overhead, and access a usage report to monitor their license state. The feature applies only to client endpoints, and Windows Server/Linux devices require relevant Defender for Server licenses. Microsoft provides a step-by-step guide on how to enable mixed licensing support and validate license assignment at scale using dynamic tagging. This update aligns with Microsoft's commitment to delivering comprehensive security solutions for organizations of all sizes.
#DefenderforEndpoint #MixedLicensingSupport #ComprehensiveSecuritySolutions #softcorpremium
Clean up Inactive users with Microsoft 365 Lighthouse - Microsoft Community Hub
Microsoft has introduced a new feature in Microsoft 365 Lighthouse that allows Managed Service Providers (MSPs) to easily manage inactive user accounts across customer tenants. Inactive user accounts are those that have had no activity for a long time. These accounts can complicate user management tasks and pose security risks. Cleaning up inactive users can help improve security, reduce unnecessary billing for unused licenses, and increase efficiency. MSPs can now identify and clean up inactive user accounts through the Lighthouse platform, making the process faster and more streamlined. Blocking sign-in for these accounts is recommended as a minimum action to take. MSPs can take advantage of this new feature to improve user management practices and enhance overall security.
#Microsoft365Lighthouse #usermanagement #security #softcorpremium
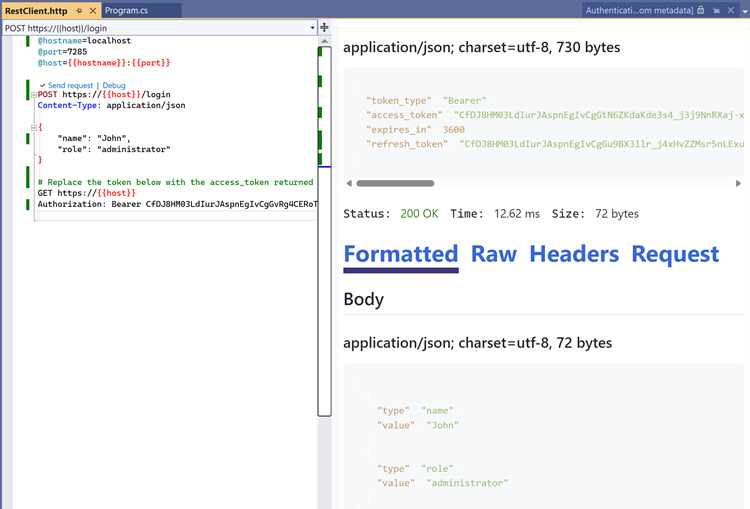
Jaliya's Blog: ASP.NET Core 8.0 Preview: All New AddBearerToken Extensions
ASP.NET Core 8.0 Preview introduces new extension methods for Bearer Tokens authentication. This feature is separate from JSON Web Tokens (JWT). Developers can add bearer token authentication using the Microsoft.AspNetCore.Authentication.BearerToken namespace. The authentication can be tested using a .http file, making it convenient for developers. This update provides improved security and authentication options for ASP.NET Core applications.
#ASPNETCore8 #BearerTokenAuthentication #ImprovedSecurity #softcorpremium
Streamlining Secrets Management for Enhanced Security Using CyberArk Secrets Hub and AWS | AWS Partner Network (APN) Blog
CyberArk and AWS have partnered to streamline secrets management for enhanced security. The solution, called CyberArk Secrets Hub, allows security teams to centrally manage secrets and credentials using CyberArk solutions, while developers can continue using AWS Secrets Manager. This solution helps organizations consolidate secrets management across multiple instances of AWS Secrets Manager and hybrid environments, reducing vault sprawl and improving security and efficiency. It also provides automated policy-based rotation and centralized audit capabilities. With CyberArk Secrets Hub and AWS, developers can continue using their existing tools while security teams gain full visibility of secrets across the enterprise.
#CyberArkSecretsHub #AWSsecretsmanagement #securityandefficiency #softcorpremium
Released: August 2023 Exchange Server Security Updates - Microsoft Community Hub
Microsoft has released security updates for vulnerabilities found in Exchange Server 2019 and Exchange Server 2016. These updates address vulnerabilities responsibly reported to Microsoft and are recommended for immediate installation. Exchange Online customers are already protected and do not need to take any action. Administrators may need to perform additional actions to address certain vulnerabilities. Microsoft also announced support for a change in the default encryption algorithm in Microsoft Purview Information Protection. The update installation process and known issues are provided in the release. Exchange Server 2013 is no longer supported and users are advised to migrate to Exchange Server 2019 or Exchange Online.
#MicrosoftSecurityUpdates #ExchangeServerUpdates #PurviewInformationProtection #softcorpremium
TTP-based threat hunting with Security Analytics solves alert noise
Dynatrace, a leading cybersecurity company, has developed a solution called Dynatrace Security Analytics to address the challenges faced by security analysts in detecting and preventing advanced cyberattacks. The system brings together various data sources to derive high-level attacker tactics, techniques, and procedures (TTPs), providing a clearer understanding of threats and enabling quicker action. It offers real-time monitoring and detailed technical information on attacks, helping businesses respond effectively. Dynatrace has also integrated its platform with open-source tools like Falco to enhance security measures and offer context-rich insights. The company's latest offering, Grail, provides comprehensive observability and security data analytics capabilities. Dynatrace is continuously working on improving its threat hunting strategies and detection techniques to combat evolving cyber threats.
#CybersecuritySolutions #ThreatHunting #SecurityAnalytics #softcorpremium
Cloudflare Radar's new BGP origin hijack detection system
Cloudflare has launched a new system called Radar to detect BGP origin hijacks, which are instances where malicious actors falsely claim ownership of IP addresses they do not control. BGP hijacks allow attackers to redirect traffic and intercept data. Cloudflare's system aims to identify these hijacks and protect networks from such attacks. The system uses multiple data sources and three modules to detect and analyze potential hijack events. Cloudflare has also released several datasets that provide valuable information about the relationship between autonomous systems (AS) in the internet infrastructure. Additionally, they have introduced a new feature to calculate the end of hijack events and a lightweight command line application for BGP hijack detection. Cloudflare's BGP hijack detection results are available on their Radar website and API. They are urging people to join them in building a more secure internet and offer insights on various internet-related issues.
#Cybersecurity #NetworkProtection #SecureInternet #softcorpremium