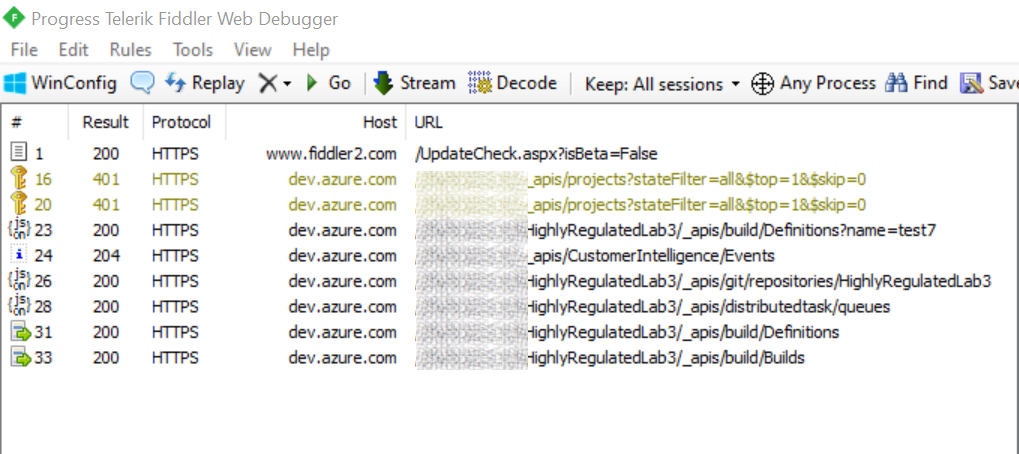
Intercepting Azure CLI HTTP traffic leveraging Fiddler
Its sometimes helpful to look at the HTTP Requests generated by the Azure CLI to understand how to replicate certain scenarios when it's not clear from documentation.

Its sometimes helpful to look at the HTTP Requests generated by the Azure CLI to understand how to replicate certain scenarios when it's not clear from documentation. Usually capturing HTTP traffic using Fiddler "Just works" as the system proxy is updated to point to "http://127.0.0.1:8888" which is the default endpoint used by fiddler to setup a local proxy.
When capturing SSL/TLS traffic we also need to trust Fiddlers Root Certificate by adding it to our local certificate store.
When capturing Azure CLI traffic there are a few special considerations which are discussed on this GitHub issue - https://github.com/Azure/azure-cli/issues/7455
There are two interesting environment variables which are mentioned which we can leverage for our scenario.
AZURE_CLI_DISABLE_CONNECTION_VERIFICATION. This is UNSAFE and should not be used.
REQUESTS_CA_BUNDLE. This allows me to specify a path to the Fiddler cert and az will now work when Fiddler is running, however it will no longer work while Fiddler is not running. Given that a typical developer will turn Fiddler on and off multiple times throughout the day it is not feasible to expect to constantly flip environment variables.
Due to the Azure CLI's technology stack it seems it's not enough to just set AZURE_CLI_DISABLE_CONNECTION_VERIFICATION=1(at least on a Windows machine), in addition to setting this value we need to provide the a path to Fiddlers Root Certificate using REQUESTS_CA_BUNDLE.
You can perform the following steps to get this scenario working:
- Open certmgr.exe
- Find Fiddlers Root Certificate in Trusted Root Certification Authorities.
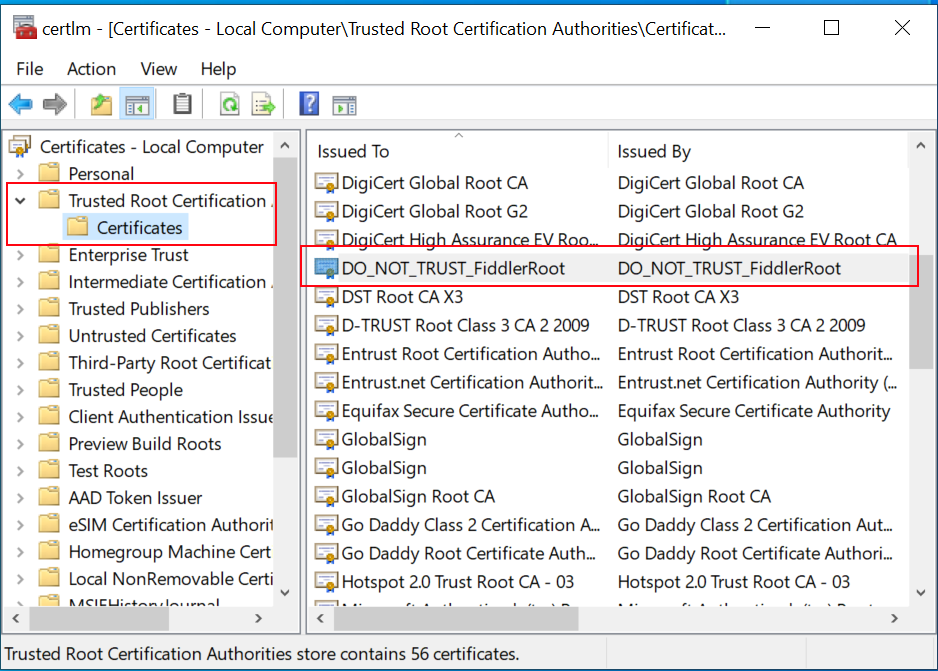
- Export the certificate in DER format
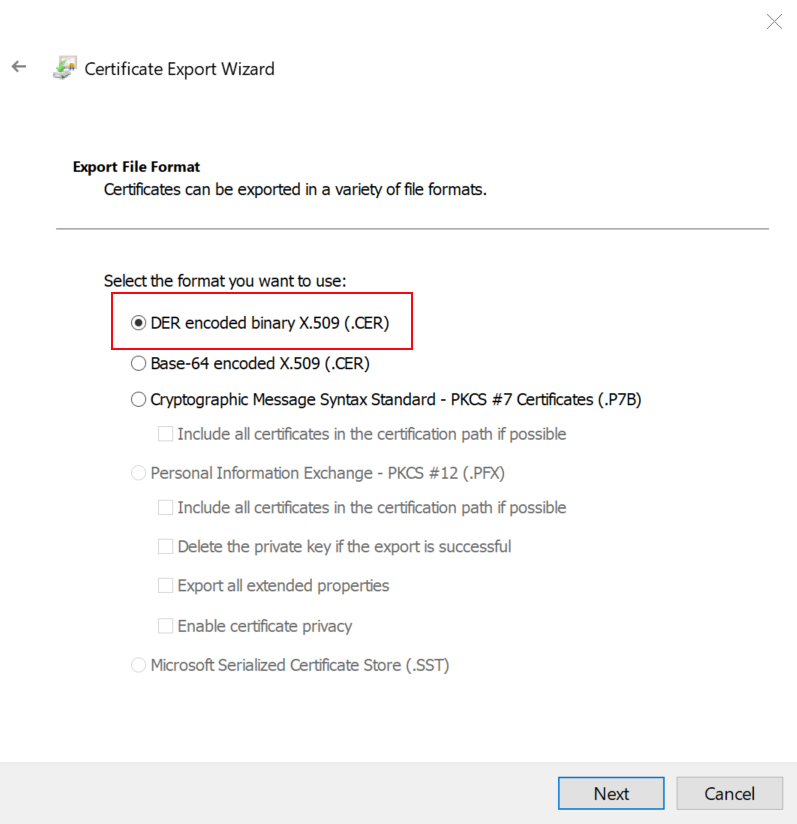
- Download the Windows binaries for openssl
- Use openssl to convert the exported .cer file to .pem
openssl x509 -inform der -in c:\temp\FiddlerRoot.cer -out c:\temp\FiddlerRoot.pem
- Set the following Environment Variables
SET REQUESTS_CA_BUNDLE="c:\temp\FiddlerRoot.pem"
- Run your Azure CLI Command, Fiddler should start to capture the generate requests.