💡
Attention readers! We want to let you know that the summaries in this newsletter are generated using cutting-edge generative AI technology. However, we understand the importance of accuracy and quality content, so our team of expert editors manually reviews each summary before it's published. If you feel the quality of a particular summary does not meet your expectations, please leave a comment in the Member Discussion section below. We will rectify it as soon as humanly possible!
What’s new in Microsoft Intune (2308) August edition - Microsoft Community Hub
Intune's August (2308) service release introduces several new capabilities aimed at improving device support, analytics, and security. For frontline workers, Remote Help for Android is now available, allowing IT admins to resolve device issues in real time. The analytical AI offerings have been expanded with settings insights that provide valuable information on successful configurations used by other organizations. Anomaly detection device cohorts help improve user experiences by identifying and proactively addressing device anomalies. Additionally, Intune has collaborated with Samsung to develop a device attestation solution that offers extra protection for Samsung devices. Feedback on these new releases is encouraged, and more features are promised for next month.
#IntuneUpdates #DeviceManagement #SecurityEnhancements #softcorpremium
Introducing Microsoft Sentinel Optimization Workbook - Microsoft Community Hub
Microsoft has introduced the Optimization Workbook for Microsoft Sentinel, aimed at improving cost efficiency, operational effectiveness, and overall management in organizations' security operations. The workbook consists of three tabs: Cost and Ingestion Optimization, Operational Optimization and Effectiveness, and Management and Acceleration. Each tab provides high-level insights and detailed information with recommendations for enhancing various aspects of security operations. The workbook helps organizations optimize costs, improve operational efficiency, and enhance threat management. It offers visibility into data ingestion, operational efficiency, and threat management, enabling security teams to make informed decisions and stay ahead of potential threats. To use the workbook, users need to have auditing and health monitoring data and can find it in the Content Hub or the Workbooks blade. The Optimization Workbook is a valuable tool for organizations looking to enhance their security operations.
#securityoperations #optimizationworkbook #threatmanagement #softcorpremium
Latest functionalities uplevel asset management and enhance data visibility
Microsoft Defender External Attack Surface Management (Defender EASM) has introduced new functionalities to enhance asset management and improve data visibility. The latest updates include the consolidation of insights into one area, allowing users to easily view and understand high, medium, and low priority observations related to assets. Users can now modify more than 25 assets at once, saving time and increasing efficiency for bulk asset modifications. The addition of a Task Manager section provides key information about tasks and their status, while notifications keep users updated on task progress. Dashboard chart exports allow users to download asset details, and saved queries enable organizations to quickly access recurring searches. New regions have been added to Defender EASM, and enhancements include the addition of asset labels in data connections and the blocking of private IP addresses to prevent workspace issues. Users can provide feedback and engage with the security professional community to further improve Defender EASM and strengthen security posture.
#MicrosoftDefenderEASM #AssetManagement #SecurityEnhancements #softcorpremium
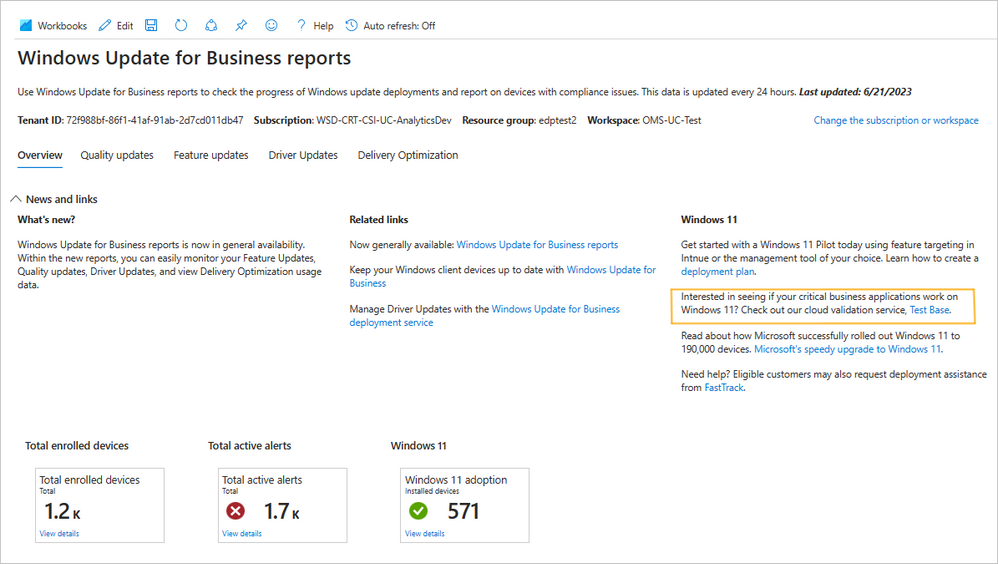
What’s new in Test Base for Microsoft 365: August 2023 - Windows IT Pro Blog
Microsoft's Test Base for Microsoft 365 has achieved ISO/IEC 27001:2013 certification, demonstrating its commitment to security and compliance. The service now allows customers to access Test Base from the Windows Update for Business reports page, simplifying the process of validating applications against Windows updates. Test Base also introduces new capabilities, such as WinGet package onboarding and testing against custom images. Additionally, Test Base supports testing apps for Windows on Arm and aids in the migration to Windows 11. Developers and IT professionals can join the Test Base community and access resources on GitHub.
#MicrosoftTestBase #WindowsUpdateForBusiness #TestBaseCommunity #softcorpremium
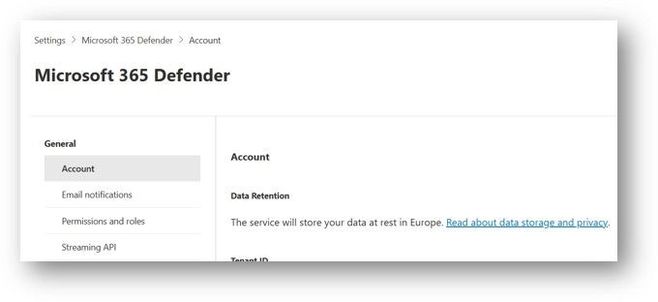
Microsoft Defender data can now be hosted locally in Australia
Microsoft has announced that their security and compliance services, including Microsoft Defender for Endpoint, Microsoft 365 Defender, and Microsoft Defender for Identity, now support data residency in Australia. This means that Australian customers can confidently onboard to these services knowing that their data at rest will remain within Australian boundaries, allowing them to meet regulatory obligations and maintain control over their data. The services offer advanced threat detection and response capabilities. To configure the data residency location, customers need to determine the current location in the Microsoft 365 Defender portal and contact Customer Service and Support for a tenant reset if necessary. Once the reset is complete, devices can be onboarded to the new tenant. Windows devices can simply use the onboarding script, while macOS and Linux devices will need to reinstall and onboard with the new script. A restart is required for the changes to take effect.
#MicrosoftSecurityAustralia #DataResidencyAU #AdvancedThreatDetection #softcorpremium
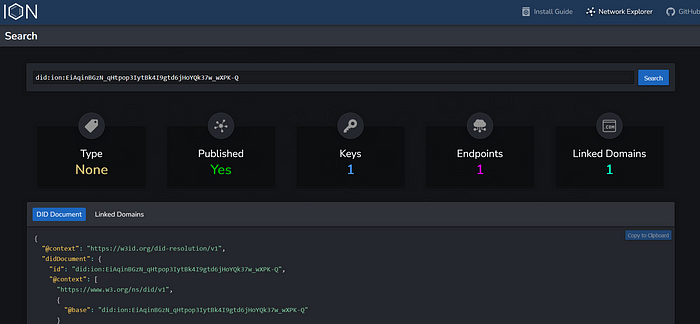
Creating a Decentralized Identifier (DID) | by Rory Braybrook | The new control plane | Aug, 2023 | Medium
Microsoft has introduced a decentralized identifier (DID) solution called ION, which offers self-owned and globally unique identifiers. The Entra system provides two trust systems, Web and ION, for tenant onboarding. Users can use npm commands to add necessary dependencies and generate and publish DIDs. A mysterious string of characters has been shared on social platforms, leaving many speculating about its meaning. Tech enthusiasts are working to decipher the code. A new technology registration process using the ION protocol marks a significant advancement in decentralized identity technology. The DIF Universal Resolver now supports searching for public keys of DIDs.
#MicrosoftION #DecentralizedIdentityTech #DIFUniversalResolver #softcorpremium
Why is CIRA all the Hype for Cloud Incident Response? - Cado Security | Cloud Forensics & Incident Response
CIRA, or Cloud Investigation and Response Automation, is an emerging category within cloud security that enables security teams to automate the collection and analysis of forensic data in cloud environments. With the rapid shift to the cloud across all sectors, the need for effective incident response in the cloud has become crucial. CIRA technologies deliver key capabilities to help organizations understand and respond to cloud risk, including forensic data collection and analysis, investigation of various data sources, and automated remediation actions. Implementing CIRA is important because the cloud introduces complexity and dynamic elements that traditional incident response approaches cannot handle. Additionally, the growing scope of reporting regulations and the rise of cloud threats further highlight the need for CIRA. Cado Security offers a platform specifically designed to address the challenges of incident response in cloud environments, providing automation and access to forensic-level data.
#CIRA #cloudsecurity #incidentresponse #softcorpremium
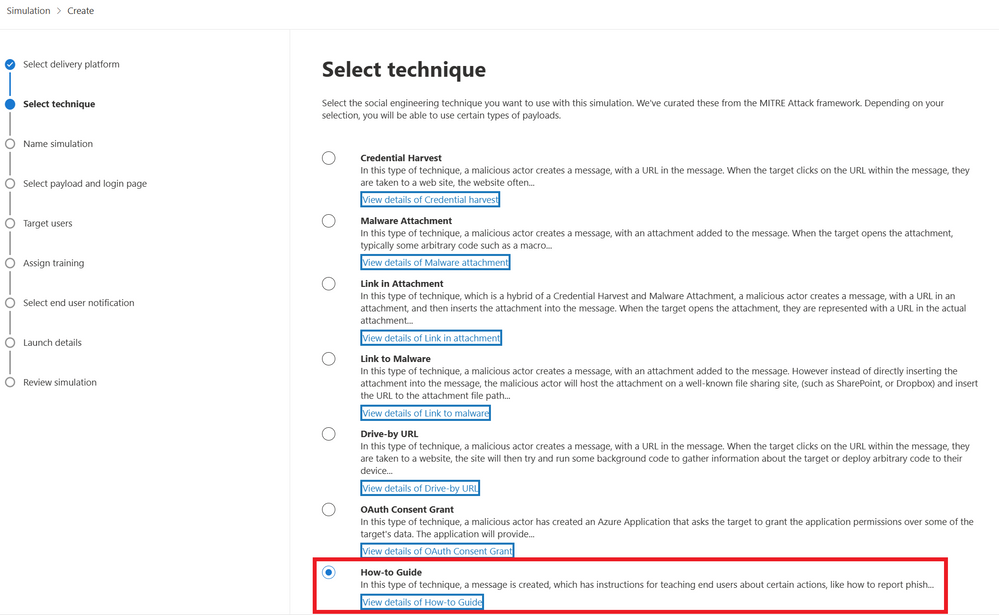
Send "How-to guides" to your organization from Attack Simulation training - Microsoft Community Hub
Attack Simulation Training, an intelligent phish risk reduction tool, has added a new feature called \"How-to Guides\" to help users report phishing messages. These guides provide instructions to recipients on how to complete important security tasks, such as reporting suspicious emails. By delivering the guides directly to users' inboxes, the tool aims to improve end user participation during simulations and real attacks, bridging the gap between recognizing malicious messages and reporting them. Admins can customize the guides and use them to send regular reminders to users. The goal is to empower users with knowledge and confidence to protect themselves and their organizations from phishing threats.
#phishriskreduction #enduserempowerment #reportphishing #softcorpremium
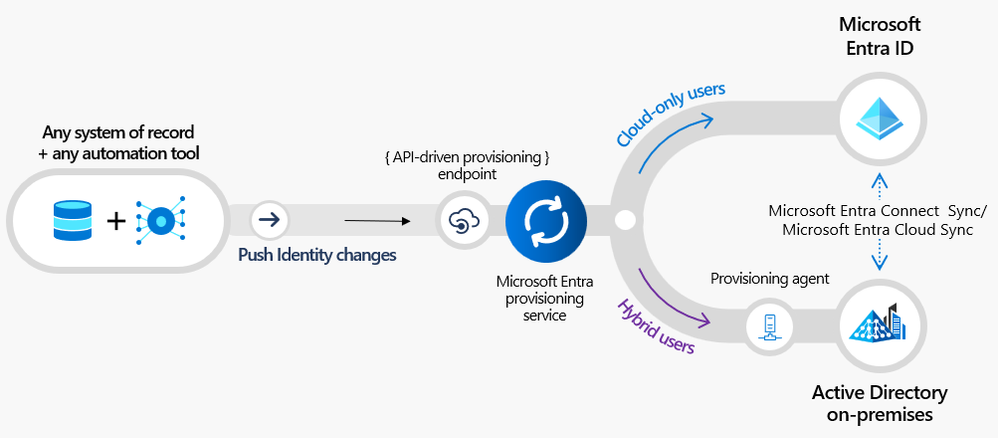
Introducing a New Flexible Way of Bringing Identities from Any Source into Microsoft Entra ID! - Microsoft Community Hub
Microsoft has announced the public preview of its Entra API-driven provisioning, expanding its support for HR-driven provisioning. The new feature allows for automatic provisioning of cloud-only users and hybrid users, importing data from sources like CSV files and SQL staging tables, and simplifying integration using standard SCIM schema attributes. Microsoft Entra also leverages Lifecycle Workflows to automate joiner-mover-leaver workflows for users sourced from any system of record. The API-driven provisioning can be configured through the Microsoft Entra Portal and grants permissions for uploading identity data using any automation tool of choice. This new capability provides flexibility for syncing identity data with authoritative sources, whether they are in the cloud or on-premises. The feature is currently in preview and requires Microsoft Entra ID P1 license or above.
#MicrosoftEntra #APIProvisioning #IdentitySync #softcorpremium
Let’s Architect! Security in software architectures | AWS Architecture Blog
The AWS Architecture Blog has released a post discussing the importance of security in software architectures. They provide resources and practices for securing cloud workloads, protecting against common attacks, and implementing the Zero Trust security model. They also delve into container security and offer guidance on migrating secrets to AWS Secrets Manager. Overall, the blog aims to help users build secure architectures and will continue to cover topics like cost optimization on AWS.
#AWSArchitecture #CloudSecurity #ZeroTrust #softcorpremium
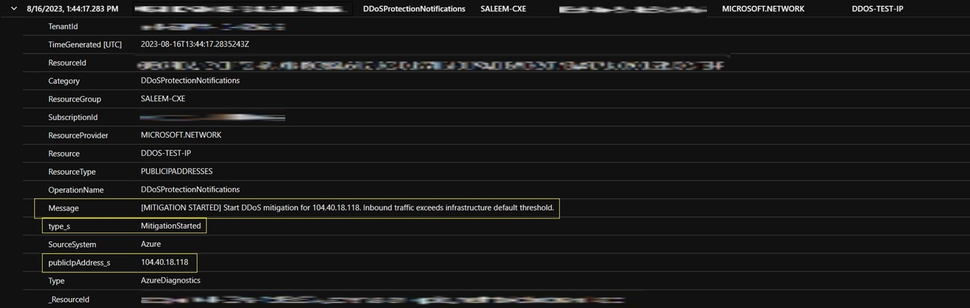
Strengthening Your Defenses: Simulation Testing for Azure DDoS Protection - Microsoft Community Hub
Microsoft Azure offers Azure DDoS Protection, a powerful security solution against DDoS attacks. DDoS simulation testing helps evaluate and enhance the effectiveness of Azure DDoS Protection. Azure offers two SKUs for DDoS protection: Network protection and Application protection. Azure's DDoS Simulation Partners, including BreakingPoint Cloud, Red Button, and RedWolf, offer simulation environments for testing against DDoS threats. RedWolf allows self-service or guided DDoS testing, while BreakingPoint Cloud enables initiating DDoS attacks on Azure resources. Posture.Gap Identification provides simulated DDoS attacks to optimize incident response procedures. BreakingPoint Cloud allows users to initiate DDoS attacks on Azure resources. Azure DDoS Network Protection enables easy creation of DDoS protection plans. Detailed information about each packet encountered during the mitigation process is now available. Regular reports on DDoS mitigation are provided, and logs can be sent to an analytics workspace for analysis. BreakingPoint Cloud allows users to authorize Azure subscriptions for DDoS simulation testing. Microsoft provides queries and logs for monitoring and analyzing DDoS attacks. Post-mitigation reports and Azure Monitor Workbook for DDoS Protection offer valuable insights. Simulation testing and quickstart guides are available to strengthen Azure DDoS Protection. Stay protected with these resources from Microsoft.
#AzureDDoSProtection #SimulationTesting #StayProtected #softcorpremium
Manage Access to Microsoft Sentinel Workbooks with Lower Scoped RBAC - Microsoft Community Hub
Microsoft Sentinel workbooks can now be used for reporting to leadership without granting access to the entire workspace. This can be achieved through table-level and resource-level RBAC components. Table-level RBAC ensures access to specific data tables, while resource-level RBAC limits visibility to the workbook of interest. Configuration involves creating custom roles and assigning reader roles to tables. The workbook can be shared via a link, as the user does not have access to Microsoft Sentinel. Anticipated questions are addressed, such as the inability to hide the workspace from users and the option to create AAD groups for multiple users. This process is simple and effective for limited access to Microsoft Sentinel workbooks.
#MicrosoftSentinel #WorkbookAccess #RBAC #softcorpremium
Download the Microsoft Defender for Identity sensor - Azure Cloud & AI Domain Blog
Microsoft has released the Microsoft Defender for Identity (MDI) sensor, which can be downloaded from the portal. The installation package is the same for Domain Controllers, ADFS, and ADCS. Users can download the installer from the portal and then copy it to the target server to execute the installation. An access key is required during the installation, but it can be regenerated if needed. Regenerating the key will not affect any sensors that are already installed and operational.
#MicrosoftDefenderForIdentity #MDIsensor #installationpackage #softcorpremium
How to automate the review and validation of permissions for users and groups in AWS IAM Identity Center | AWS Security Blog
AWS Security Blog has published a post on how to automate the review and validation of permissions for users and groups in AWS IAM Identity Center. The blog post addresses the challenges faced by organizations in maintaining control over permissions and conducting regular audits. It provides a step-by-step guide on how to automate the permission review process using AWS serverless services and AWS SDK. The solution includes scheduling the review process based on preferred frequency and generating a business-specific access and permission review report. The blog post also provides instructions on deploying the solution using AWS SAM CLI and cleaning up the resources afterwards.
#AWSIAM #automatepermissions #securityaudit #softcorpremium
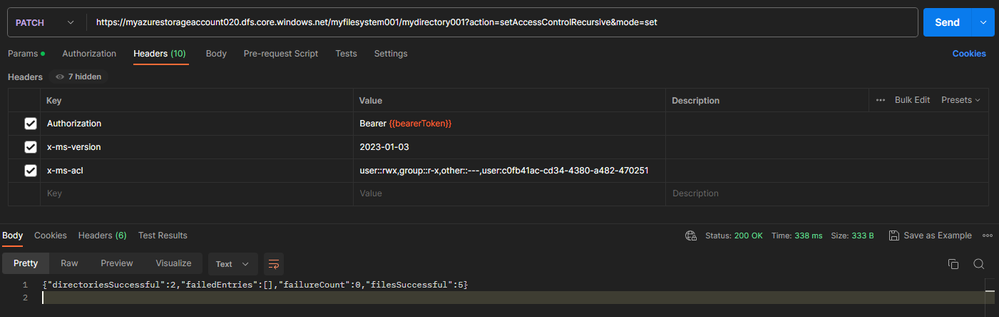
How to set ACLs Recursively? - Microsoft Community Hub
Ensuring proper access control is crucial for protecting Azure Storage assets. Azure Storage Account's Access Control Lists (ACLs) play a key role in setting permissions for containers and blobs. Now, you can set, update, or remove ACLs recursively for pre-existing child items of a parent directory, saving time and effort. This can be done using PowerShell, AZ CLI, or Postman. It's important to handle permission or runtime failures properly, obtaining a continuation token and restarting the process if necessary. Executing the ACL process within an Azure Virtual Machine in the same region is recommended for optimization. Additionally, Azure Storage Explorer offers a convenient option to propagate ACLs recursively. Follow the provided references for detailed instructions on managing ACLs in Azure Data Lake Storage Gen2 using different methods.
#AzureStorageACLs #AccessControlLists #AzureDataLakeStorageGen2 #softcorpremium
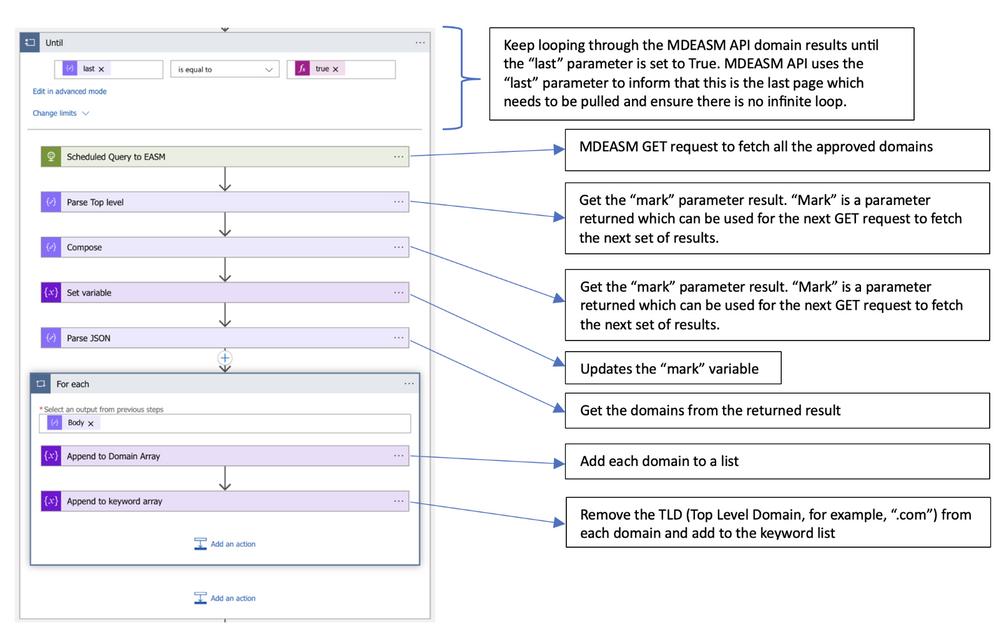
One Microsoft: Enriching owned assets with Threat Intelligence Feeds
Microsoft Defender External Attack Surface Management (MDEASM) is a tool that helps organizations identify and manage vulnerabilities in their software systems and network infrastructure. It focuses on the external attack surface, which includes components and interfaces exposed to the outside world. By integrating MDEASM with Microsoft Defender Threat Intelligence (MDTI), organizations can prioritize vulnerabilities and protect against potential threats. The integration allows for the detection of patterns and anomalies that indicate emerging threats, and provides real-time updates on malicious domains, IP addresses, URLs, and file hashes. By leveraging MDTI's threat intelligence, organizations can make informed decisions and take immediate action to mitigate risks. The integration can be implemented using Azure Logic Apps and the MDEASM GitHub repository. Overall, the integration of MDEASM and MDTI helps organizations understand and prioritize vulnerabilities, ensuring that targeted assets are addressed promptly.
#MDEASM #MDTI #ThreatIntelligence #softcorpremium
New Threat Detections for Azure WAF - Microsoft Community Hub
Azure Web Application Firewall (WAF) is a cloud-native service that protects web apps from common web-hacking techniques. It can be integrated with Microsoft Sentinel to automate the detection and response to threats. The blog provides steps on how to build Analytic rules/detections in Sentinel for attacks like Code Injection, Path Traversal, and scanner-based attacks. It also explains the process of setting up Analytic Rules in Sentinel and using pre-built detection queries. The goal is to enhance security and save time and effort in updating WAF policies.
#AzureWAF #SecurityAutomation #WebAppProtection #softcorpremium
New Threat Detections for Azure WAF - Microsoft Community Hub
Azure Web Application Firewall (WAF) is a cloud-native service that provides centralized security against web-hacking techniques. By integrating Azure WAF with Microsoft Sentinel, users can automate the detection and response to threats. The blog explains how to build analytic rules in Sentinel for attacks like code injection, path traversal, and scanner-based attacks. The blog also provides pre-built detection queries for these attacks and guides users on setting up analytic rules in Sentinel. The rules can help security analysts respond to future threats and incidents. The goal is to enhance web application security and provide a comprehensive defense against malicious attacks.
#AzureWebApplicationFirewall #WebSecurity #ThreatDetection #softcorpremium
Defender for APIs Better Together with WAF and APIM
Microsoft has introduced a new service called Defender for APIs, which provides enhanced security for API endpoints. It offers visibility into crucial APIs, prioritization of vulnerabilities, and quick detection of active threats. This service works in conjunction with Azure Web Application Firewall (Azure WAF) and Azure API Management (APIM) to create a comprehensive security framework. Azure WAF provides centralized defense against web and API vulnerabilities, while APIM manages the entire API lifecycle. Defender for APIs augments these solutions by providing deep traffic analysis, machine learning-driven detection of API threats, and alignment with the OWASP API Top 10. The combination of these tools ensures complete monitoring and end-to-end security for APIs, with immediate threat detection and streamlined incident response. A real-world example demonstrates how these solutions can work together to protect against API threats. Overall, the collaboration between Microsoft Defender for APIs, Azure WAF, and APIM offers a comprehensive and effective security strategy against evolving cyber threats.
#DefenderForAPIs #AzureSecurity #APIProtection #softcorpremium
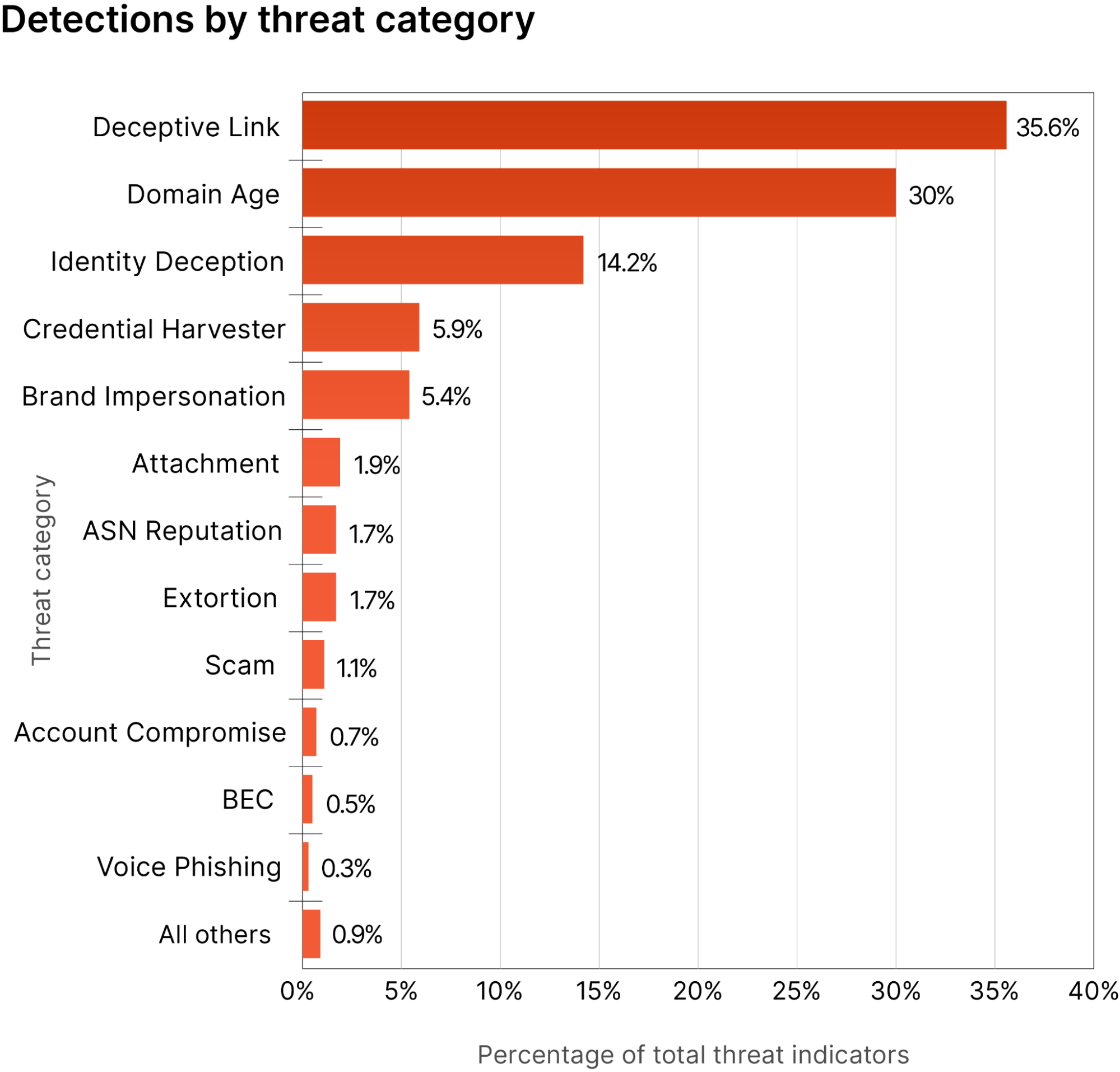
Introducing Cloudflare's 2023 phishing threats report
Cloudflare has released its first Phishing Threats Report, which analyzes phishing trends and provides recommendations based on data from May 2022 to May 2023. The report highlights evolving tactics used by attackers, the increasing prevalence of business email compromise attacks, and the need for proactive measures to address these evolving phishing trends. Cloudflare processed approximately 13 billion emails during this period, blocking around 250 million malicious messages. The report provides insights on the top email threat indicators observed, including deceptive links, domain age, and brand impersonation. Cloudflare has also introduced a new email security service that utilizes advanced technology to detect potential threats and provide specific reasons for the disposition of a particular email. The report emphasizes the importance of understanding the limitations of email authentication protocols such as SPF and DKIM and recommends implementing additional measures to enhance email security. It also suggests adopting a Zero Trust security model and using phishing-resistant multifactor authentication to prevent successful phishing attacks. Cloudflare's new Email Security feature blocks suspicious emails and disables keyboard inputs on untrusted websites, providing an extra layer of defense against phishing attacks. Overall, Cloudflare aims to build a better internet and offers various security solutions to protect against hackers and DDoS attacks.
#PhishingTrends #EmailSecurity #Cloudflare #softcorpremium
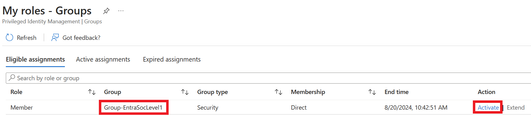
Configure Just-in-Time Access to M365 Defender
Microsoft's PIM for Groups Entra ID offers a feature called Privileged Identity Management (PIM) for Groups, which allows users to have just-in-time membership and ownership of groups. This feature enables users to govern access to various services by implementing policies such as approval enforcement, multi-factor authentication, justification requirements, and activation time limits. Additionally, Microsoft 365 Defender RBAC provides centralized permissions management for services like Defender for Endpoint, Identity, Cloud Apps, Office 365, and Vulnerability Management. The advantage of using the new M365 Defender RBAC is that it allows granting permissions to multiple services from a single role assignment. By combining PIM for Groups and M365 Defender RBAC, users can effectively manage access to Defender roles in a just-in-time manner. This solution can be beneficial for organizations looking for flexible and secure access to Microsoft 365 Defender.
#PrivilegedIdentityManagement #Microsoft365Defender #AccessManagement #softcorpremium
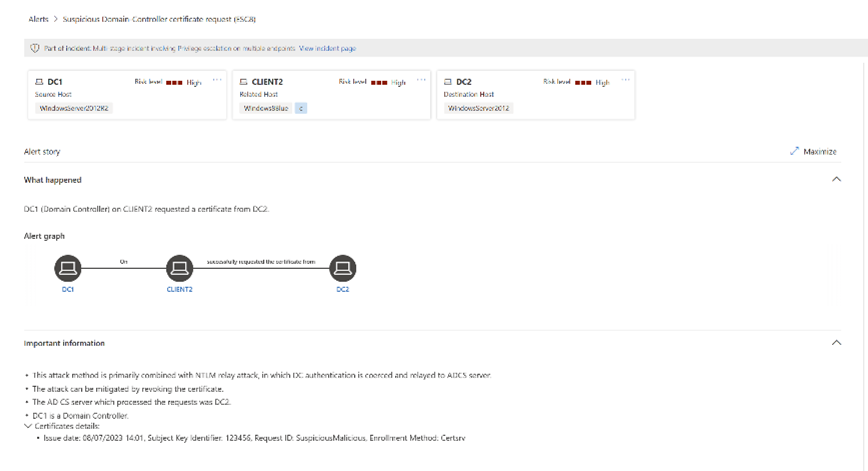
Microsoft Defender for Identity expands its coverage with new AD CS sensor! - Microsoft Community Hub
Microsoft has introduced a new sensor for Active Directory Certificate Services (AD CS) servers as part of their ongoing efforts to enhance security solutions. AD CS is a role in Windows Server that manages public key infrastructure certificates, which are crucial for secure communication and user authentication in Active Directory environments. However, the popularity of AD CS coupled with its potential vulnerabilities and misconfigurations make it an attractive target for attackers. The new sensor extends the capabilities of Microsoft Defender for Identity and provides enhanced detections and security recommendations. These include detecting suspicious certificate usage, tracking changes to audit configurations, monitoring deletion of certificate requests, and identifying modifications to AD CS settings. The upcoming security recommendations in Secure Score will help prevent arbitrary certificate requests, address misconfigured certificate templates, and enhance security for AD CS.
#MicrosoftSecurity #ADCSSecurity #EnhancedDetection #softcorpremium
Security Budgets - Supply and Demand
In a recent blog post, security expert Phil Venables discusses the often overlooked aspect of security budgets. He highlights that while risk quantification is often discussed, the operational planning and budgeting needed to run an enterprise-wide security program is rarely mentioned. Venables suggests thinking about security budgets in terms of supply and demand to be more efficient and commercial in resource allocation. He outlines strategies for balancing supply and demand, including redefining priorities, reducing demand through risk avoidance, increasing resource leverage, accepting risk deficits, and managing accumulated risk over time. Venables emphasizes the importance of approaching security budgeting as a risk management exercise and thinking commercially to reduce the ever-increasing security budget.
#SecurityBudgeting #RiskManagement #ResourceAllocation #softcorpremium
MDE Device Control – leveraging Reusable Settings in Intune - Microsoft Community Hub
Microsoft consultants Jorge Miguel Ferreira and Sebastian Werner have shared a blog post detailing how to set up Microsoft Defender for Endpoint (MDE) Device Control Removable Storage Access Control. The post focuses on using the new Attack Surface Reduction (ASR) rules in Intune to configure the feature. They cover various scenarios, including blocking write access to all removable storage for all users with exceptions for specific storage, blocking write access to removable storage for specific user groups on specific machines, blocking read and write access to specific devices, and blocking access to CD/DVDs. The post provides step-by-step instructions and troubleshooting information. Overall, it highlights the simplicity and extensive possibilities of configuring Device Control policies through Intune.
#MicrosoftDefenderforEndpoint #DeviceControl #softcorpremium
Azure VWAN and Private Endpoint Traffic Inspection – Findings | Journey Of The Geek
The author explores the topic of Azure VWAN and Private Endpoint Traffic Inspection, emphasizing the importance of strong security in the financial services industry. They discuss the use of Azure Private Endpoints and Azure Virtual WAN to achieve traffic inspection within internal network spaces. The author highlights the goal of VWAN to simplify networking management and setup. They also discuss the challenges and inconsistencies in Microsoft's documentation regarding SNAT requirements for traffic inspection. The author shares their own lab experiments and experiences with Azure Firewall and VPN connections. They mention the availability of new log features like Azure Firewall Flow Trace Log for troubleshooting asymmetric traffic. The author concludes by suggesting caution when using Azure Firewall due to potential performance issues and high billing costs, and recommends using SNAT until further clarification is received from Microsoft.
#AzureVWAN #TrafficInspection #NetworkingManagement #softcorpremium